策略路由
- 1关注
- 1收藏,2417浏览
问题描述:
场景是这样,msr5060型号的路由器核心是7006E,然后路由器上做策略路由出去,但是策略应用上以后,打开网页非常慢,上午速度,策略路由取消就回复正常,但是客户的场景只能做策略路由,所有大神解答一下。 对了,核心上连路由做的聚合,本来是动态的现在啊我改成静态的了,下边有配置文件
组网及组网描述:
场景是这样,msr5060型号的路由器核心是7006E,然后路由器上做策略路由出去,但是策略应用上以后,打开网页非常慢,上午速度,策略路由取消就回复正常,但是客户的场景只能做策略路由,所有大神解答一下。 本来是动态的现在啊我改成静态的了,下边有配置文件
- 2020-10-22提问
- 举报
-
(0)
最佳答案

[router]dis cu
#
version 7.1.064, Release 0707P16
#
sysname router
#
telnet server enable
#
qos carl 1 destination-ip-address subnet 192.168.160.0 23 per-address
qos carl 2 destination-ip-address subnet 192.168.170.0 23 per-address
qos carl 3 destination-ip-address subnet 192.168.160.0 23 per-address
qos carl 4 destination-ip-address range 192.168.21.1 to 192.168.24.254 per-address
qos carl 5 destination-ip-address range 192.168.61.1 to 192.168.64.254 per-address
qos carl 6 destination-ip-address range 192.168.101.1 to 192.168.104.254 per-address
#
dialer-group 1 rule ip permit
dialer-group 2 rule ip permit
dialer-group 3 rule ip permit
dialer-group 4 rule ip permit
#
undo nat alg dns
#
dhcp enable
#
dns proxy enable
dns server 202.96.134.133
dns server 114.114.114.114
#
password-recovery enable
#
vlan 1
#
policy-based-route aaa permit node 5
if-match acl 3995
apply default-next-hop 121.15.131.169
#
policy-based-route aaa permit node 10
if-match acl 3999
apply default-output-interface Dialer1
#
policy-based-route aaa permit node 15
if-match acl 3998
apply default-output-interface Dialer2
#
policy-based-route aaa permit node 20
if-match acl 3997
apply default-output-interface Dialer3
#
policy-based-route aaa permit node 25
if-match acl 3996
apply default-output-interface Dialer4
#
controller Cellular2/0/0
#
interface Route-Aggregation1
ip address 192.168.10.1 255.255.255.0
link-aggregation mode dynamic
ip policy-based-route aaa
#
interface Dialer1
mtu 1492
ppp chap password cipher $c$3$RDST1FoMV9OpOn7k7tVtv7QyLP85FUllOpzH
ppp chap user 07551200913543@163.gd
ppp ipcp dns admit-any
ppp ipcp dns request
ppp pap local-user 07551200913543@163.gd password cipher $c$3$mIQMPaDmEtglFGW1LgRXYWHTTmnpUwNMMhoj
dialer bundle enable
dialer-group 1
dialer timer idle 0
ip address ppp-negotiate
tcp mss 1024
nat outbound
#
interface Dialer2
mtu 1492
ppp chap password cipher $c$3$Uegz3AcKXy3a5/uHtKVD0thTm+Nt7M5p0iN/
ppp ipcp dns admit-any
ppp ipcp dns request
ppp pap local-user 075506827101@163.gd password cipher $c$3$iJ4JSlVxeq0JB0GMdpQOjuTXGk2Lpz5J61CS
dialer bundle enable
dialer-group 2
dialer timer idle 0
ip address ppp-negotiate
tcp mss 1024
nat outbound
#
interface Dialer3
mtu 1492
ppp ipcp dns admit-any
ppp ipcp dns request
ppp pap local-user 07551200909992@163.gd password cipher $c$3$iJ+lRMvlKdLsMfipBUU5LkVY5qYHQk27VUWr
dialer bundle enable
dialer-group 3
dialer timer idle 0
ip address ppp-negotiate
tcp mss 1024
nat outbound
#
interface Dialer4
mtu 1492
ppp ipcp dns admit-any
ppp ipcp dns request
ppp pap local-user 07554201886857@163.gd password cipher $c$3$dVY6tJBfk28m69bUrQ6t4CHrDVZ6poKb67V1
dialer bundle enable
dialer-group 4
dialer timer idle 0
ip address ppp-negotiate
tcp mss 1024
nat outbound
#
interface NULL0
#
interface GigabitEthernet2/0/0
port link-mode route
combo enable copper
ip address 121.15.131.171 255.255.255.248
ip last-hop hold
nat outbound
nat server protocol tcp global current-interface 88 inside 192.168.5.56 80
nat server protocol tcp global current-interface 3890 inside 192.168.5.56 389
nat server protocol tcp global current-interface 6360 inside 192.168.5.56 636
