防火墙无法通过tracert
- 0关注
- 1收藏,4563浏览
问题描述:
有一台防火墙H3C F1050,防火墙上联一台路由器,下联一台交换机。这3台设备,tracert外网一台设备,IP:10.0.0.1,其中在路由器和防火墙上tracert,都可以获得完整的tracert数据;在交换机上tracert只能获得最后一跳(即10.0.0.1)的数据,中间的路径全部是*号;经过排查感觉问题是在防火墙上,但防火墙已经配置以下命令:
ip unreachables enable
ip ttl-expires enable
session state-machine mode loose
#
仍然没有作用
以下是防火墙的配置,麻烦帮忙看看是什么原因导致
#
version 7.1.064, Release 9313P1901
#
sysname FW_F1050
#
clock timezone Beijing add 08:00:00
clock protocol ntp context 1
#
context Admin id 1
#
telnet server enable
#
irf mac-address persistent timer
irf auto-update enable
undo irf link-delay
irf member 1 priority 2
irf member 2 priority 1
#
ip unreachables enable
ip ttl-expires enable
#
lldp global enable
#
password-recovery enable
#
vlan 1
#
vlan 100
#
irf-port 1/2
port group interface GigabitEthernet1/0/15
#
irf-port 2/1
port group interface GigabitEthernet2/0/15
#
object-group service Fang
0 service tcp destination eq 69
3 service tcp destination eq 1434
5 service tcp destination eq 4444
6 service tcp destination eq 5554
7 service tcp destination eq 5444
8 service tcp destination eq 1068
9 service tcp destination eq 9996
10 service tcp destination eq 1025
11 service tcp destination eq 539
12 service tcp destination eq 7995
13 service tcp destination eq 6667
15 service udp destination eq 1434
17 service udp destination eq 4444
18 service udp destination eq 5444
19 service udp destination eq 9996
20 service udp destination eq 1025
21 service udp destination eq 539
22 service udp destination eq 7995
23 service udp destination eq 6667
40 service tcp destination eq 3389
50 service tcp source eq 445
60 service udp source eq 445
70 service udp destination eq 445
80 service tcp destination eq 445
90 service tcp source range 135 139
100 service udp source range 135 139
110 service udp destination range 135 139
120 service tcp destination range 135 139
#
interface NULL0
#
interface Vlan-interface100
ip address 10.X.X.X 255.255.255.0
#
interface GigabitEthernet1/0/0
port link-mode route
#
interface GigabitEthernet1/0/3
port link-mode route
#
interface GigabitEthernet1/0/4
port link-mode route
#
interface GigabitEthernet1/0/5
port link-mode route
#
interface GigabitEthernet1/0/6
port link-mode route
#
interface GigabitEthernet1/0/7
port link-mode route
#
interface GigabitEthernet1/0/8
port link-mode route
#
interface GigabitEthernet1/0/9
port link-mode route
#
interface GigabitEthernet1/0/11
port link-mode route
#
interface GigabitEthernet1/0/12
port link-mode route
#
interface GigabitEthernet1/0/14
port link-mode route
#
interface GigabitEthernet1/0/18
port link-mode route
#
interface GigabitEthernet1/0/19
port link-mode route
#
interface GigabitEthernet1/0/20
port link-mode route
#
interface GigabitEthernet1/0/21
port link-mode route
#
interface GigabitEthernet1/0/22
port link-mode route
#
interface GigabitEthernet1/0/23
port link-mode route
#
interface GigabitEthernet2/0/0
port link-mode route
#
interface GigabitEthernet2/0/3
port link-mode route
#
interface GigabitEthernet2/0/4
port link-mode route
#
interface GigabitEthernet2/0/5
port link-mode route
#
interface GigabitEthernet2/0/6
port link-mode route
#
interface GigabitEthernet2/0/7
port link-mode route
#
interface GigabitEthernet2/0/8
port link-mode route
#
interface GigabitEthernet2/0/9
port link-mode route
#
interface GigabitEthernet2/0/10
port link-mode route
#
interface GigabitEthernet2/0/11
port link-mode route
#
interface GigabitEthernet2/0/12
port link-mode route
