msr2030路由器做内网一台设备映射
- 0关注
- 1收藏,1684浏览
问题描述:
msr2030做内网一台设备映射,ip192.168.169.166 端口6666—6666 10010—10130。从WEB里做好了能映射了,可是外网IP变动后不能自动更新,外部地址停在旧的IP。我是动态域名解释IP的
组网及组网描述:
- 2020-02-15提问
- 举报
-
(0)
最佳答案

看能不能用接口映射nat server protocol tcp global current-interface
- 2020-02-15回答
- 评论(37)
- 举报
-
(0)
是udP协议
命令上有udp的 nat server protocol upp global current-interface
直接把这条命令输进去么?
nat server protocol upp global current-interface 6666 inside 192.168.169.166 6666 命令行登录在外网口输入类似命令。另外是web页面的映射配置,看看有没有选择接口的也可以
[2630]int g0/0 [2630-GigabitEthernet0/0] upp global current-niterface 6666 inside 192.168 ^ % Unrecognized command found at '^' position. [2630-GigabitEthernet0/0].169.166
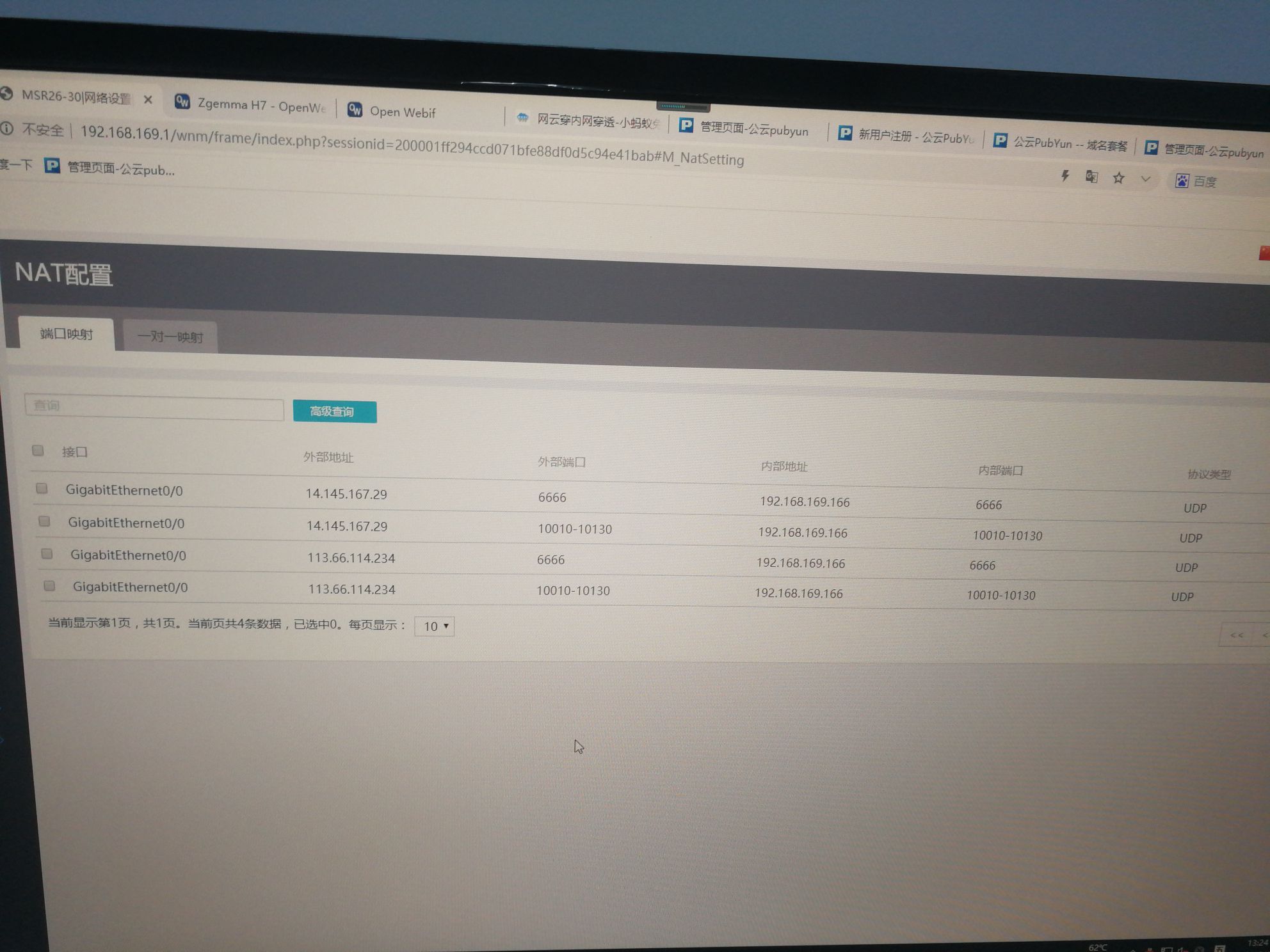
端口映射配置页面,外部地址看是否支持用当前接口,有的设备支持此功能
问号看看支持吗?如果支持是有current-interface参数的 nat server protocol udp global ? X.X.X.X Start global IP address current-interface Current interface interface Use the IP address of an interface as the global IP address
current-interface 代表此时接口获取的ip地址,如果ip地址变化,设备侧不用修改配置,外网用接口新ip一般就能访问了
端口映射配置页面,外部地址是设置用当前接口的,保存好后变成其他地址
dis ip int br看看接口实际的ip