nat server protocol tcp global current-interface 8888 inside 192.168.5.56 8888
nat server protocol tcp global current-interface 53389 inside 192.168.5.56 3389
#
interface GigabitEthernet2/0/1
port link-mode route
combo enable copper
mtu 1492
tcp mss 1024
ip last-hop hold
pppoe-client dial-bundle-number 2
#
interface GigabitEthernet2/0/2
port link-mode route
combo enable copper
mtu 1492
tcp mss 1024
ip last-hop hold
pppoe-client dial-bundle-number 1
#
interface GigabitEthernet2/0/3
port link-mode route
combo enable copper
mtu 1492
tcp mss 1024
ip last-hop hold
pppoe-client dial-bundle-number 3
#
interface GigabitEthernet2/0/4
port link-mode route
combo enable copper
mtu 1492
tcp mss 1024
ip last-hop hold
pppoe-client dial-bundle-number 4
#
interface GigabitEthernet2/0/5
port link-mode route
combo enable copper
#
interface GigabitEthernet2/0/6
port link-mode route
combo enable copper
port link-aggregation group 1
#
interface GigabitEthernet2/0/7
port link-mode route
combo enable copper
port link-aggregation group 1
#
interface GigabitEthernet2/0/8
port link-mode route
combo enable copper
port link-aggregation group 1
#
interface GigabitEthernet2/0/9
port link-mode route
combo enable copper
port link-aggregation group 1
#
interface M-GigabitEthernet0
#
scheduler logfile size 16
#
line class console
user-role network-admin
#
line class tty
user-role network-operator
#
line class vty
user-role network-operator
#
line con 0
user-role network-admin
#
line vty 0 63
authentication-mode scheme
user-role network-operator
#
ip route-static 192.168.0.0 16 192.168.10.2
#
acl advanced 3000
rule 10 permit ip source 192.168.100.0 0.0.3.255
#
acl advanced 3995
rule 0 permit ip source 192.168.5.0 0.0.0.255
rule 5 permit ip source 192.168.23.60 0
rule 10 permit ip source 192.168.23.61 0
rule 15 permit ip source 192.168.23.62 0
rule 20 permit ip source 192.168.23.63 0
rule 25 permit ip source 192.168.23.64 0
rule 30 permit ip source 192.168.23.65 0
rule 35 permit ip source 192.168.23.66 0
rule 40 permit ip source 192.168.23.67 0
rule 45 permit ip source 192.168.23.68 0
rule 50 permit ip source 192.168.23.69 0
rule 55 permit ip source 192.168.23.70 0
rule 60 permit ip source 192.168.24.60 0
rule 65 permit ip source 192.168.24.61 0
rule 70 permit ip source 192.168.24.62 0
rule 75 permit ip source 192.168.24.63 0
rule 80 permit ip source 192.168.24.64 0
rule 85 permit ip source 192.168.24.65 0
rule 90 permit ip source 192.168.24.66 0
rule 95 permit ip source 192.168.24.67 0
rule 100 permit ip source 192.168.24.68 0
rule 105 permit ip source 192.168.24.69 0
rule 110 permit ip source 192.168.24.70 0
#
acl advanced 3996
rule 0 permit ip source 192.168.150.0 0.0.0.255
rule 5 permit ip source 192.168.170.0 0.0.0.255
#
acl advanced 3997
rule 0 permit ip source 192.168.101.0 0.0.0.255
rule 5 permit ip source 192.168.102.0 0.0.0.255
rule 10 permit ip source 192.168.103.0 0.0.0.255
rule 15 permit ip source 192.168.104.0 0.0.0.255
#
acl advanced 3998
rule 0 permit ip source 192.168.61.0 0.0.0.255
rule 5 permit ip source 192.168.62.0 0.0.0.255
rule 10 permit ip source 192.168.63.0 0.0.0.255
rule 15 permit ip source 192.168.64.0 0.0.0.255
rule 20 permit ip source 192.168.160.0 0.0.0.255
#
acl advanced 3999
rule 0 permit ip source 192.168.21.0 0.0.0.255
rule 5 permit ip source 192.168.22.0 0.0.0.255
rule 60 permit ip source 192.168.23.0 0.0.0.255
rule 120 permit ip source 192.168.24.0 0.0.0.255
rule 125 permit ip source 192.168.25.0 0.0.0.255
