问题描述:
设置列表
- 有序列表
- 无序列表
对齐方式
- 靠左
- 居中
- 靠右
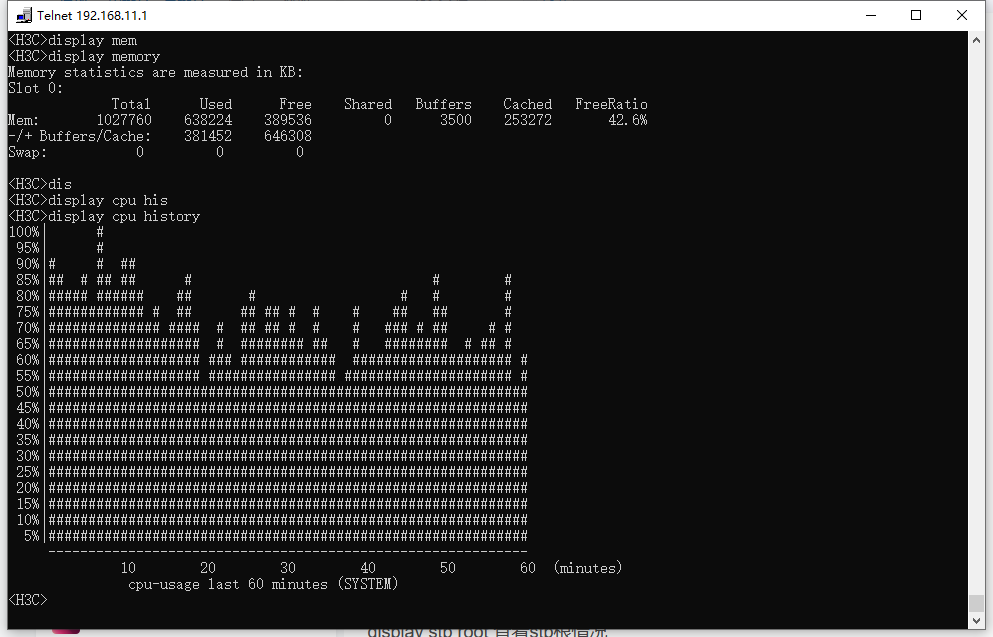
1、最近网络波动很明显,偶尔会断网,MSR2600CPU占用率很高,查看日志发现interface Virtual-Access0,interface Virtual-Access1口会翻动,在一段时间内不断UP DOWM,以及日志出现shell failed to log in from 58.21.146.180,或者其他IP地址, The usage of security log file flash:/seclog/seclog.log reaches 80%.等日志大量出现。telnet检查时命令行有明显卡顿。同时查看CPU占用较高。但内存占用一般。
2、在检查的时候发现切换使用备线 Dialer2 无法上网,但是有流量经过。不知道是Dialer1冲突了还是其他原因。
3、display interface Dialer 0 Dialer0
Current state: UP Line protocol state: UP Description: Dialer0 Interface Bandwidth: 1000000 kbps Maximum transmission unit: 1492 Hold timer: 10 seconds, retry times: 5 Internet address: 14.145.172.109/32 (PPP-negotiated) Link layer protocol: PPP LCP: initial Physical: Dialer, baudrate: 100000000 bps Output queue - Urgent queuing: Size/Length/Discards 0/1024/0 Output queue - Protocol queuing: Size/Length/Discards 0/500/0 Output queue - FIFO queuing: Size/Length/Discards 0/75/0 Last clearing of counters: Never Last 300 seconds input rate: 5711477 bytes/sec, 45691816 bits/sec, 6419 packets/sec Last 300 seconds output rate: 838847 bytes/sec, 6710776 bits/sec, 3556 packets/sec Input: 13649735410 packets, 11106225424178 bytes, 0 drops Output: 8171890213 packets, 2166551625406 bytes, 4 drops
display interface Dialer 1
Dialer1 Current state: UP Line protocol state: UP(spoofing) Description: Dialer1 Interface Bandwidth: 64 kbps Maximum transmission unit: 1492 Hold timer: 10 seconds, retry times: 5 Internet protocol processing: Enabled Link layer protocol: PPP LCP: initial Physical: Dialer, baudrate: 64000 bps Output queue - Urgent queuing: Size/Length/Discards 0/1024/0 Output queue - Protocol queuing: Size/Length/Discards 0/500/0 Output queue - FIFO queuing: Size/Length/Discards 0/75/0 Last clearing of counters: Never Last 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec Last 300 seconds output rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec Input: 0 packets, 0 bytes, 0 drops Output: 0 packets, 0 bytes, 0 drops
display interface Dialer 2
