问题描述:
组网情况:
Msr3600-28-xs是一台出口路由器(路由交换一体机,有20多个口作交换机用)
另有2个wan口,之前GE0 接【线路1】这条宽带,固定ip上网
共有vlan4 机房用 192.168.4.0/24
vlan5 、6、7 固定pc机 网线接入 对应ip段都是 192.168.x.0/24
vlan8 无线ap接入 192.168.8.0/24
各vlan可以互相ping通。
路由器下连了一台POE交换机S5120V3。
需求:
新增了【线路2】,就是GE1口,拨号 Dialer1 的宽带。
需要修改路由策略,让(vlan4 机房用 192.168.4.0/24)走(【线路1】这条宽带,固定ip)出去。
其它vlan都走【线路2】
同时,各vlan在内网保持互通。
问题描述:
之前网上请教和搜索,拼凑配置了策略路由。
配置完以后。vlan5 6 7各试了一台,都是按预期,走的【线路1】
但vlan4 4.0网段,机房有不少服务器,有的ip如4.132走的【线路1】,有的走的【线路2】,不一定,怎么办?
测试方法 windows cmd下 : tracert 163.com
~~~~~~~~~~~~~~~~~~~~~~~~
8.0网段比较特殊,在交换机上配置的
怎么配?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
我拟定的,部分策略路由的配置:
vlan 5 6 7 8 走319宽带 Dialer1
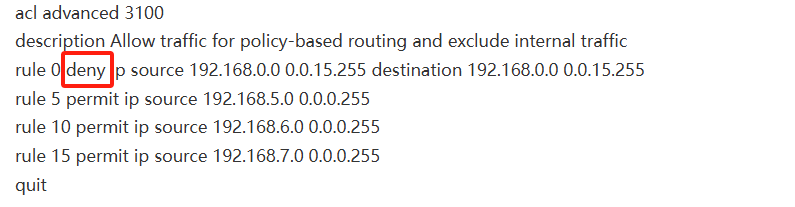
acl advanced 3100
description Allow traffic for policy-based routing and exclude internal traffic
rule 0 deny ip source 192.168.0.0 0.0.15.255 destination 192.168.0.0 0.0.15.255
rule 5 permit ip source 192.168.5.0 0.0.0.255
rule 10 permit ip source 192.168.6.0 0.0.0.255
rule 15 permit ip source 192.168.7.0 0.0.0.255
quit
policy-based-route neiwang node 10
if-match acl 3100
apply output-interface Dialer1
quit
interface Vlan-interface6
ip policy-based-route neiwang
quit
vlan5 和 7 也是这样配置
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
vlan4 走默认【线路1】这条宽带
acl advanced 3200
description Allow traffic for policy-based routing and exclude internal traffic
rule 0 deny ip source 192.168.0.0 0.0.15.255 destination 192.168.0.0 0.0.15.255
rule 5 permit ip source 192.168.4.0 0.0.0.255
quit
policy-based-route neiwang4.0 node 20
if-match acl 3200
apply output-interface GigabitEthernet0/0
quit
interface Vlan-interface4
ip policy-based-route neiwang4.0
quit
~~~~~~~~~~~~~~~~~~~~~~~~
配置策略路由之前的 【路由表】
[msr3600]display ip routing-table
Destinations : 39 Routes : 39
Destination/Mask Proto Pre Cost NextHop Interface
0.0.0.0/0 Static 60 0 125.81.1.1 GE0/0
0.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
125.81.1.0/24 Direct 0 0 125.81.1.29 GE0/0
125.81.1.29/32 Direct 0 0 127.0.0.1 InLoop0
125.81.1.255/32 Direct 0 0 125.81.1.29 GE0/0
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
127.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
192.168.0.0/23 Direct 0 0 192.168.0.1 Vlan1
192.168.0.1/32 Direct 0 0 127.0.0.1 InLoop0
192.168.1.255/32 Direct 0 0 192.168.0.1 Vlan1
192.168.4.0/24 Direct 0 0 192.168.4.1 Vlan4
192.168.4.1/32 Direct 0 0 127.0.0.1 InLoop0
192.168.4.255/32 Direct 0 0 192.168.4.1 Vlan4
192.168.5.0/24 Direct 0 0 192.168.5.1 Vlan5
192.168.5.1/32 Direct 0 0 127.0.0.1 InLoop0
192.168.5.255/32 Direct 0 0 192.168.5.1 Vlan5
192.168.6.0/24 Direct 0 0 192.168.6.1 Vlan6
192.168.6.1/32 Direct 0 0 127.0.0.1 InLoop0
192.168.6.255/32 Direct 0 0 192.168.6.1 Vlan6
192.168.7.0/24 Direct 0 0 192.168.7.1 Vlan7
192.168.7.1/32 Direct 0 0 127.0.0.1 InLoop0
192.168.7.255/32 Direct 0 0 192.168.7.1 Vlan7
192.168.8.0/24 Direct 0 0 192.168.8.253 Vlan8
192.168.8.253/32 Direct 0 0 127.0.0.1 InLoop0
192.168.8.255/32 Direct 0 0 192.168.8.253 Vlan8
192.168.9.0/24 Static 60 0 192.168.10.2 Vlan10
192.168.10.0/24 Direct 0 0 192.168.10.1 Vlan10
192.168.10.1/32 Direct 0 0 127.0.0.1 InLoop0
192.168.10.255/32 Direct 0 0 192.168.10.1 Vlan10
192.168.11.0/24 Direct 0 0 192.168.11.253 Vlan11
192.168.11.253/32 Direct 0 0 127.0.0.1 InLoop0
192.168.11.255/32 Direct 0 0 192.168.11.253 Vlan11
192.168.172.0/24 Direct 0 0 192.168.172.1 SSLVPN-AC1