#
interface GigabitEthernet2/0/13
port link-mode route
#
interface GigabitEthernet2/0/14
port link-mode route
#
interface GigabitEthernet2/0/18
port link-mode route
#
interface GigabitEthernet2/0/19
port link-mode route
#
interface GigabitEthernet2/0/20
port link-mode route
#
interface GigabitEthernet2/0/21
port link-mode route
#
interface GigabitEthernet2/0/22
port link-mode route
#
interface GigabitEthernet2/0/23
port link-mode route
#
interface GigabitEthernet1/0/1
port link-mode bridge
port access vlan 100
#
interface GigabitEthernet1/0/2
port link-mode bridge
port access vlan 100
#
interface GigabitEthernet1/0/10
port link-mode bridge
port access vlan 100
#
interface GigabitEthernet1/0/13
port link-mode bridge
port access vlan 100
#
interface GigabitEthernet1/0/16
port link-mode bridge
port access vlan 100
#
interface GigabitEthernet1/0/17
port link-mode bridge
port access vlan 100
#
interface GigabitEthernet2/0/1
port link-mode bridge
port access vlan 100
#
interface GigabitEthernet2/0/2
port link-mode bridge
port access vlan 100
#
interface GigabitEthernet2/0/16
port link-mode bridge
port access vlan 100
#
interface GigabitEthernet2/0/17
port link-mode bridge
port access vlan 100
#
interface GigabitEthernet1/0/15
#
interface GigabitEthernet2/0/15
description IRF_LINK—_GE1/0/15
#
object-policy ip Local-Trust
rule 0 pass counting
#
object-policy ip Local-Untrust
rule 0 pass counting
#
object-policy ip Trust-Local
rule 0 pass
#
object-policy ip Trust-Trust
rule 100 pass counting
#
object-policy ip Trust-Untrust
rule 15 pass service icmp-traceroute
rule 5 drop service FangBingDu counting
rule 5 comment FangBingDU
rule 12 pass counting
#
object-policy ip Untrust-Local
rule 0 pass
#
object-policy ip Untrust-Trust
rule 56958 pass service icmp-traceroute
rule 5 drop service FangBingDu counting
rule 5 comment FangBingDu
rule 9 pass counting
#
object-policy ip Untrust-Untrust
rule 0 pass
#
security-zone name Local
attack-defense apply policy test1
#
security-zone name Trust
import interface Vlan-interface100
import interface GigabitEthernet1/0/2 vlan 100
import interface GigabitEthernet1/0/10 vlan 100
import interface GigabitEthernet1/0/13 vlan 100
import interface GigabitEthernet1/0/16 vlan 100
import interface GigabitEthernet1/0/17 vlan 100
import interface GigabitEthernet2/0/2 vlan 100
import interface GigabitEthernet2/0/16 vlan 100
import interface GigabitEthernet2/0/17 vlan 100
attack-defense apply policy test1
#
security-zone name DMZ
attack-defense apply policy test1
#
security-zone name Untrust
import interface GigabitEthernet1/0/1 vlan 100
import interface GigabitEthernet2/0/1 vlan 100
attack-defense apply policy test1
#
security-zone name Management
import interface GigabitEthernet1/0/0
attack-defense apply policy test1
#
security-zone name tu
#
zone-pair security source Any destination Any
#
zone-pair security source Local destination Trust
object-policy apply ip Local-Trust
#
zone-pair security source Local destination Untrust
object-policy apply ip Local-Untrust
#
zone-pair security source Trust destination Local
object-policy apply ip Trust-Local
#
zone-pair security source Trust destination Trust
object-policy apply ip Trust-Trust
#
zone-pair security source Trust destination Untrust
object-policy apply ip Trust-Untrust
#
zone-pair security source Untrust destination Local
object-policy apply ip Untrust-Local
#
zone-pair security source Untrust destination Trust
object-policy apply ip Untrust-Trust
