F1060 IPSEC 协商不成功
- 1关注
- 1收藏,2264浏览
最佳答案

你拓扑图上写的是PC地址为192.168.2.1,然后配置里写的是防火墙接口地址(应该就是PC的网关)为192.168.2.1,这地址写串了吧。
我用你的配置是可以的。
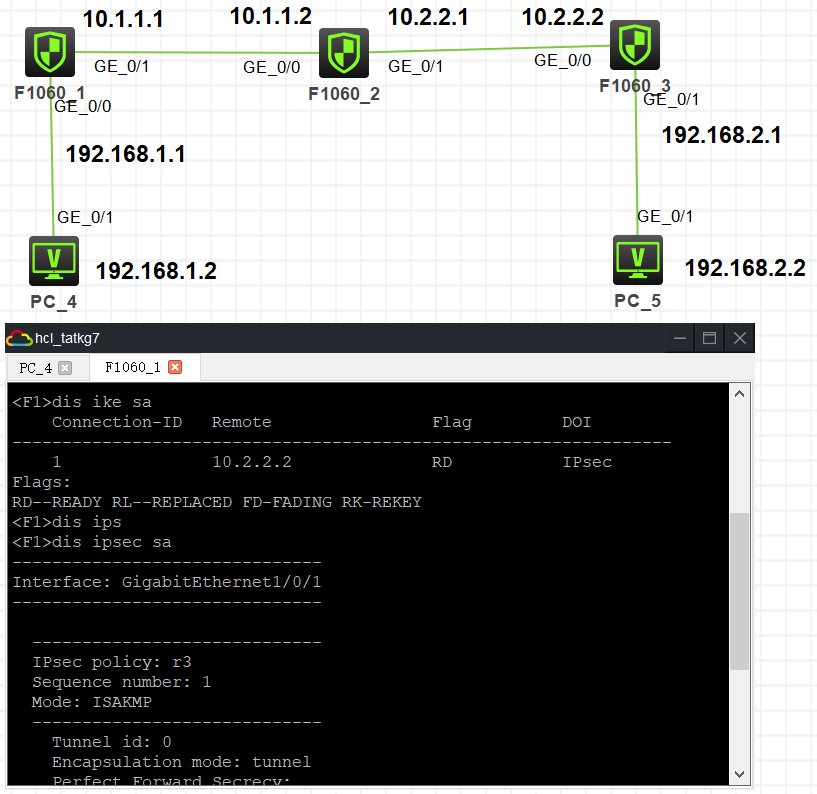
<F1> interface GigabitEthernet1/0/0 port link-mode route combo enable copper ip address 192.168.1.1 255.255.255.0 # interface GigabitEthernet1/0/1 port link-mode route combo enable copper ip address 10.1.1.1 255.255.255.0 ipsec apply policy r3 # security-zone name Trust import interface GigabitEthernet1/0/1 # security-zone name Untrust import interface GigabitEthernet1/0/0 # zone-pair security source Any destination Any packet-filter 3000 # ip route-static 0.0.0.0 0 10.1.1.2 # acl advanced 3000 rule 0 permit ip # acl advanced 3100 rule 0 permit ip source 192.168.1.0 0.0.0.255 destination 192.168.2.0 0.0.0.255 # ipsec transform-set