192.168.172.1/32 Direct 0 0 127.0.0.1 InLoop0
192.168.172.255/32 Direct 0 0 192.168.172.1 SSLVPN-AC1
224.0.0.0/4 Direct 0 0 0.0.0.0 NULL0
224.0.0.0/24 Direct 0 0 0.0.0.0 NULL0
255.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
[msr3600]
~~~~~~~~~~~~~~~~~~~~~~~~~~~~
附,配置后的整体配置,dis curr
~~~~~~~~~~~~~~~~~~~~~~~~~
以下是配置原文
#
version 7.1.064, Release 6749P2102
#
sysname msr3600
#
clock timezone Beijing add 08:00:00
clock protocol ntp
#
wlan global-configuration
#
qos carl 1 source-ip-address object-group temp1 per-address shared-bandwidth
qos carl 2 destination-ip-address object-group temp1 per-address shared-bandwidth
qos carl 3 source-ip-address object-group temp2 per-address
qos carl 4 destination-ip-address object-group temp2 per-address
qos carl 5 source-ip-address object-group temp2 per-address
qos carl 6 destination-ip-address object-group temp2 per-address
qos carl 7 source-ip-address object-group temp1 per-address shared-bandwidth
qos carl 8 destination-ip-address object-group temp1 per-address shared-bandwidth
qos carl 9 source-ip-address object-group temp3 per-address
qos carl 10 destination-ip-address object-group temp3 per-address
qos carl 11 source-ip-address object-group temp1 per-address shared-bandwidth
qos carl 12 destination-ip-address object-group temp1 per-address shared-bandwidth
qos carl 13 source-ip-address object-group temp1 per-address shared-bandwidth
qos carl 14 destination-ip-address object-group temp1 per-address shared-bandwidth
qos carl 15 source-ip-address object-group temp1 per-address shared-bandwidth
qos carl 16 destination-ip-address object-group temp1 per-address shared-bandwidth
#
security-policy disable
#
dialer-group 2 rule ip permit
#
dhcp enable
dhcp server forbidden-ip 192.168.5.1 192.168.5.150
dhcp server forbidden-ip 192.168.6.1 192.168.6.150
dhcp server forbidden-ip 192.168.7.1 192.168.7.150
#
dns proxy enable
dns server 114.114.114.114
dns server 218.6.200.139
dns server 223.6.6.6
#
lldp global enable
#
system-working-mode standard
password-recovery enable
#
vlan 1
#
vlan 4 to 8
#
vlan 10 to 11
#
object-group ip address 10.0
0 network range 192.168.10.2 192.168.10.254
#
object-group ip address 4.0
0 network range 192.168.4.1 192.168.4.254
#
object-group ip address 5.0
0 network range 192.168.5.1 192.168.5.254
#
object-group ip address 6.0
0 network range 192.168.6.1 192.168.6.254
#
object-group ip address 7.0
0 network range 192.168.7.1 192.168.7.254
0 network exclude 192.168.7.69
#
object-group ip address 8.0
0 network range 192.168.8.1 192.168.8.254
#
object-group ip address temp1
description 临时占用用于限速排行
#
object-group ip address temp2
description 临时占位用于限速排行
#
object-group ip address temp3
description 临时占用用于限速排行
0 network host address 172.16.111.112
#
stp instance 0 root primary
stp global enable
#
dhcp server ip-pool lan1
gateway-list 192.168.0.1
network 192.168.0.0 mask 255.255.254.0
address range 192.168.1.3 192.168.1.254
dns-list 192.168.0.1
#
dhcp server ip-pool vlan5
gateway-list 192.168.5.1
network 192.168.5.0 mask 255.255.255.0
address range 192.168.5.150 192.168.5.250
dns-list 192.168.5.1
#
dhcp server ip-pool vlan6
gateway-list 192.168.6.1
network 192.168.6.0 mask 255.255.255.0
address range 192.168.6.150 192.168.6.250
dns-list 192.168.6.1
#
dhcp server ip-pool vlan7
gateway-list 192.168.7.1
network 192.168.7.0 mask 255.255.255.0