#
zone-pair security source Untrust destination Untrust
object-policy apply ip Untrust-Untrust
#
scheduler logfile size 16
#
line class aux
user-role network-operator
#
line class console
user-role network-admin
#
line class vty
user-role network-operator
#
line aux 0
user-role network-admin
#
line aux 1
user-role network-operator
#
line con 0
user-role network-admin
set authentication password hash $h$6$6ec9UUhlpMd+4bIh$Bk5o9
#
line con 1
authentication-mode scheme
user-role network-admin
#
line vty 0 63
authentication-mode scheme
user-role network-admin
#
userlog flow export version 3
#
time-range ceshi-dns from 16:30 9/8/2021 to 16:30 9/9/2021
time-range test from 16:40 9/8/2021 to 16:42 9/8/2021
#
sntp enable
#
password-control history 3
password-control login-attempt 5 exceed lock-time 5
#
domain system
#
aaa session-limit ftp 16
aaa session-limit telnet 16
aaa session-limit ssh 16
domain default enable system
#
role name level-0
description Predefined level-0 role
#
role name level-1
description Predefined level-1 role
#
role name level-2
description Predefined level-2 role
#
role name level-3
description Predefined level-3 role
#
role name level-4
description Predefined level-4 role
#
role name level-5
description Predefined level-5 role
#
role name level-6
description Predefined level-6 role
#
role name level-7
description Predefined level-7 role
#
role name level-8
description Predefined level-8 role
#
role name level-9
description Predefined level-9 role
#
role name level-10
description Predefined level-10 role
#
role name level-11
description Predefined level-11 role
#
role name level-12
description Predefined level-12 role
#
role name level-13
description Predefined level-13 role
#
role name level-14
description Predefined level-14 role
#
user-group system
#
local-user admin class manage
password hash $h$6$HNHtkSUtAiUGx7xf$sFOWXcL34WyWPR4UENUTa
service-type ssh https
authorization-attribute user-role network-admin
authorization-attribute user-role network-operator
password-control aging 90
password-control length 10
password-control composition type-number 3 type-length 1
password-control login-attempt 3 exceed lock-time 3
#
session top-statistics enable
session synchronization enable
session synchronization dns http
session state-machine mode loose
#
ip https enable
#
app-profile 5_3_56956_IPv4
ips apply policy ceshi1 mode protect
anti-virus apply policy default mode protect
#
inspect block-source parameter-profile ips_block_default_parameter
#
inspect capture parameter-profile ips_capture_default_parameter
#
inspect logging parameter-profile ips_logging_default_parameter
#
inspect redirect parameter-profile av_redirect_default_parameter
#
inspect redirect parameter-profile ips_redirect_default_parameter
#
inspect redirect parameter-profile url_redirect_default_parameter
#
ips policy default
#
anti-virus policy ceshi
inspect smtp action block
inspect pop3 action block
#
anti-virus policy default
#
return
#
组网及组网描述:
- 2022-05-12提问
- 举报
-
(0)

zone-pair security source Any destination Any
这条没生效 , 配置一条安全策略any到any全放通的,放在最前面,测试是不是策略阻挡
- 2022-05-12回答
- 评论(1)
- 举报
-
(0)
trust-untrust和untrust-trust的路径,都是有放通,应该不需要any-any吧
trust-untrust和untrust-trust的路径,都是有放通,应该不需要any-any吧

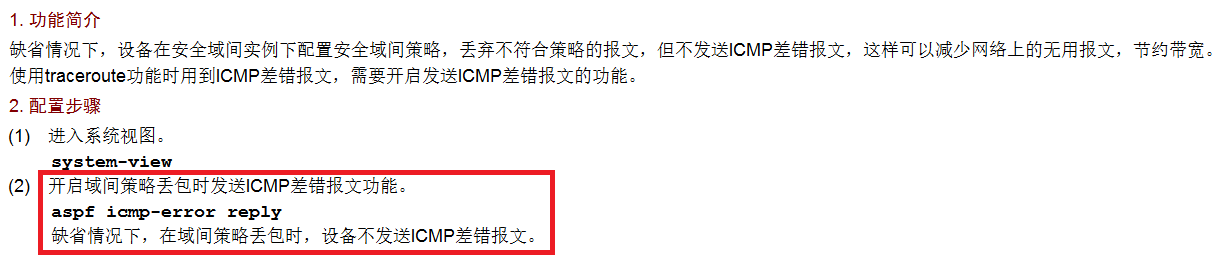
应该是被策略阻止了,你输入如下命令,允许防火墙回包icmp差错报文,再tracert看看是不是回显了一堆防火墙的地址。
其实昨天就跟你说过,用包过滤,不要用域间策略的traceroute服务,容易出问题。
- 2022-05-12回答
- 评论(0)
- 举报
-
(0)
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明