实际IP202.105.58.195 ,NAT的外部地址还是停留在更新前的14.145.167.29
看看有实际ip能正常访问吗?
用实际ip能否正常访问
能访问的
那就可以,14那个条目应该之前配置残留的
我用当前接口地址IP重做一条映射,就可以访问到192.168.169.166这台设备了
只保留1条nat sever current-interface,其他临时删除删除,dis ip int br查看实际ip,用实际ip去访问,如果能正常访问就说明没问题了
弄错了,用实际IP也是访问不到192.168.169.166这台设备的,我在WEB里用当前接口地址IP重做一条映射,才可以访问到192.168.169.166这台设备。但是外网IP变动后就不能访问了!
外网口下display this看看有哪些配置
[2630-GigabitEthernet0/0]display this # interface GigabitEthernet0/0 port link-mode route description Multiple_Line nat outbound 3000 nat server protocol udp global current-interface 6666 inside 192.168.169.166 6666 pppoe-client dial-bundle-number 0 # return [2630-GigabitEthernet0/0]
将nat配置移动到PPPoE虚拟拨号口下看看能否正常 nat outbound 3000 nat server protocol udp global current-interface 6666 inside 192.168.169.166 6666
[2630-GigabitEthernet0/0]nat outbound 3000 nat server protocol udp global curren t-interface 6666 inside 192.168.169.166 6666 ^ % Too many parameters found at '^' position. [2630-GigabitEthernet0/0]
不是在这个介面输入吗
G口下的2行nat的配置临时移动到virtual-template或者是 dialer虚拟口下
不太明白,能不能做好命令我直接输入么?