address range 192.168.7.150 192.168.7.250
dns-list 192.168.7.1
#
dhcp server ip-pool vlan-interface11
gateway-list 192.168.11.253
network 192.168.11.0 mask 255.255.255.0
address range 192.168.11.150 192.168.11.250
dns-list 192.168.11.253
forbidden-ip-range 192.168.11.253 192.168.11.253
#
policy-based-route neiwang permit node 10
if-match acl 3100
apply output-interface Dialer1
#
policy-based-route neiwang4.0 permit node 20
if-match acl 3200
apply output-interface GigabitEthernet0/0
#
wlan service-template h3c
ssid H3C
service-template enable
#
wlan service-template h3c_5g
ssid H3C_5G
service-template enable
#
controller Cellular0/0
#
interface Bridge-Aggregation1
port access vlan 4
#
interface Bridge-Aggregation2
port access vlan 4
#
interface Bridge-Aggregation3
port access vlan 4
#
interface Dialer0
mtu 1492
#
interface Dialer1
mtu 1492
ppp chap password cipher $c$3$Bwfyq2k7kf7HnGJX+EMjPYoMYNu3O1YSfII5
ppp chap user CD02833025248351
ppp ipcp dns admit-any
ppp ipcp dns request
ppp pap local-user CD02833025248351 password cipher $c$3$Ri71gxU5B8VAaO6UUzF4Cfgk1fA/DHUE+TtH
dialer bundle enable
dialer-group 2
dialer timer idle 0
dialer timer autodial 5
ip address ppp-negotiate
tcp mss 1280
nat outbound
#
interface NULL0
#
interface Vlan-interface1
description LAN-interface
ip address 192.168.0.1 255.255.254.0
tcp mss 1280
nat hairpin enable
#
interface Vlan-interface4
description LAN-interface
ip address 192.168.4.1 255.255.255.0
packet-filter 3001 inbound
packet-filter 3001 outbound
nat hairpin enable
ip policy-based-route neiwang4.0
#
interface Vlan-interface5
description LAN-interface
ip address 192.168.5.1 255.255.255.0
packet-filter 3001 inbound
packet-filter 3001 outbound
nat hairpin enable
ip policy-based-route neiwang
#
interface Vlan-interface6
description LAN-interface
ip address 192.168.6.1 255.255.255.0
packet-filter 3001 inbound
packet-filter 3001 outbound
nat hairpin enable
ip policy-based-route neiwang
#
interface Vlan-interface7
description LAN-interface
ip address 192.168.7.1 255.255.255.0
packet-filter 3001 inbound
packet-filter 3001 outbound
nat hairpin enable
ip policy-based-route neiwang
#
interface Vlan-interface8
ip address 192.168.8.253 255.255.255.0
tcp mss 1280
nat hairpin enable
undo dhcp select server
#
interface Vlan-interface10
ip address 192.168.10.1 255.255.255.0
packet-filter name Vlan-interface10 inbound
packet-filter 3001 inbound
packet-filter 3001 outbound
nat hairpin enable
#
interface Vlan-interface11
description LAN-interface
ip address 192.168.11.253 255.255.255.0
tcp mss 1280
nat hairpin enable
#
interface GigabitEthernet0/0
port link-mode route
description Double_Line1
ip address 125.81.1.29 255.255.255.0
dns server 218.6.200.139
dns server 223.6.6.6
tcp mss 1280
packet-filter name GigabitEthernet0/0 inbound
qos car inbound carl 4 cir 10 cbs 1000 ebs 0 green pass red discard yellow pass
qos car inbound carl 6 cir 5123 cbs 320187 ebs 0 green pass red discard yellow pass
qos car inbound carl 10 cir 5123 cbs 320187 ebs 0 green pass red discard yellow pass
qos car inbound carl 2 cir 60123 cbs 3757687 ebs 0 green pass red discard yellow pass
qos car inbound carl 8 cir 60123 cbs 3757687 ebs 0 green pass red discard yellow pass
qos car inbound carl 12 cir 60123 cbs 3757687 ebs 0 green pass red discard yellow pass