Dialer2 Current state: UP Line protocol state: UP Description: Dialer2 Interface Bandwidth: 1000000 kbps Maximum transmission unit: 1492 Hold timer: 10 seconds, retry times: 5 Internet address: 113.119.9.17/32 (PPP-negotiated) Link layer protocol: PPP LCP: initial Physical: Dialer, baudrate: 1000000 kbps Output queue - Urgent queuing: Size/Length/Discards 0/1024/0 Output queue - Protocol queuing: Size/Length/Discards 0/500/0 Output queue - FIFO queuing: Size/Length/Discards 0/75/0 Last clearing of counters: Never Last 300 seconds input rate: 7 bytes/sec, 56 bits/sec, 0 packets/sec Last 300 seconds output rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec Input: 3093416 packets, 2445066634 bytes, 0 drops Output: 1516751 packets, 253541090 bytes, 0 drops
ping测试和日志如下图
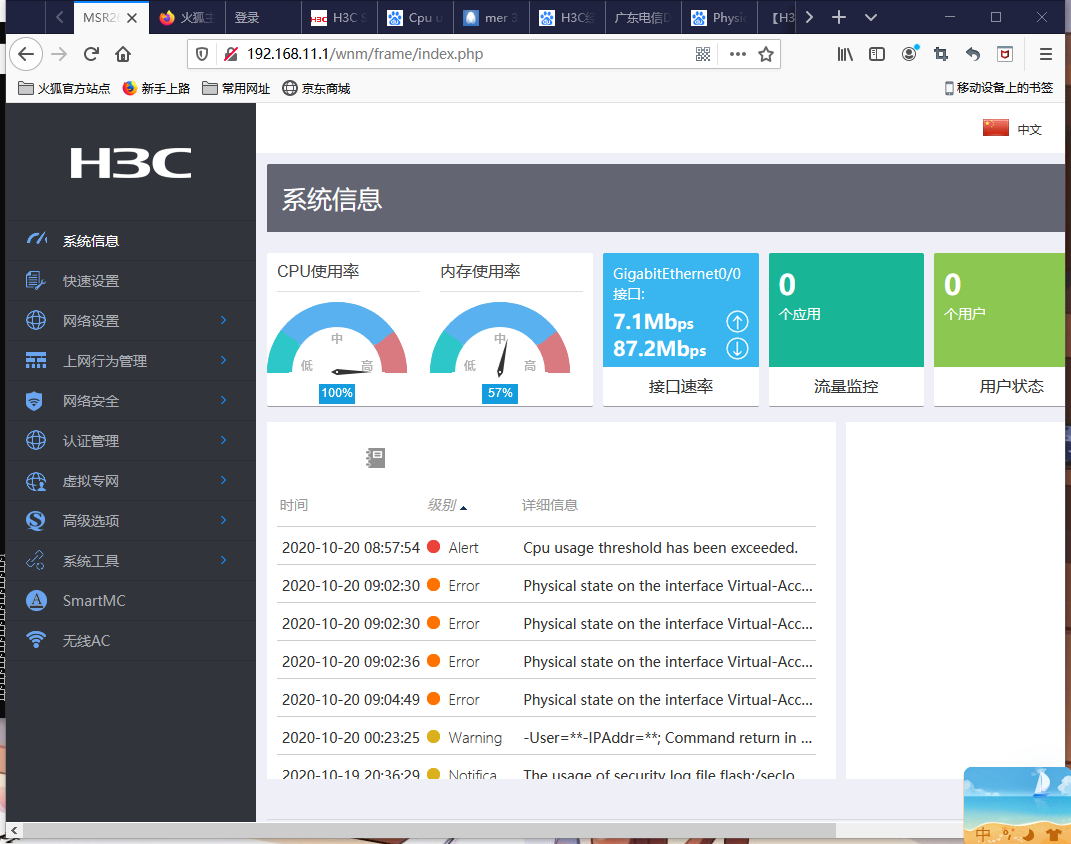
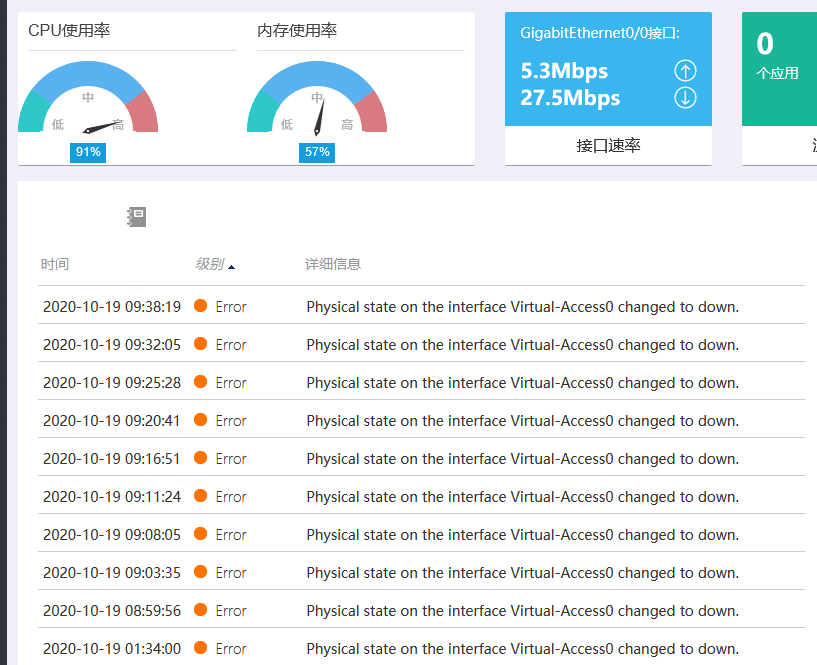

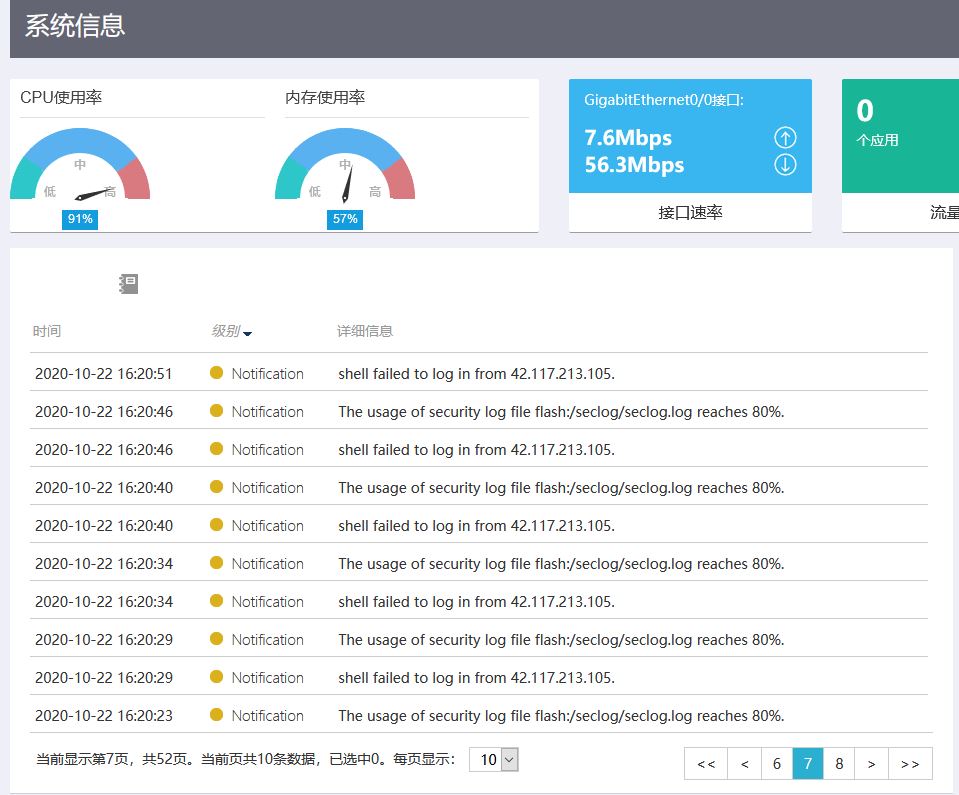
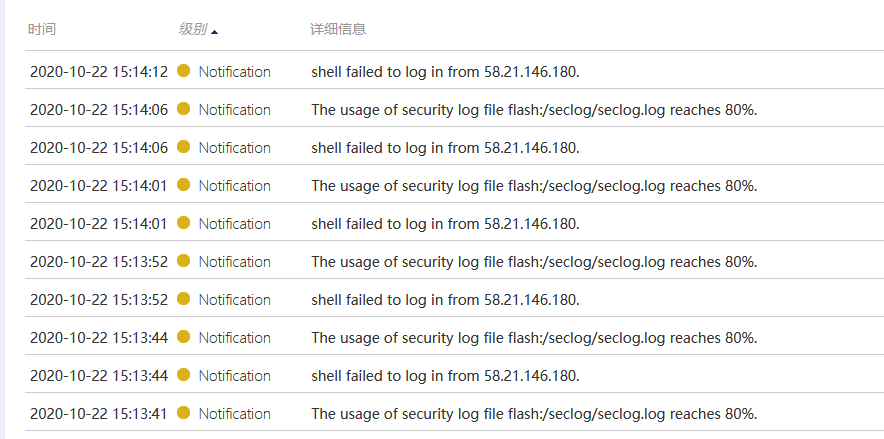



MSR2600 配置如下:
<H3C>display current-configuration
#
version 7.1.064, Release 0707P16
#
sysname H3C
#
clock timezone Beijing add 08:00:00
clock protocol ntp
#
telnet server enable
#
port-security enable
#
ip pool PPPoEServerIpPoolName 192.168.30.101 192.168.30.201
ip pool l2tp1 192.168.30.2 192.168.30.100
#
dialer-group 1 rule ip permit
dialer-group 2 rule ip permit
dialer-group 3 rule ip permit
#
dhcp enable
dhcp server always-broadcast
#
dns proxy enable
dns server 202.96.128.166
dns server 202.96.128.86
#
password-recovery enable
#
vlan 1
#
traffic behavior behaviorfordeny
filter deny
#
dhcp server ip-pool vlan1
gateway-list 192.168.11.1
network 192.168.11.0 mask 255.255.255.0
dns-list 192.168.11.1 202.96.128.86
static-bind ip-address 192.168.11.50 mask 255.255.255.0 hardware-address a4bb-6dc2-13cf
#
ddns policy GigabitEthernet0/0
url ***.***/dyndns/update?system=dyndns&hostname=<h>&myip=<a>
username fantadust
password cipher $c$3$BcMH+neN3Fix1gx5ZMTfZiPsSUvkB6i8hVzyBdQ=
#
ddns policy ***.***
url ***.***/dyndns/update?system=dyndns&hostname=<h>&myip=<a>
username root
