问题描述:
今天配置F100-C-AC2防火墙,配完在securecrt中一直提示以下信息:
%Jan 1 00:09:55:006 2000 H3C SEC/4/ATCKDF:atckType(1016)=(21)ARP-spoofing;rcvIfName(1023)=Ethernet0/4;srcIPAddr(1017)=10.0.0.254;srcMacAddr(1021)=0c-2c-54-c1-11-1c;destIPAddr(1019)=10.0.0.1;destMacAddr(1022)=c4-ca-d9-35-64-81;atckSpeed(1047)=0;atckTime_cn(1048)=20000101000948
%Jan 1 00:09:55:008 2000 H3C SEC/4/ATCKDF:atckType(1016)=(21)ARP-spoofing;rcvIfName(1023)=Ethernet0/4;srcIPAddr(1017)=10.0.0.254;srcMacAddr(1021)=0c-2c-54-c1-11-1c;destIPAddr(1019)=10.0.0.1;destMacAddr(1022)=c4-ca-d9-35-64-81;atckSpeed(1047)=0;atckTime_cn(1048)=20000101000949
%Jan 1 00:09:55:010 2000 H3C SEC/4/ATCKDF:atckType(1016)=(21)ARP-spoofing;rcvIfName(1023)=Ethernet0/4;srcIPAddr(1017)=10.0.0.254;srcMacAddr(1021)=0c-2c-54-c1-11-1c;destIPAddr(1019)=10.0.0.1;destMacAddr(1022)=c4-ca-d9-35-64-81;atckSpeed(1047)=0;atckTime_cn(1048)=20000101000950
%Jan 1 00:10:55:010 2000 H3C SEC/4/ATCKDF:atckType(1016)=(21)ARP-spoofing;rcvIfName(1023)=Ethernet0/4;srcIPAddr(1017)=10.0.0.254;srcMacAddr(1021)=0c-2c-54-c1-11-1c;destIPAddr(1019)=10.0.0.1;destMacAddr(1022)=c4-ca-d9-35-64-81;atckSpeed(1047)=0;atckTime_cn(1048)=20000101001039
%Jan 1 00:10:55:013 2000 H3C SEC/4/ATCKDF:atckType(1016)=(21)ARP-spoofing;rcvIfName(1023)=Ethernet0/4;srcIPAddr(1017)=10.0.0.254;srcMacAddr(1021)=0c-2c-54-c1-11-1c;destIPAddr(1019)=10.0.0.1;destMacAddr(1022)=c4-ca-d9-35-64-81;atckSpeed(1047)=0;atckTime_cn(1048)=20000101001040
%Jan 1 00:10:55:014 2000 H3C SEC/4/ATCKDF:atckType(1016)=(21)ARP-spoofing;rcvIfName(1023)=Ethernet0/4;srcIPAddr(1017)=10.0.0.254;srcMacAddr(1021)=0c-2c-54-c1-11-1c;destIPAddr(1019)=10.0.0.1;destMacAddr(1022)=c4-ca-d9-35-64-81;atckSpeed(1047)=0;atckTime_cn(1048)=20000101001041
请问这是什么问题导致的?我是哪里没有配置好吗?
组网及组网描述:
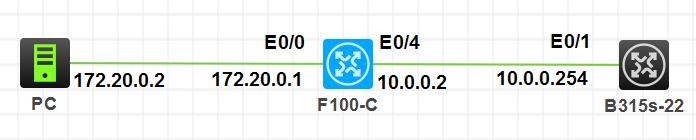
上图是网络拓扑图,下面是我的配置信息:
# sysname H3C
# firewall packet-filter enable firewall packet-filter default permit
# insulate
# firewall url-filter host enable
# nat address-group 0 10.0.0.3 10.0.0.100
# firewall statistic system enable
# firewall mac-binding enable firewall mac-binding 10.0.0.1 c4ca-d935-6481 firewall mac-binding 10.0.0.254 0c2c-54c1-111c
# radius scheme system server-type extended
# domain system
# local-user admin password cipher 123456 service-type telnet level 3
# dhcp server ip-pool 0 network 172.20.0.0 mask 255.255.0.0 gateway-list 172.20.0.1 dns-list 172.20.0.1 10.0.0.254
# acl number 2000 rule 0 permit source 172.20.0.0 0.0.255.255
# interface Aux0 async mode flow
# interface Ethernet0/0 speed 100 duplex full description WCN_INTERFACE_LAN ip address 172.20.0.1 255.255.0.0 firewall packet-filter 3003 inbound
# interface Ethernet0/1 description WCN_INTERFACE_LAN firewall packet-filter 3003 inbound
# interface Ethernet0/2 description WCN_INTERFACE_LAN firewall packet-filter 3003 inbound
# interface Ethernet0/3 description WCN_INTERFACE_LAN firewall packet-filter 3003 inbound
# interface Ethernet0/4 speed 100 duplex full description WCN_INTERFACE_WAN ip address 10.0.0.1 255.255.255.0 firewall packet-filter 3002 inbound nat outbound static nat outbound 2000 nat server protocol tcp global 10.0.0.111 www inside 172.20.0.2 www
# interface Encrypt1/0
# interface NULL0
# firewall zone local set priority 100
# firewall zone trust add interface Ethernet0/0 set priority 85
# firewall zone untrust add interface Ethernet0/4 set priority 5
# firewall zone DMZ set priority 50
# firewall interzone local trust
# firewall interzone local untrust
# firewall interzone local DMZ
# firewall interzone trust untrust
# firewall interzone trust DMZ
# firewall interzone DMZ untrust
# ip route-static 0.0.0.0 0.0.0.0 10.0.0.254 preference 60
# firewall defend ip-spoofing
firewall defend land
firewall defend smurf
firewall defend fraggle
firewall defend winnuke
firewall defend icmp-redirect
firewall defend icmp-unreachable
firewall defend source-route
firewall defend route-record
firewall defend tracert
firewall defend ping-of-death
firewall defend tcp-flag
firewall defend ip-fragment
firewall defend large-icmp
firewall defend teardrop
firewall defend ip-sweep
firewall defend port-scan
firewall defend arp-spoofing
firewall defend arp-flood
firewall defend frag-flood
firewall defend syn-flood enable
firewall defend udp-flood enable
firewall defend icmp-flood enable
# user-interface con 0 user-interface aux 0 user-interface vty 0 4 authentication-mode scheme user privilege level 3
# return
- 2020-09-13提问
- 举报
-
(0)
最佳答案

6.1.8 firewall defend arp-spoofing
【命令】
firewall defend arp-spoofing
undo firewall defend arp-spoofing
【视图】
系统视图
【参数】
无
【描述】
firewall defend arp-spoofing命令用来打开ARP欺骗攻击防范功能,undo firewall defend arp-spoofing命令用来关闭ARP欺骗攻击防范功能。
缺省情况下,关闭ARP欺骗攻击防范功能。
【举例】
# 打开ARP欺骗攻击防范功能。
[H3C] firewall defend arp-spoofing
这个命令产生的日志
- 2020-09-13回答
- 评论(1)
- 举报
-
(0)
也就是说一切是正常的,直接把这个arp-spoofing关闭就可以了,对吗?


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明

也就是说一切是正常的,直接把这个arp-spoofing关闭就可以了,对吗?