qos car inbound carl 14 cir 60123 cbs 3757687 ebs 0 green pass red discard yellow pass
qos car inbound carl 16 cir 60123 cbs 3757687 ebs 0 green pass red discard yellow pass
qos car outbound carl 3 cir 10 cbs 1000 ebs 0 green pass red discard yellow pass
qos car outbound carl 5 cir 5123 cbs 320187 ebs 0 green pass red discard yellow pass
qos car outbound carl 9 cir 5123 cbs 320187 ebs 0 green pass red discard yellow pass
qos car outbound carl 1 cir 60123 cbs 3757687 ebs 0 green pass red discard yellow pass
qos car outbound carl 7 cir 60123 cbs 3757687 ebs 0 green pass red discard yellow pass
qos car outbound carl 11 cir 60123 cbs 3757687 ebs 0 green pass red discard yellow pass
qos car outbound carl 13 cir 60123 cbs 3757687 ebs 0 green pass red discard yellow pass
qos car outbound carl 15 cir 60123 cbs 3757687 ebs 0 green pass red discard yellow pass
nat outbound
……
……
#
interface GigabitEthernet0/1
port link-mode route
description Double_Line2
pppoe-client dial-bundle-number 1
#
interface GigabitEthernet0/2
port link-mode route
#
interface GigabitEthernet0/27
port link-mode route
#
interface GigabitEthernet0/28
port link-mode route
#
interface GigabitEthernet0/3
port link-mode bridge
port access vlan 7
#
interface GigabitEthernet0/4
port link-mode bridge
port access vlan 7
#
interface GigabitEthernet0/5
port link-mode bridge
port access vlan 7
#
interface GigabitEthernet0/6
port link-mode bridge
port access vlan 7
#
interface GigabitEthernet0/7
port link-mode bridge
port access vlan 7
#
interface GigabitEthernet0/8
port link-mode bridge
port access vlan 7
#
interface GigabitEthernet0/9
port link-mode bridge
port access vlan 7
#
interface GigabitEthernet0/10
port link-mode bridge
port access vlan 7
#
interface GigabitEthernet0/11
port link-mode bridge
port access vlan 6
#
interface GigabitEthernet0/12
port link-mode bridge
port access vlan 6
#
interface GigabitEthernet0/13
port link-mode bridge
port access vlan 6
#
interface GigabitEthernet0/14
port link-mode bridge
port access vlan 6
#
interface GigabitEthernet0/15
port link-mode bridge
port access vlan 6
#
interface GigabitEthernet0/16
port link-mode bridge
port link-type trunk
undo port trunk permit vlan 1
port trunk permit vlan 6
port trunk pvid vlan 6
#
interface GigabitEthernet0/17
port link-mode bridge
port access vlan 5
#
interface GigabitEthernet0/18
port link-mode bridge
port access vlan 5
#
interface GigabitEthernet0/19
port link-mode bridge
port access vlan 5
#
interface GigabitEthernet0/20
port link-mode bridge
port access vlan 5
#
interface GigabitEthernet0/21
port link-mode bridge
port access vlan 4
port link-aggregation group 1
#
interface GigabitEthernet0/22
port link-mode bridge
port access vlan 4
port link-aggregation group 1
#
interface GigabitEthernet0/23
port link-mode bridge
port access vlan 10
#
interface GigabitEthernet0/24
port link-mode bridge
port link-type trunk
port trunk permit vlan all
#
interface GigabitEthernet0/25
port link-mode bridge
port access vlan 4
port link-aggregation group 3
#
interface GigabitEthernet0/26
port link-mode bridge
port access vlan 4
port link-aggregation group 3
#
interface SSLVPN-AC1
ip address 192.168.172.1 255.255.255.0
#
object-policy ip Any-Any
rule 65533 inspect 8048_url_profile_global disable
rule 65534 pass
#
security-zone name Local
#
security-zone name Trust
#
security-zone name DMZ
#
security-zone name Untrust