password cipher $c$3$SzGpTwIX4/MByDdicVhA/cXEx2xhUI2Q7yUreig2JA==
interval 0 0 15
#
policy-based-route dust permit node 0
if-match acl 3000
apply output-interface Dialer0
#
policy-based-route dust permit node 10
if-match acl 3000
#
controller Cellular0/0
#
interface Aux0
#
interface Dialer0
bandwidth 1000000
mtu 1492
ppp chap password cipher $c$3$gRGRBYNencFGy7+v7rh61vG7bVwVmwDDNKNx
ppp chap user 02007723548@163.gd
ppp ipcp dns admit-any
ppp ipcp dns request
ppp pap local-user 02007723548@163.gd password cipher $c$3$dJJXXU+M+glzTZCSaLlIESeBGuqr4Q2bMb7U
dialer bundle enable
dialer-group 10
dialer timer idle 0
dialer timer autodial 5
ip address ppp-negotiate
tcp mss 1024
qos car inbound carl 1 cir 120000 cbs 62500 ebs 0 green pass red discard yellow pass
qos car inbound carl 4 cir 120000 cbs 7500000 ebs 0 green pass red discard yellow pass
qos car outbound carl 3 cir 15000 cbs 1250000 ebs 0 green pass red discard yellow pass
qos car outbound carl 2 cir 15000 cbs 750000 ebs 0 green pass red discard yellow pass
nat outbound
ddns apply policy GigabitEthernet0/0 fqdn ***.***
#
interface Dialer1
mtu 1492
ppp chap password cipher $c$3$dSSwdQHossgTarHWoJ8hv7HnhswNuJdwZNwm
ppp chap user 02001873127@163.gd
ppp ipcp dns admit-any
ppp ipcp dns request
ppp pap local-user 02001873127@163.gd password cipher $c$3$jVnwcJmLKt95YXc+SS1e9MKPRHwBR1XJER+L
dialer bundle enable
dialer-group 11
dialer timer idle 0
dialer timer autodial 5
ip address ppp-negotiate
tcp mss 1024
qos car inbound carl 6 cir 130000 cbs 7500000 ebs 0 green pass red discard yellow pass
qos car inbound carl 5 cir 120000 cbs 7500000 ebs 0 green pass red discard yellow pass
qos car inbound carl 9 cir 120000 cbs 7500000 ebs 0 green pass red discard yellow pass
qos car outbound carl 7 cir 15000 cbs 937500 ebs 0 green pass red discard yellow pass
qos car outbound carl 8 cir 15000 cbs 937500 ebs 0 green pass red discard yellow pass
qos car outbound carl 10 cir 15000 cbs 937500 ebs 0 green pass red discard yellow pass
nat outbound
ddns apply policy ***.*** fqdn ***.***
#
interface Dialer2