r3 esp encryption-algorithm aes-cbc-128 esp authentication-algorithm sha1 # ipsec policy r3 1 isakmp transform-set r3 security acl 3100 remote-address 10.2.2.2 ike-profile r3 # ike profile r3 keychain r3 local-identity address 10.1.1.1 match remote identity address 10.2.2.2 255.255.255.255 proposal 1 # ike proposal 1 encryption-algorithm aes-cbc-128 # ike keychain r3 pre-shared-key address 10.2.2.2 255.255.255.255 key cipher $c$3$vDDON4zDv7fesDVgysVm3/mtPigNhxQz #
<F3> interface GigabitEthernet1/0/0 port link-mode route combo enable copper ip address 10.2.2.2 255.255.255.0 ipsec apply policy r3 # interface GigabitEthernet1/0/1 port link-mode route combo enable copper ip address 192.168.2.1 255.255.255.0 # security-zone name Trust import interface GigabitEthernet1/0/1 # security-zone name Untrust import interface GigabitEthernet1/0/0 # zone-pair security source Any destination Any packet-filter 3000 # ip route-static 0.0.0.0 0 10.2.2.1 # acl advanced 3000 rule 0 permit ip # acl advanced 3100 rule 0 permit ip source 192.168.2.0 0.0.0.255 destination 192.168.1.0 0.0.0.255 # ipsec transform-set r3 esp encryption-algorithm aes-cbc-128 esp authentication-algorithm sha1 # ipsec policy r3 1 isakmp transform-set r3 security acl 3100 remote-address 10.1.1.1 ike-profile r3 # ike profile r3 keychain r3 local-identity address 10.2.2.2 match remote identity address 10.1.1.1 255.255.255.255 proposal 1 # ike proposal 1 encryption-algorithm aes-cbc-128 # ike keychain r3 pre-shared-key address 10.1.1.1 255.255.255.255 key cipher $c$3$vcpye8Lc0xx7ISFTDFv6jVx8Ja5HJsfE #
- 2021-07-08回答
- 评论(0)
- 举报