#
security-zone name Management
#
scheduler logfile size 16
#
line class console
user-role network-admin
#
line class tty
user-role network-operator
#
line class vty
user-role network-operator
#
line con 0
user-role network-admin
set authentication password hash y0MForAn$Cvw/vyAUts1IRfR5FfOI/aFl1yf0mmdsmgSP6HGu
#
line vty 0 63
authentication-mode scheme
user-role network-operator
#
ip route-static 0.0.0.0 0 GigabitEthernet0/0 125.81.1.1
ip route-static 0.0.0.0 0 Dialer1
ip route-static 192.168.8.0 24 192.168.10.2
ip route-static 192.168.9.0 24 192.168.10.2
ip route-static 192.168.10.0 24 192.168.10.2
ip route-static 192.168.11.0 24 192.168.10.2
#
info-center source CFGLOG loghost level informational
#
performance-management
#
ssh server enable
#
ntp-service enable
ntp-service unicast-server ***.***
ntp-service unicast-server registry.h3c.com
ntp-service unicast-server ***.***
ntp-service unicast-server ***.***
#
acl advanced 3001
rule 0 deny ip source 192.168.11.0 0.0.0.255 destination 192.168.4.0 0.0.0.255
rule 5 deny ip source 192.168.11.0 0.0.0.255 destination 192.168.5.0 0.0.0.255
rule 10 deny ip source 192.168.11.0 0.0.0.255 destination 192.168.6.0 0.0.0.255
rule 15 deny ip source 192.168.11.0 0.0.0.255 destination 192.168.7.0 0.0.0.255
rule 20 deny ip source 192.168.11.0 0.0.0.255 destination 192.168.8.0 0.0.0.255
rule 25 deny ip source 192.168.11.0 0.0.0.255 destination 192.168.9.0 0.0.0.255
rule 30 deny ip source 192.168.11.0 0.0.0.255 destination 192.168.10.1 0
rule 35 deny ip source 192.168.11.0 0.0.0.255 destination 192.168.10.2 0
rule 40 deny ip source 192.168.11.0 0.0.0.255 destination 192.168.10.3 0
rule 45 deny ip source 192.168.11.0 0.0.0.255 destination 192.168.10.4 0
rule 50 deny ip source 192.168.11.0 0.0.0.255 destination 192.168.10.5 0
#
acl advanced 3100
description Allow traffic for policy-based routing and exclude internal traffic
rule 0 deny ip source 192.168.0.0 0.0.15.255 destination 192.168.0.0 0.0.15.255
rule 5 permit ip source 192.168.5.0 0.0.0.255
rule 10 permit ip source 192.168.6.0 0.0.0.255
rule 15 permit ip source 192.168.7.0 0.0.0.255
#
acl advanced 3200
description Allow traffic for policy-based routing and exclude internal traffic
rule 0 deny ip source 192.168.0.0 0.0.15.255 destination 192.168.0.0 0.0.15.255
rule 5 permit ip source 192.168.4.0 0.0.0.255
#
acl advanced 3888
rule 5 permit ip
#
acl advanced name GigabitEthernet0/0
rule 9 permit ip source 125.81.1.29 0 destination 125.81.1.29 0
rule 9 comment permit myself
……
#
acl advanced name SWXWSGL
rule 1 permit ip
#
acl advanced name Vlan-interface10
rule 10 permit ip source 192.168.8.87 0
rule 10 comment 允许打印机
……
#
acl mac 4999
rule 10 permit
#
undo password-control aging enable
undo password-control length enable
undo password-control composition enable
undo password-control history enable
password-control length 6
undo password-control complexity user-name check
#
domain system
#
domain default enable system
#
role name level-0
description Predefined level-0 role
#
role name level-1
description Predefined level-1 role
#
role name level-2
description Predefined level-2 role
#
role name level-3
description Predefined level-3 role
#
role name level-4
description Predefined level-4 role
#
role name level-5
description Predefined level-5 role
#
role name level-6
description Predefined level-6 role
