问题描述:
802.1x 认证成功,但下发的vlan 交换机 s5130 不动作,仍旧使用vlan1
debug radius 可以观察到服务器下发了三条属性,vlan是104
组网及组网描述:
freeradius 3 认证是成功
s5130 接收到了 用户属性
*Apr 27 15:04:32:468 2021 H3C SW RADIUS/7/PACKET:
Framed-Protocol=PPP
Framed-Compression=Van-Jacobson-TCP-IP
Tunnel-Type:0=VLAN
Tunnel-Medium-Type:0=IEEE-802
Tunnel-Private-Group-Id:0="104"
EAP-Message=0x010e00061920
Message-Authenticator=0xa5194a6a10adef886f794e518d95353b
State=0x38090a8d390713640f536e1bad07c576
交换机的log
%Apr 27 15:10:54:305 2021 H3C SW DOT1X/6/DOT1X_LOGIN_SUCC: -IfName=GigabitEthernet1/0/41-MACAddr=8c04-ba1a-e77a-AccessVLANID=1-AuthorizatiOnVLANID=1-Username=test-win10; User passed 802.1X authentication and came online.
显示dot1x 如下
dis dot1x
Global 802.1X parameters:
802.1X authentication : Enabled
EAP authentication : Enabled
Max-tx period : 30 s
Handshake period : 15 s
Quiet timer : Disabled
Quiet period : 60 s
Supp timeout : 30 s
Server timeout : 100 s
Reauth period : 3600 s
Max auth requests : 2
User aging period for Auth-Fail VLAN : 1000 s
User aging period for critical VLAN : 1000 s
User aging period for guest VLAN : 1000 s
EAD assistant function : Disabled
EAD timeout : 30 min
Domain delimiter : @
Max EAP-TLS-fragment (to-server) : N/A
Online 802.1X wired users : 1
GigabitEthernet1/0/41 is link-up
802.1X authentication : Enabled
Handshake : Disabled
Handshake reply : Disabled
Handshake security : Disabled
Unicast trigger : Enabled
Periodic reauth : Disabled
Port role : Authenticator
Authorization mode : Auto
Port access control : Port-based
Multicast trigger : Disabled
Mandatory auth domain : Not configured
Guest VLAN : Not configured
Auth-Fail VLAN : Not configured
Critical VLAN : Not configured
Critical voice VLAN : Disabled
Add Guest VLAN delay : Disabled
Re-auth server-unreachable : Logoff
Max online users : 4294967295
User IP freezing : Disabled
Reauth period : 0 s
Send Packets Without Tag : Disabled
Max Attempts Fail Number : 0
User aging : Enabled
Server-recovery online-user-sync : Disabled
Auth-Fail EAPOL : Disabled
Critical EAPOL : Disabled
Discard duplicate EAPOL-Start : No
dis dot con