1、将G0/0下2行nat的命令删除 2、dis cu查看是否有virtual-template或者是 dialer,如果有,进入接口视图下,配置 nat outbound 3000 nat server protocol udp global current-interface 6666 inside 192.168.169.166 6666 3、dis ip int br查看实际ip,用实际ip去访问,如果能正常访问就说明没问题了
[2630]int g 0/0 [2630-GigabitEthernet0/0]nat outbound 3000 [2630-GigabitEthernet0/0]nat server protocol udp global current-interface 6666 i nside 192.168.169.166 6666 [2630-GigabitEthernet0/0]
这两条正常输入了
上面2条配置是配置在虚拟拨号口下的,dis cu(一直按空格刷新)查看是否有virtual-template或者是 dialer
[2630]dis cu # version 7.1.064, Release 0615P16 # sysname 2630 # telnet server enable # track 1 nqa entry admin ipsec reaction 1 # ip pool l2tp22 192.168.3.100 192.168.3.200 ip pool l2tp22 gateway 192.168.3.1 # dialer-group 1 rule ip permit # dhcp enable # dns server 115.144.122.193 dns server 115.144.122.194 # password-recovery enable # vlan 1 # traffic classifier 1 operator and if-match acl 3100 # traffic behavior 1 filter permit # qos policy 1 classifier 1 behavior 1 # dhcp server ip-pool 169 gateway-list 192.168.169.1 network 192.168.169.0 mask 255.255.255.0 dns-list 114.114.114.114 # ddns policy GigabitEthernet0/0 url ***.***/dyndns/update?system=dyndns&hostname=<h>&myip=<a> username gzyxfb password cipher $c$3$rt6rvXDD5Co4POLvWW8mvwoxFDXcaT1mEIch # nqa entry ipsec ipsec type icmp-echo destination ip 192.168.0.1 frequency 300000 probe count 2 probe timeout 50000 source ip 192.168.169.1 # nqa entry ipsec1 ipsec1 type icmp-echo destination ip 192.168.6.1 frequency 300000 probe count 2 probe timeout 50000 source ip 192.168.169.1 # nqa entry ipsec2 ipsec2 type icmp-echo destination ip 192.168.20.1 frequency 300000 probe count 2 probe timeout 50000 source ip 192.168.3.1 # nqa entry ipsec3 ipsec3 type icmp-echo destination ip 192.168.6.1 frequency 300000 probe count 2 probe timeout 50000 source ip 192.168.3.1 # nqa schedule ipsec ipsec start-time now lifetime forever nqa schedule ipsec1 ipsec1 start-time now lifetime forever nqa schedule ipsec2 ipsec2 start-time now lifetime forever nqa schedule ipsec3 ipsec3 start-time now lifetime forever # controller Cellular0/0 # interface Aux0 # interface Dialer0 mtu 1492 ppp chap password cipher $c$3$5mW6LRTObj+AI3tmOYggzxOQUwIRc1wh1M/8 ppp chap user 02005298327@163.gd ppp ipcp dns admit-any ppp ipcp dns request ppp pap local-user 02005298327@163.gd password cipher $c$3$3GPrqu7IQzCNHumL+66nchQugGt/7g8Ht4HC dialer bundle enable dialer-group 1 dialer timer idle 0 dialer timer autodial 5 ip address ppp-negotiate tcp mss 1024 qos apply policy 1 inbound nat outbound 3000 nat server protocol udp global 14.145.167.29 6666 inside 192.168.169.166 6666 nat server protocol udp global 14.145.167.29 10010 10130 inside 192.168.169.166 10010 10130 ddns apply policy GigabitEthernet0/0 fqdn ***.*** ipsec apply policy server # interface Dialer1 # interface Virtual-Template0 # interface Virtual-Template1 ppp authentication-mode chap domain system remote address pool l2tp22 ip address 192.168.3.1 255.255.255.0 # interface NULL0 # interface GigabitEthernet0/0 port link-mode route description Multiple_Line nat outbound 3000 nat server protocol udp global current-interface 6666 inside 192.168.169.166 6666 pppoe-client dial-bundle-number 0 # interface GigabitEthernet0/1 port link-mode route ip address 192.168.169.1 255.255.255.0 undo dhcp select server # security-zone name Local # security-zone