ppp chap password cipher $c$3$Q61fpp6YAr1aBShSjIUqODdAPVDtWsjrWgnJ
ppp chap user 02001873127@163.gd
ppp ipcp dns admit-any
ppp ipcp dns request
ppp pap local-user 02001873127@163.gd password cipher $c$3$qG4udYZV/rwN0vZXtoeR+odq/U3FGVf1ImUQ
dialer bundle enable
dialer-group 3
dialer timer idle 0
dialer timer autodial 5
ip address ppp-negotiate
nat outbound
ddns apply policy ***.*** fqdn ***.***
#
interface Virtual-Template0
ppp authentication-mode chap
ppp ipcp dns 192.168.30.1 202.96.128.166
remote address pool l2tp1
ip address 192.168.30.1 255.255.255.0
#
interface NULL0
#
interface Vlan-interface1
ip address 192.168.11.1 255.255.255.0
#
interface GigabitEthernet0/0
port link-mode route
description Multiple_Line
qos car inbound carl 5 cir 120000 cbs 7500000 ebs 0 green pass red discard yellow pass
qos car inbound carl 6 cir 130000 cbs 7500000 ebs 0 green pass red discard yellow pass
qos car inbound carl 9 cir 120000 cbs 7500000 ebs 0 green pass red discard yellow pass
qos car outbound carl 7 cir 15000 cbs 7500000 ebs 0 green pass red discard yellow pass
qos car outbound carl 8 cir 15000 cbs 750000 ebs 0 green pass red discard yellow pass
qos car outbound carl 10 cir 15000 cbs 937500 ebs 0 green pass red discard yellow pass
pppoe-client dial-bundle-number 0
#
interface GigabitEthernet0/1
port link-mode route
description Multiple_Line
pppoe-client dial-bundle-number 2
#
interface GigabitEthernet0/8
port link-mode route
tcp mss 1024
pppoe-server bind virtual-template 0
#
interface GigabitEthernet0/9
port link-mode route
#
interface GigabitEthernet0/2
port link-mode bridge
#
interface GigabitEthernet0/3
port link-mode bridge
#
interface GigabitEthernet0/4
port link-mode bridge
#
interface GigabitEthernet0/5
port link-mode bridge
#
interface GigabitEthernet0/6
port link-mode bridge
#
interface GigabitEthernet0/7
port link-mode bridge
#
security-zone name Local
#
security-zone name Trust
#
security-zone name DMZ
#
security-zone name Untrust
#
security-zone name Management
#
scheduler logfile size 16
#
line class aux
