V7防火墙 L2TP OVER IPSEC 与iNode进行对接
- 1关注
详细介绍如图:PC为分部电脑,通过路由器接入ISP,总部为一台防火墙配置L2TP OVER IPSEC 。现需要PC通过iNode客户端拨入总部,与服务器进行互访。 附件为我做的原版配置 配置同时可以适用Windows 系统VPN及手机VPN
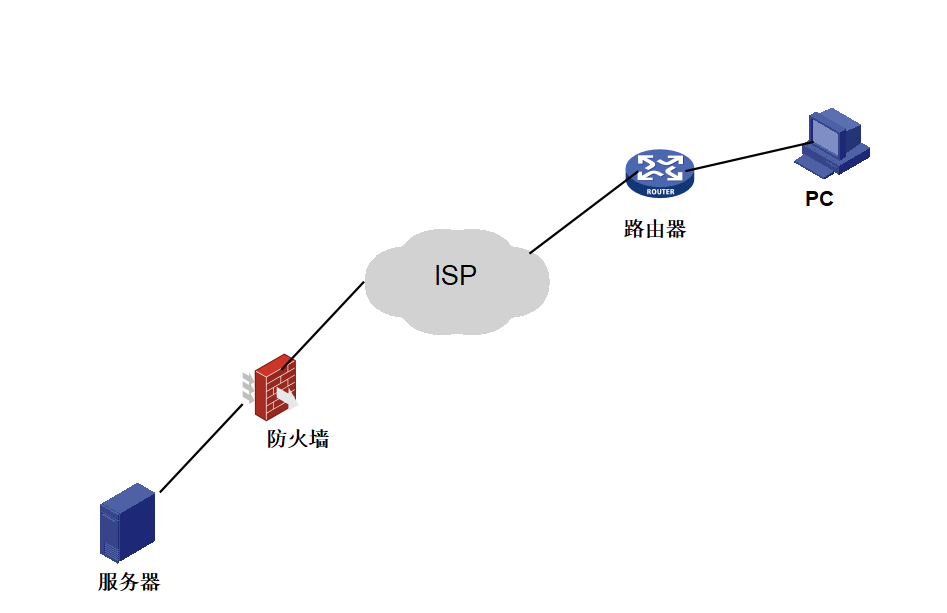
详细配置如下
version 7.1.064, Release 9510P05
#
sysname H3C
#
context Admin id 1
#
telnet server enable
#
irf mac-address persistent timer
irf auto-update enable
undo irf link-delay
irf member 2 priority 1
#
ip pool pool 10.1.1.2 10.1.1.10 (创建虚服务模板的地址池,暨用户拨号获取的IP)
#
dialer-group 1 rule ip permit
#
ip unreachables enable ip ttl-expires enable
#
password-recovery enable
# vlan 1
#
interface Virtual-Template1
ppp authentication-mode
pap remote address pool pool
ip address 10.1.1.1 255.255.255.0
#
object-policy ip 1
rule 0 pass
#
security-zone name Local
#
security-zone name Trust (将端口加入安全区域)
import interface GigabitEthernet2/0/4
import interface Virtual-Template1
#
security-zone name DMZ
#
security-zone name Untrust (将端口加入安全区域)
import interface GigabitEthernet2/0/3 (三口设置为外网口连接ISP)
#
security-zone name Management (将端口加入安全区域)
import interface GigabitEthernet2/0/0
import interface GigabitEthernet2/0/2
#
zone-pair security source Any destination Any (设置安全策略)
object-policy apply ip 1
#
zone-pair security source Any destination Local (设置安全策略)
object-policy apply ip 1
#
zone-pair security source Local destination Any (设置安全策略)
object-policy apply ip 1
#
zone-pair security source Trust destination Trust (设置安全策略)
object-policy apply ip 1
#
zone-pair security source Trust destination Untrust (设置安全策略)
object-policy apply ip 1
#
zone-pair security source Untrust destination Trust (设置安全策略)
object-policy apply ip 1
#
local-user 1 class network (创建PPP用户,用户名为1 密码为1)
password cipher $c$3$Slq/njg/1L0tpkyLJTxtoEW3VsM=
service-type ppp
authorization-attribute user-role network-operator
#
#
ipsec transform-set 1 (设置IPSEC参数)
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
#
ipsec transform-set 2 (设置IPSEC参数)
esp encryption-algorithm aes-cbc-128
esp authentication-algorithm sha1
#
ipsec transform-set 3 (设置IPSEC参数)
esp encryption-algorithm aes-cbc-256
