DHCP option82属性实现固定接口获取固定地址
- 0关注
- 8收藏 4759浏览
组网及说明
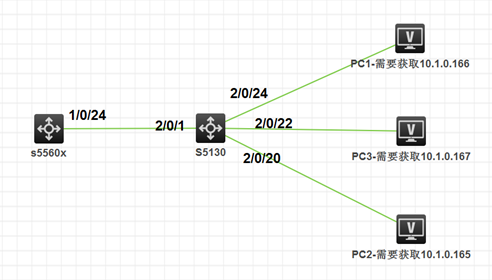
S5130为网关,做DHCP中继,S5560X为DHCP服务器
问题描述
需求:
S5130为网关,做DHCP中继,S5560X为DHCP服务器,需要实现PC接入S5130的2/0/20只能获取到10.1.0.165,接入2/0/22只能获取到地址10.1.0.167,接入2/0/24只能获取到地址10.1.0.166。
过程分析
需要使用option82来实现关联
解决方法
S5560关键配置:
dhcp enable
#
dhcp server relay information enable //设备默认开启处理option 82
#
vlan 10
#
vlan 206
#
dhcp class 6port38
if-match rule 1 option 82 hex 36706f72743338 partial //模糊匹配
#
dhcp class 6port39
if-match rule 1 option 82 hex 36706f72743339 offset 2 length 7 //精确匹配,与partial功能一致,但是对接其他厂商或者不通芯片可能不一致,需要抓包明确
#
dhcp class 6port37
if-match rule 1 option 82 hex 36706f72743337 offset 2 length 7
#
dhcp server ip-pool vlan206
gateway-list 10.1.0.1
network 10.1.0.0 mask 255.255.255.0
class 6port38 range 10.1.0.166 10.1.0.166
class 6port39 range 10.1.0.167 10.1.0.167
class 6port37 range 10.1.0.165 10.1.0.165
#
interface Vlan-interface10
ip address 1.1.1.1 255.255.255.0
#
interface Vlan-interface206
#
interface GigabitEthernet1/0/24
port link-mode bridge
port link-type trunk
port trunk permit vlan all
mirroring-group 1 mirroring-port both
#
ip route-static 0.0.0.0 0 1.1.1.2
#
S5130关键配置:
dhcp enable
#
dhcp snooping enable
#
#
vlan 10
#
vlan 206
#
interface Vlan-interface10
ip address 1.1.1.2 255.255.255.0
#
interface Vlan-interface206
ip address 10.1.0.1 255.255.255.0
dhcp select relay
dhcp relay server-address 1.1.1.1
#
interface GigabitEthernet2/0/1
port link-type trunk
port trunk permit vlan all
dhcp snooping trust
#
interface GigabitEthernet2/0/24
port access vlan 206
dhcp snooping information enable
dhcp snooping information circuit-id string 6port38
#
interface GigabitEthernet2/0/22
port access vlan 206
dhcp snooping information enable
dhcp snooping information circuit-id string 6port39
#
interface GigabitEthernet2/0/20
port access vlan 206
dhcp snooping information enable
dhcp snooping information circuit-id string 6port37
#
ip route-static 0.0.0.0 0 1.1.1.1
#
将PC接入S5130的2/0/22上测试:
在S5560的1/0/24接口抓包如下,获取到指定地址:
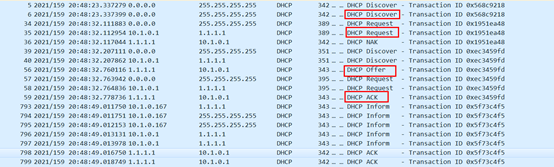
终端在发送request请求时,在S5130的2/0/22接口添加了option82属性,携带字段为“6port39”由网关中继发送到dhcp服务器上。
#
interface GigabitEthernet2/0/22
port access vlan 206
dhcp snooping information enable //开启option82功能
dhcp snooping information circuit-id string 6port39 //携带字段
#
S5560作为DHCP服务器,处理并识别option82字段,通过class做匹配,dhcp class中设置的字段与客户端发送上来的字段校验一致,则通过dhcp地址池中的class与地址范围做关联,地址范围最大最小只有一个,实现只获取固定地址的需求。
#
dhcp server relay information enable //设备默认开启处理option 82
#
dhcp class 6port39
if-match rule 1 option 82 hex 36706f72743339 offset 2 length 7
#
dhcp server ip-pool vlan206
gateway-list 10.1.0.1