user-role network-admin
#
line class tty
user-role network-operator
#
line class usb
user-role network-admin
#
line class vty
user-role network-operator
#
line aux 0
user-role network-admin
#
line vty 0 63
authentication-mode scheme
user-role network-operator
#
ip route-static 0.0.0.0 0 Dialer0 preference 50
ip route-static 0.0.0.0 0 Dialer1 preference 80
ip route-static 0.0.0.0 0 Dialer2
ip route-static 192.168.14.0 23 192.168.11.2
ip route-static 192.168.15.0 24 192.168.11.2
ip route-static 192.168.17.0 24 192.168.11.3
ip route-static 192.168.18.0 23 192.168.11.2
ip route-static 192.168.20.0 24 192.168.11.2
ip route-static 192.168.21.0 24 192.168.11.2
ip route-static 192.168.22.0 24 192.168.11.3
ip route-static 192.168.40.0 24 192.168.11.2
ip route-static 192.168.100.0 24 192.168.11.3
#
info-center security-logfile enable
#
ntp-service enable
ntp-service unicast-server 114.118.7.161
ntp-service unicast-server 120.25.108.11
#
acl basic 2999
rule 1 permit source 192.168.11.50 0
#
acl advanced 3000
rule 0 permit ip source 192.168.15.0 0.0.0.255
#
undo password-control aging enable
undo password-control history enable
password-control length 6
password-control login-attempt 3 exceed lock-time 10
password-control update-interval 0
password-control login idle-time 0
password-control complexity user-name check
#
domain system
#
domain default enable system
#
role name level-0
description Predefined level-0 role
#
role name level-1
description Predefined level-1 role
#
role name level-2
description Predefined level-2 role
#
role name level-3
description Predefined level-3 role
#
role name level-4
description Predefined level-4 role
#
role name level-5
description Predefined level-5 role
#
role name level-6
description Predefined level-6 role
#
role name level-7
description Predefined level-7 role
#
role name level-8
description Predefined level-8 role
#
role name level-9
description Predefined level-9 role
#
role name level-10
description Predefined level-10 role
#
role name level-11
description Predefined level-11 role