Total connections: 1
Slot ID: 1
User MAC address: 8c04-ba1a-e77a
Access interface: GigabitEthernet1/0/41
Username: test-win10
User access state: Successful
Authentication domain: sjgs
Authentication method: EAP
Initial VLAN: 1
Authorization untagged VLAN: N/A
Authorization tagged VLAN list: N/A
Authorization ACL number/name: N/A
Authorization user profile: test
Authorization CAR: N/A
Authorization URL: N/A
Termination action: Default
Session timeout period: N/A
Online from: 2021/04/27 15:18:28
Online duration: 0h 15m 12s
交换机信息
BOARD TYPE: S5130S-52S-LI
Release Version: H3C S5130S-52S-LI-6326
交换机 配置:
dot1x
dot1x authentication-method eap
dot1x access-user log enable abnormal-logoff failed-login normal-logoff successful-login
vlan 1
#
vlan 2 to 4094
interface GigabitEthernet1/0/41
dot1x
undo dot1x handshake
undo dot1x multicast-trigger
dot1x port-method portbased
dot1x unicast-trigger
#
radius scheme sjgs52
primary authentication 192.168.136.52 key cipher
primary accounting 192.168.136.52 key cipher
user-name-format without-domain
#
radius scheme system
user-name-format without-domain
#
domain sjgs
authorization-attribute user-profile test
authentication lan-access radius-scheme sjgs52
authorization lan-access radius-scheme sjgs52
accounting lan-access radius-scheme sjgs52
- 2021-04-27提问
- 举报
-
(0)
最佳答案

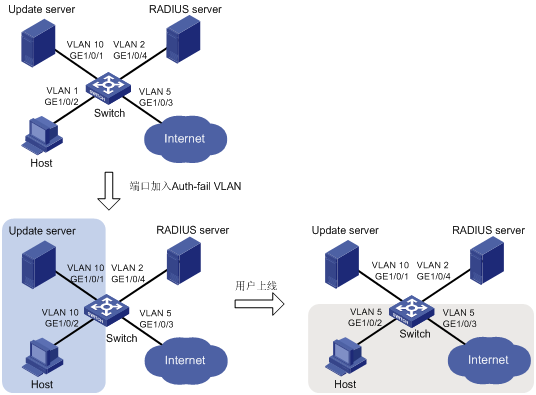
组网需求
如图15所示,主机Host通过802.1X认证接入网络,认证服务器为RADIUS服务器。Host接入Switch的端口在VLAN 1内;认证服务器在VLAN 2内;Update Server是用于客户端等软件下载和升级的服务器,在VLAN 10内;Switch连接Internet网络的端口在VLAN 5内。现有如下组网需求:
· 若802.1X用户认证失败,Host可以访问Update Server进行软件升级等操作。
· 若802.1X用户认证成功,Host可以访问Internet。
图15 Auth-Fail VLAN及VLAN下发组网图
1.5.3 配置思路
· 为实现802.1X用户认证失败后可以访问Update Server进行软件升级等操作,需配置Host接入Switch的端口加入Auth-Fail VLAN(VLAN 10)。
· 为实现802.1X用户认证成功后可以访问Internet,需配置认证服务器对于认证成功用户下发VLAN 5,此时Host和连接Internet网络的端口在同一VLAN(VLAN 5)内。
1.5.4 配置注意事项
· 如果用户端设备发出的是携带Tag的数据流,且接入端口上使能了802.1X认证并配置了Auth-Fail VLAN,为保证各种功能的正常使用,请为Voice VLAN、端口的缺省VLAN和802.1X的Auth-Fail VLAN分配不同的VLAN ID。
· 如果某个VLAN被指定为Super VLAN,则该VLAN不能被指定为某个端口的Auth-Fail VLAN;同样,如果某个VLAN被指定为某个端口的Auth-Fail VLAN,则该VLAN不能被指定为Super VLAN。