name Trust # security-zone name DMZ # security-zone name Untrust # security-zone name Management # scheduler logfile size 16 # line class aux user-role network-admin # line class tty user-role network-operator # line class usb user-role network-admin # line class vty user-role network-operator # line aux 0 user-role network-admin # line vty 0 4 authentication-mode scheme user-role network-admin user-role network-operator # line vty 5 63 user-role network-operator # ip route-static 0.0.0.0 0 Dialer0 # acl advanced 3000 rule 0 deny ip destination 192.168.1.0 0.0.0.255 rule 5 deny ip destination 192.168.0.0 0.0.0.255 rule 10 deny ip destination 192.168.9.0 0.0.0.255 rule 11 deny ip destination 192.168.30.0 0.0.0.255 rule 15 deny ip destination 192.168.10.0 0.0.0.255 rule 16 deny ip destination 192.168.8.0 0.0.0.255 rule 17 deny ip destination 192.168.6.0 0.0.0.255 rule 18 deny ip destination 192.168.20.0 0.0.0.255 rule 20 permit ip # acl advanced 3100 rule 0 permit ip source 192.168.169.151 0 destination 192.168.8.2 0 # acl advanced 3200 rule 0 permit ip source 192.168.169.0 0.0.0.255 destination 192.168.0.0 0.0.0.255 # domain system authentication ppp local # domain default enable system # role name level-0 description Predefined level-0 role # role name level-1 description Predefined level-1 role # role name level-2 description Predefined level-2 role # role name level-3 description Predefined level-3 role # role name level-4 description Predefined level-4 role # role name level-5 description Predefined level-5 role # role name level-6 description Predefined level-6 role # role name level-7 description Predefined level-7 role # role name level-8 description Predefined level-8 role # role name level-9 description Predefined level-9 role # role name level-10 description Predefined level-10 role # role name level-11 description Predefined level-11 role # role name level-12 description Predefined level-12 role # role name level-13 description Predefined level-13 role # role name level-14 description Predefined level-14 role # user-group system # local-user admin class manage password hash $h$6$ccjLjXAe6I90r+c8$bNsbPDeSYgYo/ptQKrW5Lr46/+uqj3rG94FiTas8vHOfyHEpAQnojphADtCUNb8dbjuG93hJSCEImPxX01EgtQ== service-type telnet http https authorization-attribute user-role network-admin authorization-attribute user-role network-operator # local-user test class network password cipher $c$3$/qiA+bWs804BNRyPUST4SbGIakBhR1/O5RojZg== service-type ppp authorization-attribute user-role network-operator # ipsec transform-set 1 encapsulation-mode transport esp encryption-algorithm 3des-cbc esp authentication-algorithm md5 # ipsec transform-set 2 encapsulation-mode transport esp encryption-algorithm aes-cbc-128 esp authentication-algorithm sha1 # ipsec transform-set 3 encapsulation-mode transport esp encryption-algorithm aes-cbc-256 esp authentication-algorithm sha1 # ipsec transform-set 4 encapsulation-mode transport esp encryption-algorithm des-cbc esp authentication-algorithm sha1 # ipsec transform-set 5 encapsulation-mode transport esp encryption-algorithm 3des-cbc esp authentication-algorithm sha1 # ipsec transform-set 6 encapsulation-mode transport esp encryption-algorithm aes-cbc-192 esp authentication-algorithm sha1 # ipsec transform-set server esp encryption-algorithm aes-cbc-256 esp