#
role name level-7
description Predefined level-7 role
#
role name level-8
description Predefined level-8 role
#
role name level-9
description Predefined level-9 role
#
role name level-10
description Predefined level-10 role
#
role name level-11
description Predefined level-11 role
#
role name level-12
description Predefined level-12 role
#
role name level-13
description Predefined level-13 role
#
role name level-14
description Predefined level-14 role
#
user-group system
#
local-user admin class manage
password hash ……
service-type ssh telnet terminal http https
authorization-attribute user-role level-15
authorization-attribute user-role network-admin
#
local-user system class manage
password hash ……
service-type ftp
service-type ssh telnet terminal http https
authorization-attribute user-role level-15
authorization-attribute user-role network-operator
#
security-enhanced level 1
#
ssl version gm-tls1.1 disable
undo ssl renegotiation disable
undo ssl version ssl3.0 disable
undo ssl version tls1.0 disable
undo ssl version tls1.1 disable
undo ssl version tls1.2 disable
undo ssl version tls1.3 disable
#
netconf soap http enable
#
ip http enable
ip https enable
web idle-timeout 999
web new-style
#
url-filter category custom severity 65535
#
app-profile recordurl
url-filter apply policy recordurl
#
wlan auto-ap enable
#
wlan ap-group default-group
vlan 1
ap-model WA2610H
radio 1
radio enable
service-template h3c
ethernet 1
ethernet 2
ethernet 3
ap-model WA2610H-LI
radio 1
radio enable
service-template h3c
ethernet 1
ethernet 2
ethernet 3
ap-model WA4320-ACN-C
radio 1
radio enable
service-template h3c_5g
radio 2
radio enable
service-template h3c
gigabitethernet 1
ap-model WA4320-ACN-D
radio 1
radio enable
service-template h3c_5g
radio 2
radio enable
service-template h3c
gigabitethernet 1
ap-model WA4320-ACN-E
radio 1
radio enable
service-template h3c_5g
radio 2
radio enable
service-template h3c
gigabitethernet 1
ap-model WA4320H
radio 1
radio enable
service-template h3c_5g
radio 2
radio enable
service-template h3c
gigabitethernet 1
gigabitethernet 2
gigabitethernet 3
gigabitethernet 4
gigabitethernet 5
ap-model WA4320H-SI
radio 1
radio enable
service-template h3c_5g
radio 2
radio enable
service-template h3c
ethernet 1
ethernet 2
ethernet 3
ap-model WA4320i-X
radio 1
radio enable
service-template h3c_5g
radio 2
radio enable
service-template h3c
gigabitethernet 1
gigabitethernet 2
ap-model WA5320
radio 1
radio enable
service-template h3c_5g
radio 2
radio enable
service-template h3c
gigabitethernet 1
gigabitethernet 2
ap-model WA5320-C
radio 1
radio enable
service-template h3c_5g
radio 2
radio enable
service-template h3c
gigabitethernet 1
gigabitethernet 2
ap-model WA5320-C-EI
radio 1
radio enable
service-template h3c_5g
radio 2
radio enable
service-template h3c
gigabitethernet 1
gigabitethernet 2
ap-model WA5320-C-IOT
radio 1
radio enable
service-template h3c_5g
radio 2
radio enable
service-template h3c
gigabitethernet 1
gigabitethernet 2
ap-model WA5320-D
radio 1
radio enable
service-template h3c_5g
radio 2
radio enable
service-template h3c
gigabitethernet 1
ap-model WA5320H
radio 1
radio enable
service-template h3c_5g
radio 2
radio enable
service-template h3c
gigabitethernet 1
gigabitethernet 2
gigabitethernet 3
gigabitethernet 4
ap-model WA5320H-LI
radio 1
radio enable