-
(0)

您好,请知:
IPSEC VPN故障排查:
1、检查公网地址的连通性
2、检查ipsec acl是否配置正确(两端ACL以互为镜像的方式配置)
3、检查ike keychain/ike profile 协商参数配置是否正确(工作模式、keychain、identity、本端/对端隧道地址或隧道名称、NAT穿越功能v7自适应)
4、检查ipsec proposal(v5平台) /ipsec transform-set(v7平台)参数两端是否一致(封装模式、安全协议、验证算法、加密算法)
5、检查设备是否创建ipsec策略,并加载协商参数(acl、ike profile 、ipsec transform-set、对端隧道IP)
6、检查ipsec策略是否应用在正确的接口上
IPSEC排查命令:
1、disp ipsec policy
2、disp acl
3、dis cu conf ike-profile
4、dis cu conf ike-keychain
5、display ike proposal
6、display ipsec transform-set
7、disp ike sa (verbose)
8、disp ipsec sa
9、reset ipsec sa
10、reset ike sa
- 2021-07-07回答
- 评论(0)
- 举报
-
(0)
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明

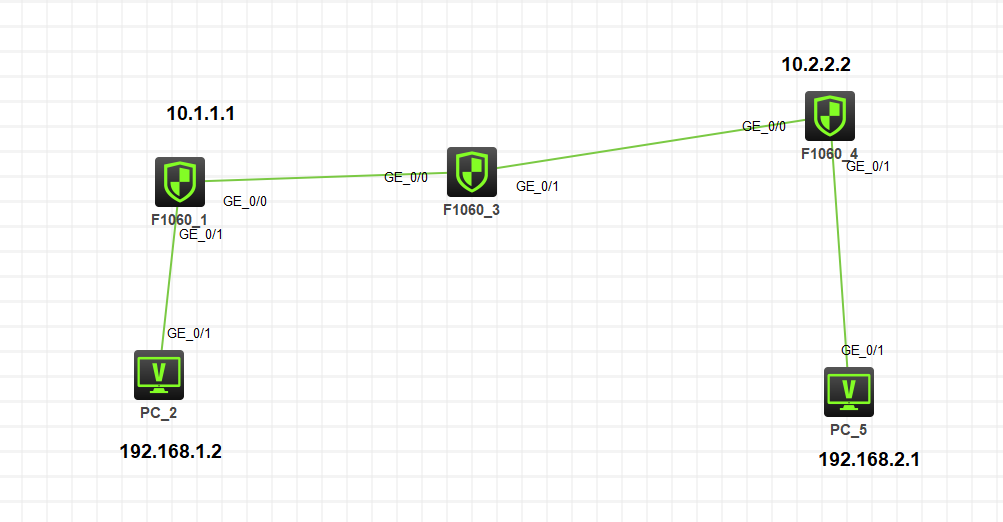
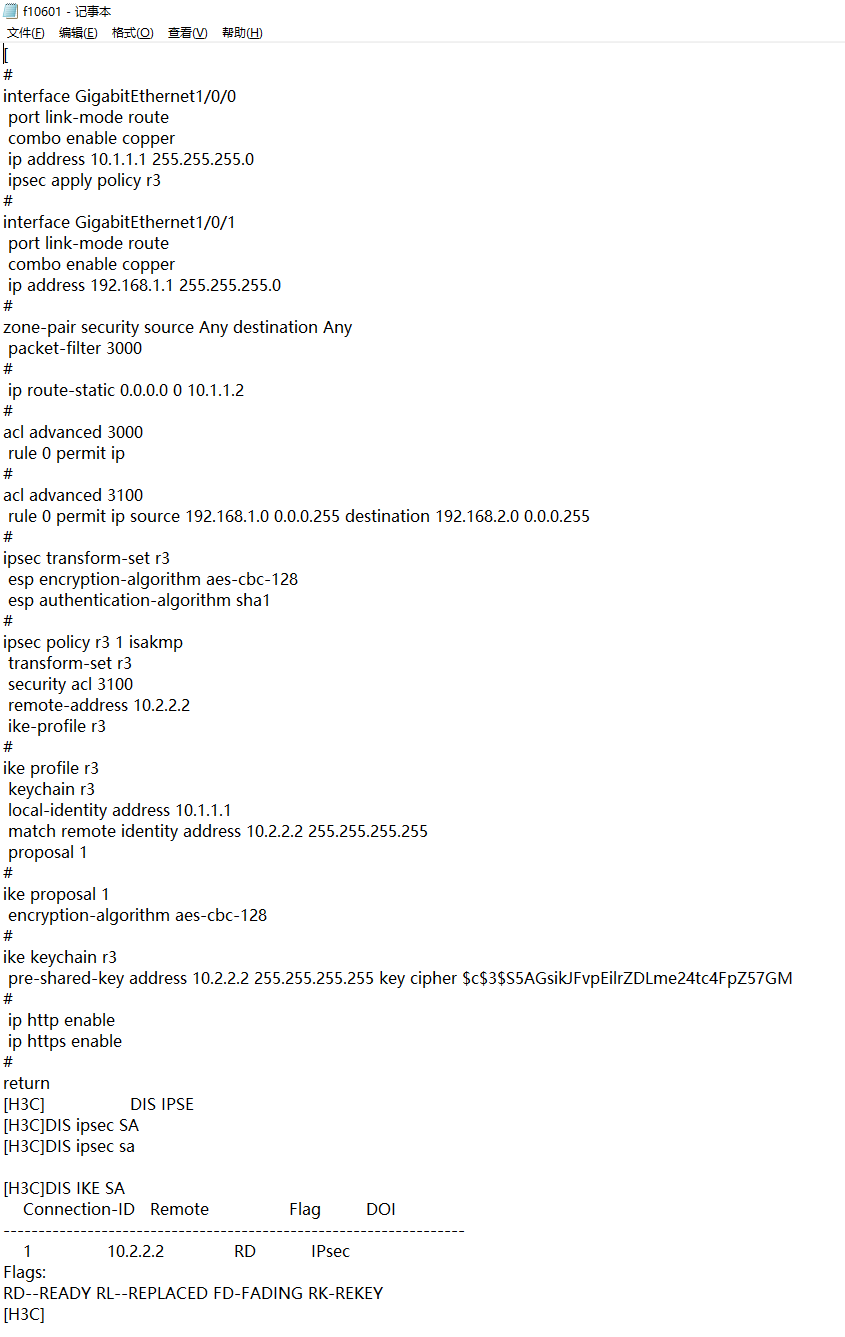
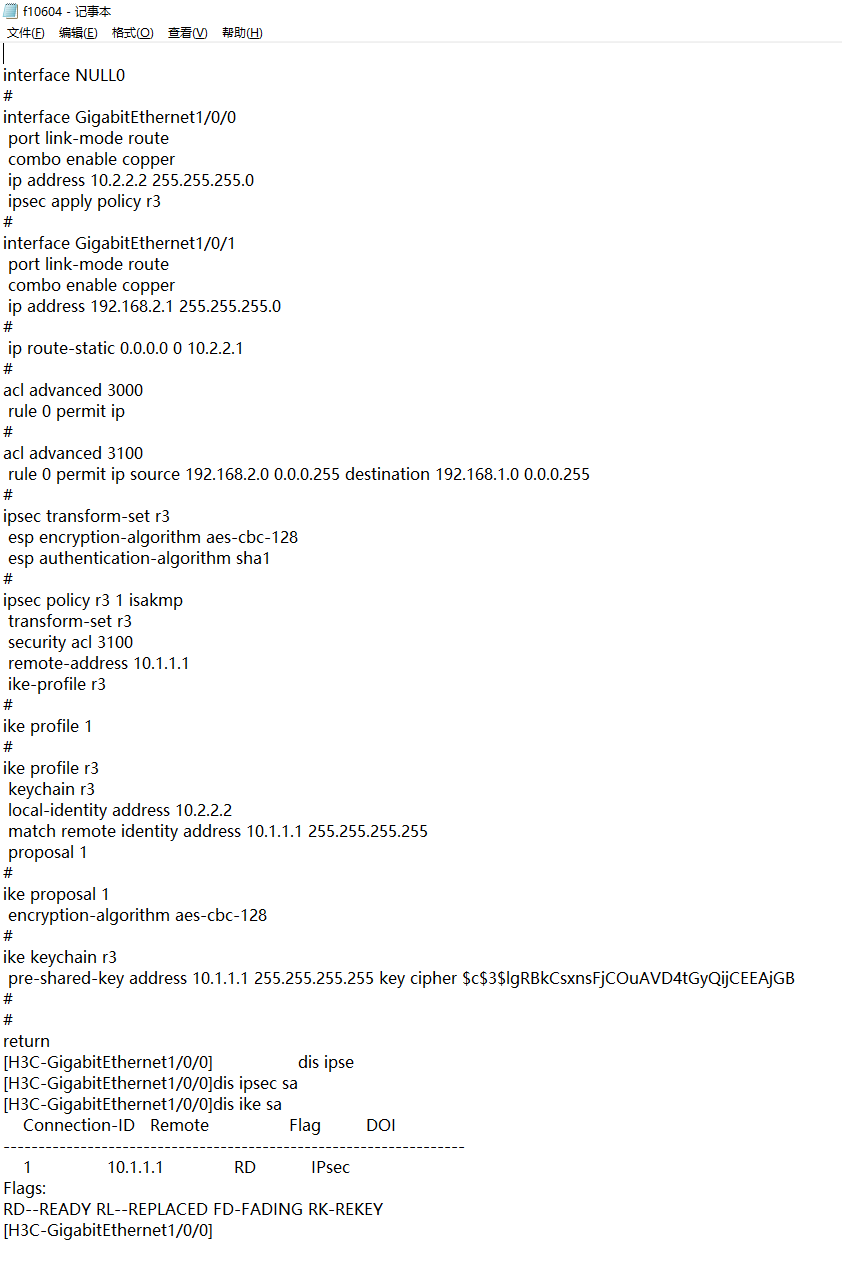








看配置也没什么问题啊 密钥也一样