network 10.1.0.0 mask 255.255.255.0
class 6port38 range 10.1.0.166 10.1.0.166
class 6port39 range 10.1.0.167 10.1.0.167
class 6port37 range 10.1.0.165 10.1.0.165
#
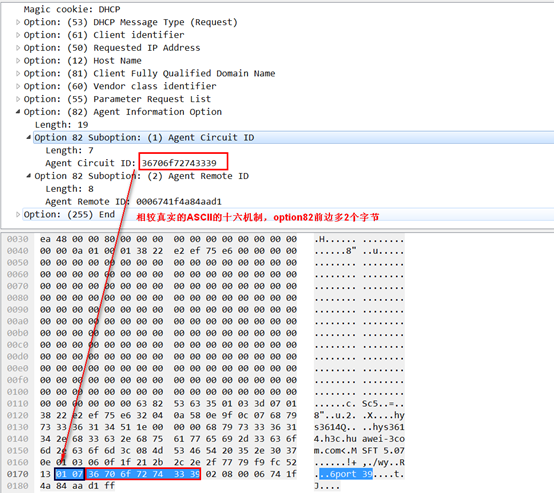
关于如何通过dhcp class中的字段与option82中字段的校验,有两种:
方式一:使用“partial”进行模糊匹配,拿咱们自己设置的hex字段去喝客户端请求带上来的option82对比,只要option82里边包含这个字段,即视为匹配,if-match rule 1 option 82 hex 36706f72743339 partial
方法二:使用偏移量精确匹配,如下这个命令,逻辑为在客户端请求的option82中,从offset+1开始,到offset+length范围的字符摘出来与下边手动学的hex字段对比,一致即关联。(下边这个命令就是找了option82中的3-9字符,共7个字符)
if-match rule 1 option 82 hex 36706f72743339 offset 2 length 7
Debug如下:
*Jan 1 02:27:37:423 2013 S5560 DHCPS/7/PACKET: From 10.1.0.1 port 67, interface Vlan-interface10
Message type: REQUEST (1)
Hardware type: 1, Hardware address length: 6
Hops: 1, Transaction ID: 3962853885
Seconds: 0, Broadcast flag: 1
Client IP address: 0.0.0.0 Your IP address: 0.0.0.0
Server IP address: 0.0.0.0 Relay agent IP address: 10.1.0.1
Client hardware address: 3822-e2ef-75e6
Server host name: not configured
Boot file name: not configured
DHCP message type: DHCPDISCOVER (1)
*Jan 1 02:27:37:423 2013 S5560 DHCPS/7/EVENT: Receive a DHCPDISCOVER message from 10.1.0.1.
*Jan 1 02:27:37:424 2013 S5560 DHCPS/7/EVENT: Send an ICMP echo request to 10.1.0.167.
*Jan 1 02:27:37:973 2013 S5560 DHCPS/7/EVENT: Send a DHCPOFFER message on 10.1.0.1.
*Jan 1 02:27:37:975 2013 S5560 DHCPS/7/PACKET: To 10.1.0.1 port 67, interface is selected by routing table
Message type: REPLY (2)
Hardware type: 1, Hardware address length: 6
Hops: 1, Transaction ID: 3962853885
Seconds: 0, Broadcast flag: 1
Client IP address: 0.0.0.0 Your IP address: 10.1.0.167
Server IP address: 0.0.0.0 Relay agent IP address: 10.1.0.1
Client hardware address: 3822-e2ef-75e6
Server host name: not configured
Boot file name: not configured
DHCP message type: DHCPOFFER (2)
*Jan 1 02:27:37:980 2013 S5560 DHCPS/7/PACKET: From 10.1.0.1 port 67, interface Vlan-interface10
Message type: REQUEST (1)
Hardware type: 1, Hardware address length: 6
Hops: 1, Transaction ID: 3962853885
Seconds: 0, Broadcast flag: 1
Client IP address: 0.0.0.0 Your IP address: 0.0.0.0
Server IP address: 0.0.0.0 Relay agent IP address: 10.1.0.1
Client hardware address: 3822-e2ef-75e6
Server host name: not configured
Boot file name: not configured
DHCP message type: DHCPREQUEST (3)
*Jan 1 02:27:37:980 2013 S5560 DHCPS/7/EVENT: Receive a DHCPREQUEST message for 10.1.0.167 from 10.1.0.1; The server identifier is 1.1.1.1.
*Jan 1 02:27:37:981 2013 S5560 DHCPS/7/EVENT: The client selected the local server.
*Jan 1 02:27:37:992 2013 S5560 DHCPS/7/EVENT: Send a DHCPACK message on 10.1.0.1.