1.5.5 配置步骤
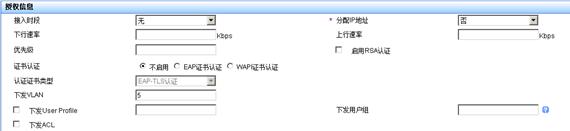
1. RADIUS服务器上的配置(以iMC服务器为例)
iMC服务器上的配置与“1.3 802.1X用户认证典型配置”类似,
仅需要在“增加接入规则”时,配置下发“VLAN5”,如图16。
2. 接入设备Switch的配置
(1) 创建VLAN并将端口加入对应VLAN
<Switch> system-view
[Switch] vlan 1
[Switch-vlan1] port gigabitethernet 1/0/2
[Switch-vlan1] quit
[Switch] vlan 10
[Switch-vlan10] port gigabitethernet 1/0/1
[Switch-vlan10] quit
[Switch] vlan 2
[Switch-vlan2] port gigabitethernet 1/0/4
[Switch-vlan2] quit
[Switch] vlan 5
[Switch-vlan5] port gigabitethernet 1/0/3
[Switch-vlan5] quit
(2) 配置RADIUS方案
# 创建RADIUS方案radius1并进入其视图。
[Switch] radius scheme radius1
# 配置主认证/授权RADIUS服务器及其共享密钥。
[Switch-radius-radius1] primary authentication 10.11.1.1 1812
[Switch-radius-radius1] key authentication aabbcc
# 设置服务类型为extended.
[Switch-radius-radius1] server-type extended
# 配置发送给RADIUS服务器的用户名携带域名。
[Switch-radius-radius1] user-name-format with-domain
[Switch-radius-radius1] quit
(3) 配置ISP域
# 创建域test并进入其视图。
[Switch] domaim test
# 配置802.1X用户使用RADIUS方案radius1进行认证、授权。
[Switch-isp-test] authentication lan-access radius-scheme radius1
[Switch-isp-test] authorization lan-access radius-scheme radius1
[Switch-isp-test] quit
# 配置域test为缺省用户域。
[Switch] domain default enable test
(4) 配置802.1X
# 开启指定端口的802.1X特性。
[Switch] interface gigabitethernet 1/0/2
[Switch-GigabitEthernet1/0/2] dot1x
# 配置端口上进行接入控制的方式为portbased。
[Switch-GigabitEthernet1/0/2] dot1x port-method portbased
# 配置端口的授权状态为auto。(此配置可选,端口的授权状态缺省为auto)
[Switch-GigabitEthernet1/0/2] dot1x port-control auto
# 配置端口的Auth-Fail VLAN。
[Switch-GigabitEthernet1/0/2] dot1x auth-fail vlan 10
[Switch-GigabitEthernet1/0/2] quit
# 开启全局802.1X特性。
[Switch] dot1x
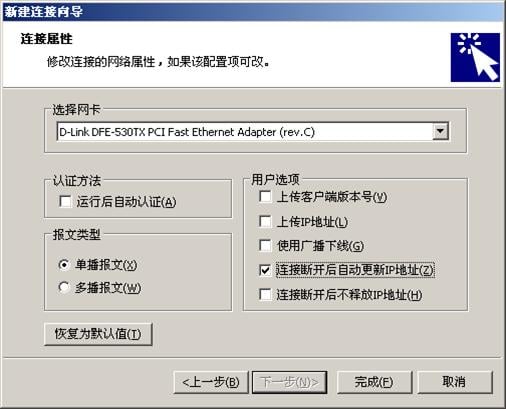
3. 接入用户上的配置
具体配置和“1.2 802.1X用户认证典型配置”中的iNode客户端配置相似,仅需要在设置“连接属性”时,选则“连接断开后自动更新IP地址”,如图17所示。
图17 802.1X连接属性配置示意图
1.5.6 验证配置
通过命令display dot1x interface gigabitethernet 1/0/2可以查看端口GigabitEthernet1/0/2上Auth-Fail VLAN的配置情况。
若端口GE1/0/2下有用户802.1X认证失败(例如密码错误),则通过命令display vlan 10可以查看到端口GE1/0/2加入了配置的Auth-Fail VLAN。
若端口GE1/0/2下的用户802.1X认证成功,则认证服务器下发VLAN5,通过display interface gigabitethernet 1/0/2可以看到用户接入的端口GE1/0/2加入了认证服务器下发的VLAN 5中。
1.5.7 配置文件
![]()
S5500-SI系列交换机不支持port link-mode bridge命令。
#
domain default enable test
#
dot1x
#
vlan 1
#
vlan 2
#
vlan 5
#
vlan 10
#
radius scheme radius1
server-type extended
primary authentication 10.1.1.1
key authentication cipher $c$3$LAV0oGNaM9Z/CuVcWONBH4xezu48Agh5aQ==
#
domain test
authentication lan-access radius-scheme radius1
authorization lan-access radius-scheme radius1
access-limit disable
state active
idle-cut disable
self-service-url disable
#
interface GigabitEthernet1/0/1
port link-mode bridge
port access vlan 10
#
interface GigabitEthernet1/0/2
port link-mode bridge
dot1x auth-fail vlan 10
dot1x port-method portbased
dot1x
#
interface GigabitEthernet1/0/3
port link-mode bridge
port access vlan 5
#
interface GigabitEthernet1/0/4
port link-mode bridge
port access vlan 2
#
- 2021-04-27回答
- 评论(0)
- 举报
-
(0)


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明


暂无评论