service-template h3c_5g
radio 2
radio enable
service-template h3c
gigabitethernet 1
gigabitethernet 2
gigabitethernet 3
gigabitethernet 4
gigabitethernet 5
ap-model WA5320X
radio 1
radio enable
service-template h3c_5g
radio 2
radio enable
service-template h3c
gigabitethernet 1
gigabitethernet 2
gigabitethernet 3
ap-model WA5320X-E
radio 1
radio enable
service-template h3c_5g
radio 2
radio enable
service-template h3c
gigabitethernet 1
gigabitethernet 2
ap-model WA5320X-LI
radio 1
radio enable
service-template h3c_5g
radio 2
radio enable
service-template h3c
gigabitethernet 1
gigabitethernet 2
gigabitethernet 3
ap-model WA5320X-SI
radio 1
radio enable
service-template h3c_5g
radio 2
radio enable
service-template h3c
gigabitethernet 1
gigabitethernet 2
gigabitethernet 3
ap-model WA5320i-LI
radio 1
radio enable
service-template h3c_5g
radio 2
radio enable
service-template h3c
gigabitethernet 1
gigabitethernet 2
ap-model WA5530
radio 1
radio enable
service-template h3c_5g
radio 2
radio enable
service-template h3c_5g
radio 3
radio enable
service-template h3c
gigabitethernet 1
gigabitethernet 2
ap-model WA5530-LI
radio 1
radio enable
service-template h3c_5g
radio 2
radio enable
service-template h3c_5g
radio 3
radio enable
service-template h3c
gigabitethernet 1
gigabitethernet 2
ap-model WA5530S
radio 1
radio enable
service-template h3c_5g
radio 2
radio enable
service-template h3c_5g
radio 3
radio enable
service-template h3c
gigabitethernet 1
gigabitethernet 2
#
sslvpn ip address-pool ssl 192.168.172.2 192.168.172.254
#
sslvpn gateway ssl
ip address 125.81.1.29 port 2000
service enable
#
sslvpn context ssl
gateway ssl domain domainip
ip-tunnel interface SSLVPN-AC1
ip-tunnel address-pool ssl mask 255.255.255.0
ip-tunnel dns-server primary 114.114.114.114
ip-route-list 10
include 192.168.4.0 255.255.255.0
include 192.168.5.0 255.255.255.0
include 192.168.6.0 255.255.255.0
include 192.168.7.0 255.255.255.0
include 192.168.8.0 255.255.255.0
policy-group ssl
filter ip-tunnel acl 3888
ip-tunnel access-route ip-route-list 10
timeout idle 1440
#
undo dac log-collect service dpi audit enable
undo dac log-collect service dpi url-filter enable
#
return
- 2025-03-04提问
- 举报
-
(0)

谢谢,我周六来试试。
这几天工作日不敢动。
~~~~~~~~~~~~~~~~~~~~~~~~~~~
V2版的策略路由:
vlan 5 6 7 8 走【线路2】 Dialer1
acl advanced 3100
description Allow traffic for policy-based routing and exclude internal traffic
rule 5 permit ip source 192.168.5.0 0.0.0.255
rule 10 permit ip source 192.168.6.0 0.0.0.255
rule 15 permit ip source 192.168.7.0 0.0.0.255
rule 80 deny ip source 192.168.0.0 0.0.15.255 destination 192.168.0.0 0.0.15.255quit
policy-based-route neiwang node 10
if-match acl 3100
apply output-interface Dialer1
quit
interface Vlan-interface6
ip policy-based-route neiwang
quit
vlan5 和 7 也是这样配置
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
vlan4 走默认【线路1】这条宽带
acl advanced 3200
description Allow traffic for policy-based routing and exclude internal traffic
rule 5 permit ip source 192.168.4.0 0.0.0.255
rule 80 deny ip source 192.168.0.0 0.0.15.255 destination 192.168.0.0 0.0.15.255
quit
policy-based-route neiwang4.0 node 20
if-match acl 3200
apply output-interface GigabitEthernet0/0
quit
interface Vlan-interface4
ip policy-based-route neiwang4.0
quit
- 2025-03-04回答
- 评论(0)
- 举报
-
(0)
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明


好的,感谢感谢