#
domain system
#
domain default enable system
#
role name level-0
description Predefined level-0 role
#
role name level-1
description Predefined level-1 role
#
role name level-2
description Predefined level-2 role
#
role name level-3
description Predefined level-3 role
#
role name level-4
description Predefined level-4 role
#
role name level-5
description Predefined level-5 role
#
role name level-6
description Predefined level-6 role
#
role name level-7
description Predefined level-7 role
#
role name level-8
description Predefined level-8 role
#
role name level-9
description Predefined level-9 role
#
role name level-10
description Predefined level-10 role
#
role name level-11
description Predefined level-11 role
#
role name level-12
description Predefined level-12 role
#
role name level-13
description Predefined level-13 role
#
role name level-14
description Predefined level-14 role
#
user-group system
#
local-user admin class manage
password hash $h$6$TIvYzbtAa9yTiGt7$OCG+9VsxF6nt2AJPSW6zpDfICMJXqeL/duNZpELJ49z8wAda5TsyrJqS1o939DBohiNfuO14rETBr8sLsw+oZQ==
service-type ssh telnet terminal http https
authorization-attribute user-role network-admin
authorization-attribute user-role network-operator
#
return
- 2020-10-22回答
- 评论(0)
- 举报
-
(0)

看下这个案例,重新做一下,没看到你PBR相关配置
基于报文源地址的转发策略路由配置举例
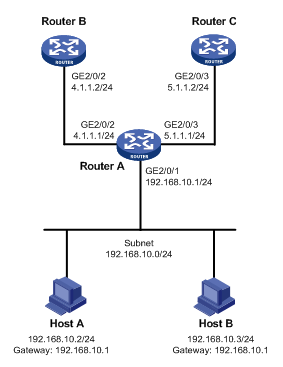
1. 组网需求
通过策略路由控制从Router A的以太网接口GigabitEthernet2/0/1接收的报文:
· 源地址为192.168.10.2的报文以4.1.1.2/24作为下一跳IP地址;
· 其它源地址的报文以5.1.1.2/24作为下一跳IP地址。
2. 组网图
3. 配置步骤
# 配置接口GigabitEthernet2/0/2和GigabitEthernet2/0/3的IP地址。
[RouterA] interface gigabitethernet 2/0/2
[RouterA-GigabitEthernet2/0/2] ip address 4.1.1.1 24
[RouterA-GigabitEthernet2/0/2] quit
[RouterA] interface gigabitethernet 2/0/3
[RouterA-GigabitEthernet2/0/3] ip address 5.1.1.1 24
[RouterA-GigabitEthernet2/0/3] quit
# 定义访问控制列表ACL 2000,用来匹配源地址为192.168.10.2的报文。
[RouterA-acl-ipv4-basic-2000] rule 10 permit source 192.168.10.2 0
[RouterA-acl-ipv4-basic-2000] quit
# 定义0号节点,指定所有源地址为192.168.10.2的报文的下一跳为4.1.1.2。
[RouterA] policy-based-route aaa permit node 0
[RouterA-pbr-aaa-0] if-match acl 2000
[RouterA-pbr-aaa-0] apply next-hop 4.1.1.2
[RouterA-pbr-aaa-0] quit
[RouterA] policy-based-route aaa permit node 1
[RouterA-pbr-aaa-1] apply next-hop 5.1.1.2
[RouterA-pbr-aaa-1] quit
# 在以太网接口GigabitEthernet2/0/1上应用转发策略路由,处理此接口接收的报文。
[RouterA] interface gigabitethernet 2/0/1
[RouterA-GigabitEthernet2/0/1] ip address 192.168.10.1 24
[RouterA-GigabitEthernet2/0/1] ip policy-based-route aaa
[RouterA-GigabitEthernet2/0/1] quit
# 配置GigabitEthernet接口的IP地址。
[RouterB] interface gigabitethernet 2/0/2
[RouterB-GigabitEthernet2/0/2] ip address 4.1.1.2 24
[RouterB-GigabitEthernet2/0/2] quit
# 配置到网段192.168.10.0/24的静态路由。
[RouterB] ip route-static 192.168.10.0 24 4.1.1.1
# 配置GigabitEthernet接口的IP地址。
[RouterC] interface gigabitethernet 2/0/3
[RouterC-GigabitEthernet2/0/3] ip address 5.1.1.2 24
[RouterC-GigabitEthernet2/0/3] quit
# 配置到网段192.168.10.0/24的静态路由。
[RouterC] ip route-static 192.168.10.0 24 5.1.1.1
4. 验证配置
将Host A的IP地址配置为192.168.10.2/24,网关地址配置为192.168.10.1;将Host B的IP地址配置为192.168.10.3/24,网关地址配置为192.168.10.1。
从Host A上ping Router B,结果成功。
从Host B上ping Router B,结果失败。
从Host A上ping Router C,结果失败。
从Host B上ping Router C,结果成功。
以上结果可证明:从Router A的以太网接口GigabitEthernet2/0/1接收的源地址为192.168.10.2的报文的下一跳为4.1.1.2,所以Host A能ping通Router B,源地址为192.168.10.3的下一跳5.1.1.2,所以Host B能ping通Router C,由此表明策略路由设置成功。
- 2020-10-22回答
- 评论(0)
- 举报
-
(0)
暂无评论
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明


暂无评论