esp authentication-algorithm sha1
#
ipsec transform-set 4
esp encryption-algorithm des-cbc
esp authentication-algorithm sha1
#
ipsec transform-set 5
esp encryption-algorithm 3des-cbc
esp authentication-algorithm sha1
#
ipsec transform-set 6
esp encryption-algorithm aes-cbc-192
esp authentication-algorithm sha1
#
ipsec policy-template 1 1 (创建IPSEC策略将参数进行绑定)
transform-set 1 2 3 4 5 6
ike-profile 1
#
ipsec policy 1 1 isakmp template 1 (IPSEC 策略与 模板1进行绑定)
#
l2tp-group 1 mode lns (设置L2TP参数 将本端命名为lns)
allow l2tp virtual-template 1
undo tunnel authentication
tunnel name lns
#
l2tp enable
#
ike identity fqdn 123 (设置本端IKE FQDN号为123)
#
#
ike profile 1
keychain 1
exchange-mode aggressive
local-identity fqdn 123 match remote identity address 0.0.0.0 0.0.0.0 (设置远端接入的IP为全部都可以接入)
match remote identity fqdn 456 (设置对端FQDN号为456)
proposal 1 2 3 4 5 6 (绑定IKE的提要)
#
ike proposal 1
encryption-algorithm aes-cbc-128
dh group2
authentication-algorithm md5
#
ike proposal 2
encryption-algorithm 3des-cbc
dh group2
authentication-algorithm md5
#
ike proposal 3
encryption-algorithm 3des-cbc
dh group2
#
ike proposal 4
encryption-algorithm aes-cbc-256
dh group2
#
ike proposal 5
dh group2
#
ike proposal 6
encryption-algorithm aes-cbc-192
dh group2
#
ike keychain 1 pre-shared-key hostname 456 key cipher $c$3$7ingFDpILKQhQ8DxrvyuG6m2AyO2K1nW9Q== (设置IKE的密钥为aabbcc)
#
ip https enable
webui log enable
#
interface GigabitEthernet2/0/3
port link-mode route
ipsec apply policy 1
(配置公网IP)
nat out (配置NAT)
#
ip route-static 0.0.0.0 0 公网网关 (设置缺省路由)
#
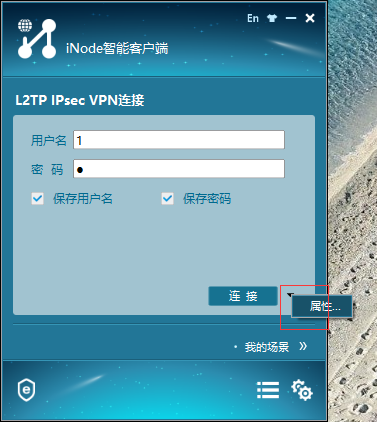
iNode 配置
(输入用户名密码 均为1 点击属性)
LNS服务器为防火墙外网口IP
预共享秘钥为aabbcc
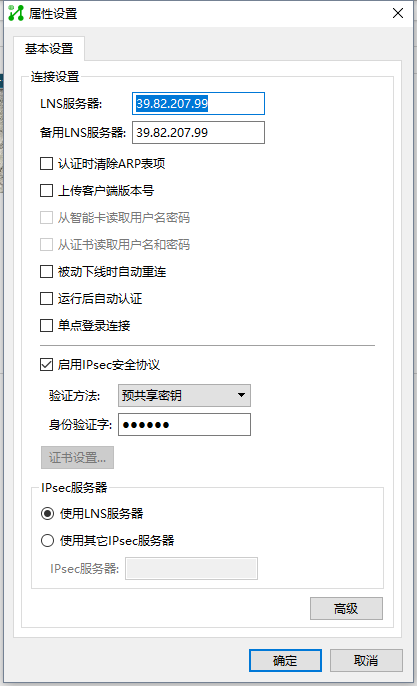
点击高级
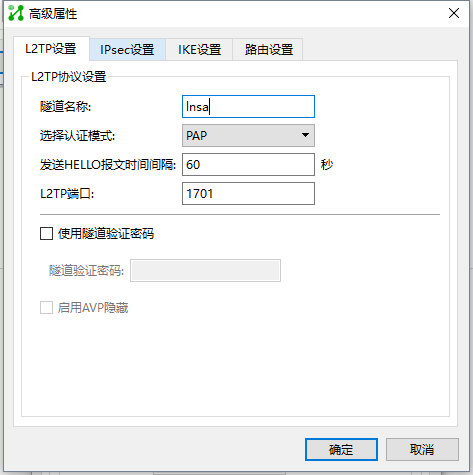

IKE这里 必须输入网关名字 就是FQDN号

实际测试系统 XP SP3, win7 64位 ,WIN server 2003 ,win server 2008 R2标准版 ,win server 2012 标准版 均无软件兼容性问题,建议分部PC选用以上系统,WIN 10部分系统存在兼容性问题,可能会导致 PPP无法建立会话 此时IKE SA和IPSEC SA均无问题。

参照以上配置,将PC的IP与外网口地址设为相同网段,直接接到该外网口后拨号就成功,但将外网口接入互联网后,在互联网环境拨号时,在IKE协商成功后提示隧道或会话建立失败,查看dis ike sa和dis ipsec sa都已正常建立,然后会自动断开。PC端为WIN11。
- 2022-11-28回复
- 评论(0)
- 举报
-
(0)
暂无评论


暂无评论