#
role name level-12
description Predefined level-12 role
#
role name level-13
description Predefined level-13 role
#
role name level-14
description Predefined level-14 role
#
user-group system
#
local-user admin class manage
password hash $h$6$M8weHhmmbGXBQT/k$eSbNYXIINYmRaMVOrqO0FQjE88K3Oo/EWVMhRbbMTbGIzjUHFDaUXb/jYqOhdxj17Ceq3GMLLbzpJVhiYF2weg==
service-type ftp
service-type telnet terminal http
authorization-attribute user-role network-admin
#
local-user fantadust class manage
password hash $h$6$hW8XrWjRnwLdxcTe$s6TRc7+9g+M9UhJ8VGzpTFR4A3zKjocFjXNhVx0WOOvrw55Z3t13BlLLBwWd7ZC4pE4TiT6HYe5gy/AeNUWA1Q==
authorization-attribute user-role network-operator
#
local-user vpn2020 class manage
authorization-attribute user-role network-operator
#
local-user vpner class manage
authorization-attribute user-role network-operator
#
local-user fantadust class network
password cipher $c$3$NwBSr0nYk7v1B7C4+mXkBY27MBDKo6c3v2k4I6g=
service-type ppp
authorization-attribute user-role network-operator
#
local-user vpn2020 class network
password cipher $c$3$myVzp/EbMvqsh4zzweOuu/YgfFwZch4cTs9+YNN4
service-type ppp
authorization-attribute user-role network-operator
#
l2tp-group 1 mode lns
allow l2tp virtual-template 0
undo tunnel authentication
tunnel password cipher $c$3$t3v5bwyQ/++a1dh9LRBZE3WeDaaS2oF9WEE=
#
l2tp enable
#
ip http enable
web idle-timeout 300
#
wlan global-configuration
#
wlan ap-group default-group
vlan 1
#
cloud-management server domain oasis.h3c.com
#
return
组网及组网描述:
MSR2600为核心出口路由 出口为两条电信五百兆宽带。其中MSR2600ZHONG 配置了最基础的L2TPVPN 下联S5560交换机,交换机下联无线AC和一堆傻瓜交换机。
请问
1、是不是因为启用telnet被攻击了,在不断试登录?
2、网络波动是负载过大还是,其他原因?有限和无线总共带了接近400台设备
3、双出口的拨号设置是否有问题?谢谢各位大佬!
- 2020-10-22提问
- 举报
-
(0)
最佳答案

您好,请知:
看到了CPU的利用率已经到了80%,CPU利用率过高会对业务有影响。
同时看到有主机在尝试登陆路由器,可以根据日志反馈的IP在ACL内进行拦截看下。为了保证设备的安全,建议使用复杂度高的密码。
另外也可以使用dis process cpu查看下具体是哪个进程对于CPU的利用率高。
以下是MSR2600的用户手册连接:
https://www.h3c.com/cn/Service/Document_Software/Document_Center/Routers/Catalog/MSR/MSR_2600/
- 2020-10-22回答
- 评论(0)
- 举报
-
(0)
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明