*Jan 1 02:27:37:992 2013 S5560 DHCPS/7/PACKET: To 10.1.0.1 port 67, interface is selected by routing table
Message type: REPLY (2)
Hardware type: 1, Hardware address length: 6
Hops: 1, Transaction ID: 3962853885
Seconds: 0, Broadcast flag: 1
Client IP address: 0.0.0.0 Your IP address: 10.1.0.167
Server IP address: 0.0.0.0 Relay agent IP address: 10.1.0.1
Client hardware address: 3822-e2ef-75e6
Server host name: not configured
Boot file name: not configured
DHCP message type: DHCPACK (5)
*Jan 1 02:27:54:228 2013 S5560 DHCPS/7/PACKET: From 10.1.0.167 port 68, interface Vlan-interface10
Message type: REQUEST (1)
Hardware type: 1, Hardware address length: 6
Hops: 0, Transaction ID: 1601422581
Seconds: 0, Broadcast flag: 0
Client IP address: 10.1.0.167 Your IP address: 0.0.0.0
Server IP address: 0.0.0.0 Relay agent IP address: 0.0.0.0
Client hardware address: 3822-e2ef-75e6
Server host name: not configured
Boot file name: not configured
DHCP message type: DHCPINFORM (8)
*Jan 1 02:27:54:228 2013 S5560 DHCPS/7/EVENT: Receive a DHCPINFORM message from Vlan-interface10.
*Jan 1 02:27:54:228 2013 S5560 DHCPS/7/EVENT: No matching network for the client.
*Jan 1 02:27:54:230 2013 S5560 DHCPS/7/PACKET: From 10.1.0.1 port 67, interface Vlan-interface10
Message type: REQUEST (1)
Hardware type: 1, Hardware address length: 6
Hops: 1, Transaction ID: 1601422581
Seconds: 0, Broadcast flag: 0
Client IP address: 10.1.0.167 Your IP address: 0.0.0.0
Server IP address: 0.0.0.0 Relay agent IP address: 10.1.0.1
Client hardware address: 3822-e2ef-75e6
Server host name: not configured
Boot file name: not configured
DHCP message type: DHCPINFORM (8)
*Jan 1 02:27:54:230 2013 S5560 DHCPS/7/EVENT: Receive a DHCPINFORM message from 10.1.0.1.
*Jan 1 02:27:54:231 2013 S5560 DHCPS/7/EVENT: Sent DHCPACK to 10.1.0.1.
*Jan 1 02:27:54:232 2013 S5560 DHCPS/7/PACKET: To 10.1.0.1 port 67, interface Vlan-interface10
Message type: REPLY (2)
Hardware type: 1, Hardware address length: 6
Hops: 1, Transaction ID: 1601422581
Seconds: 0, Broadcast flag: 1
Client IP address: 10.1.0.167 Your IP address: 0.0.0.0
Server IP address: 0.0.0.0 Relay agent IP address: 10.1.0.1
Client hardware address: 3822-e2ef-75e6
Server host name: not configured
Boot file name: not configured
DHCP message type: DHCPACK (5)
*Jan 1 02:27:54:233 2013 S5560 DHCPS/7/PACKET: From 10.1.0.1 port 67, interface Vlan-interface10
Message type: REQUEST (1)
Hardware type: 1, Hardware address length: 6
Hops: 1, Transaction ID: 1601422581
Seconds: 0, Broadcast flag: 0
Client IP address: 1.1.1.2 Your IP address: 0.0.0.0
Server IP address: 0.0.0.0 Relay agent IP address: 10.1.0.1
Client hardware address: 0800-2700-acc0
Server host name: not configured
Boot file name: not configured
DHCP message type: DHCPINFORM (8)
*Jan 1 02:27:54:233 2013 S5560 DHCPS/7/EVENT: Receive a DHCPINFORM message from 10.1.0.1.
*Jan 1 02:27:54:233 2013 S5560 DHCPS/7/EVENT: Sent DHCPACK to 10.1.0.1.
*Jan 1 02:27:54:234 2013 S5560 DHCPS/7/PACKET: To 10.1.0.1 port 67, interface Vlan-interface10
Message type: REPLY (2)
Hardware type: 1, Hardware address length: 6
Hops: 1, Transaction ID: 1601422581
Seconds: 0, Broadcast flag: 1
Client IP address: 1.1.1.2 Your IP address: 0.0.0.0
Server IP address: 0.0.0.0 Relay agent IP address: 10.1.0.1
Client hardware address: 0800-2700-acc0
Server host name: not configured
Boot file name: not configured
DHCP message type: DHCPACK (5)
- 附件下载: option82抓包存档.rar
- 2021-06-08 发表
- 举报
- 导出案例(pdf)
- 导出案例(word)
-
(0)
该案例对您是否有帮助:
您的评价:1
若您有关于案例的建议,请反馈:
该案例暂时没有网友评论
编辑评论
✖
案例意见反馈


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