authentication-algorithm md5 pfs dh-group2 # ipsec policy-template 1 1 transform-set 1 2 3 4 5 6 ike-profile 1 # ipsec policy-template server 65533 transform-set server ike-profile server1 sa duration time-based 3600 sa duration traffic-based 1843200 # ipsec policy-template server 65534 transform-set server ike-profile server sa duration time-based 3600 sa duration traffic-based 1843200 # ipsec policy server 1 isakmp template 1 # ipsec policy server 65534 isakmp template server # l2tp-group 1 mode lns allow l2tp virtual-template 1 undo tunnel authentication tunnel name LNS # l2tp enable # ike dpd interval 10 on-demand ike identity fqdn 1 # ike profile 1 keychain server exchange-mode aggressive local-identity address 192.168.3.1 match remote identity address 0.0.0.0 0.0.0.0 proposal 1 2 3 4 5 6 # ike profile server keychain server exchange-mode aggressive local-identity fqdn 1 match remote identity fqdn 2 proposal 65534 # ike profile server1 keychain server exchange-mode aggressive local-identity fqdn 1 match remote identity fqdn 3 proposal 65534 # ike proposal 1 encryption-algorithm aes-cbc-128 dh group2 authentication-algorithm md5 # ike proposal 2 encryption-algorithm 3des-cbc dh group2 authentication-algorithm md5 # ike proposal 3 encryption-algorithm 3des-cbc dh group2 # ike proposal 4 encryption-algorithm aes-cbc-256 dh group2 # ike proposal 5 dh group2 # ike proposal 6 encryption-algorithm aes-cbc-192 dh group2 # ike proposal 65534 encryption-algorithm aes-cbc-256 dh group2 authentication-algorithm md5 # ike keychain 1 pre-shared-key hostname phone key cipher $c$3$CYMkMBMg19SXP6ZT+axVsC85RAglJc6UxA== # ike keychain server pre-shared-key address 0.0.0.0 0.0.0.0 key cipher $c$3$U1fAED/f5H+GG1HLC6eme0BecjK5cpuAag== # ip http enable ip https enable # wlan global-configuration # wlan ap-group default-group # cloud-management server domain oasis.h3c.com # return [2630]
dialer bundle enable dialer-group 1 dialer timer idle 0 dialer timer autodial 5 ip address ppp-negotiate tcp mss 1024 qos apply policy 1 inbound nat outbound 3000 nat server protocol udp global 14.145.167.29 6666 inside 192.168.169.166 6666 nat server protocol udp global 14.145.167.29 10010 10130 inside 192.168.169.166 10010 10130 ddns apply policy GigabitEthernet0/0 fqdn ***.***
interface Dialer0 下配置nat outbound 3000 nat server protocol udp global current-interface 6666 inside 192.168.169.166 6666 ,如果还不行可以问问代理商
interface virtual-tem 也配置下试试
端口6666的可以了,还有端口10010-10130怎么加上去
端口替换下 nat server protocol udp global current-interface 10010 10130 inside 192.168.169.166 10010 10130


- 2020-02-15回答
- 评论(1)
- 举报
-
(0)
端口映射配置页面,外部地址看是否支持用当前接口,有的设备支持此功能
端口映射配置页面,外部地址看是否支持用当前接口,有的设备支持此功能


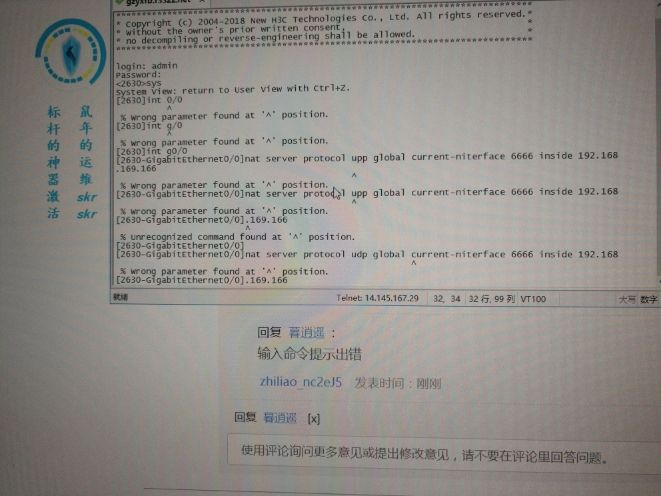 输入命令提示
输入命令提示
- 2020-02-15回答
- 评论(1)
- 举报
-
(0)
问号看看支持吗?如果支持是有current-interface参数的 nat server protocol udp global ? X.X.X.X Start global IP address current-interface Current interface interface Use the IP address of an interface as the global IP address
问号看看支持吗?如果支持是有current-interface参数的 nat server protocol udp global ? X.X.X.X Start global IP address current-interface Current interface interface Use the IP address of an interface as the global IP address
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明
端口替换下 nat server protocol udp global current-interface 10010 10130 inside 192.168.169.166 10010 10130