SecPath U200-M和ER5200 G2组IPSEC VPN,ER会自动掉线
- 0关注
- 1收藏,2374浏览
问题描述:
惠州是总部,用的是U200-M,分支为深圳和杭州,都是用的ER5200 G2,深圳那边会自动掉线,请帮忙看下是哪里出问题了。谢谢!
组网及组网描述:
总部-U200-M配置(这里有另一端杭州的配置,因为设备都是ER5200G2,深圳用的是主模式,杭州用的是野蛮模式):
#
ike local-name huizhou
#
acl number 3080
description ipsec vpn to shenzhen
rule 10 permit ip source 192.168.10.0 0.0.0.255 destination 192.168.80.0 0.0.0.255
rule 20 permit ip source 192.168.20.0 0.0.0.255 destination 192.168.80.0 0.0.0.255
acl number 3090
description ipsec vpn to hangzhou
rule 10 permit ip source 192.168.10.0 0.0.0.255 destination 192.168.90.0 0.0.0.255
rule 20 permit ip source 192.168.20.0 0.0.0.255 destination 192.168.90.0 0.0.0.255
rule 40 permit ip source 192.168.40.0 0.0.0.255 destination 192.168.90.0 0.0.0.255
#
ike dpd 1
#
ike peer hangzhou
exchange-mode aggressive
pre-shared-key cipher +MGS6bX9XT8=
id-type name
remote-name hangzhou
local-address x.x.x.x
dpd 1
#
ike peer shenzhen
pre-shared-key cipher +MGS6bX9XT8=
remote-name shenzhen
remote-address x.x.x.x
local-address x.x.x.x
dpd 1
#
ipsec proposal 1
#
ipsec policy center 80 isakmp
security acl 3080
ike-peer shenzhen
proposal 1
#
ipsec policy center 90 isakmp
security acl 3090
ike-peer hangzhou
proposal 1
#
interface GigabitEthernet0/1
port link-mode route
description this port is link to China Telecom's Fiber Converter
nat outbound 3003
ip address x.x.x.x
ipsec policy center
[U200-M]dis ike dpd 1
---------------------------
IKE dpd: 1
references: 2
interval-time: 10
time_out: 5
---------------------------
[U200-M]dis ipsec prop
[U200-M]dis ipsec proposal 1
IPsec proposal name: 1
encapsulation mode: tunnel
transform: esp-new
ESP protocol: authentication md5-hmac-96, encryption des
[U200-M]dis ike sa
total phase-1 SAs: 2
connection-id peer flag phase doi
----------------------------------------------------------
1197 x.x.x.x RD 1 IPSEC
1209 x.x.x.x RD 2 IPSEC
1206 x.x.x.x RD 1 IPSEC
1211 x.x.x.x RD 2 IPSEC
1210 x.x.x.x RD 2 IPSEC
1213 x.x.x.x RD 2 IPSEC
1212 x.x.x.x RD 2 IPSEC
flag meaning
RD--READY ST--STAYALIVE RL--REPLACED FD--FADING TO--TIMEOUT
[U200-M]dis ipsec sa
===============================
Interface: GigabitEthernet0/1
path MTU: 1500
===============================
-----------------------------
IPsec policy name: "center"
sequence number: 80
mode: isakmp
-----------------------------
connection id: 196
encapsulation mode: tunnel
perfect forward secrecy: None
tunnel:
local address: x.x.x.x
remote address: x.x.x.x
Flow :
sour addr: 192.168.10.0/255.255.255.0 port: 0 protocol: IP
dest addr: 192.168.80.0/255.255.255.0 port: 0 protocol: IP
[inbound ESP SAs]
spi: 3507750634 (0xd11406ea)
proposal: ESP-ENCRYPT-DES ESP-AUTH-MD5
sa duration (kilobytes/sec): 1843200/3600
sa remaining duration (kilobytes/sec): 1834492/1172
max received sequence-number: 69472
anti-replay check enable: Y
anti-replay window size: 32
udp encapsulation used for nat traversal: N
[outbound ESP SAs]
spi: 225714323 (0xd742093)
proposal: ESP-ENCRYPT-DES ESP-AUTH-MD5
sa duration (kilobytes/sec): 1843200/3600
sa remaining duration (kilobytes/sec): 1827372/1172
max sent sequence-number: 67963
udp encapsulation used for nat traversal: N
-----------------------------
IPsec policy name: "center"
sequence number: 80
mode: isakmp
-----------------------------
connection id: 197
encapsulation mode: tunnel
perfect forward secrecy: None
tunnel:
local address: x.x.x.x
remote address: x.x.x.x
Flow :
sour addr: 192.168.20.0/255.255.255.0 port: 0 protocol: IP
dest addr: 192.168.80.0/255.255.255.0 port: 0 protocol: IP
[inbound ESP SAs]
spi: 2216410771 (0x841bbe93)
proposal: ESP-ENCRYPT-DES ESP-AUTH-MD5
sa duration (kilobytes/sec): 1843200/3600
sa remaining duration (kilobytes/sec): 1841773/1171
max received sequence-number: 19092
anti-replay check enable: Y
anti-replay window size: 32
udp encapsulation used for nat traversal: N
[outbound ESP SAs]
spi: 225714322 (0xd742092)
proposal: ESP-ENCRYPT-DES ESP-AUTH-MD5
sa duration (kilobytes/sec): 1843200/3600
sa remaining duration (kilobytes/sec): 1842075/1171
max sent sequence-number: 16857
udp encapsulation used for nat traversal: N
-----------------------------
IPsec policy name: "center"
sequence number: 90
mode: isakmp
-----------------------------
connection id: 200
encapsulation mode: tunnel
perfect forward secrecy: None
tunnel:
local address: x.x.x.x
remote address: x.x.x.x
Flow :
sour addr: 192.168.10.0/255.255.255.0 port: 0 protocol: IP
dest addr: 192.168.90.0/255.255.255.0 port: 0 protocol: IP
[inbound ESP SAs]
spi: 1592023955 (0x5ee45b93)
proposal: ESP-ENCRYPT-DES ESP-AUTH-MD5
sa duration (kilobytes/sec): 1843200/3600
sa remaining duration (kilobytes/sec): 1838075/768
max received sequence-number: 11495
anti-replay check enable: Y
anti-replay window size: 32
udp encapsulation used for nat traversal: N
[outbound ESP SAs]
spi: 2753749697 (0xa422e2c1)
proposal: ESP-ENCRYPT-DES ESP-AUTH-MD5
sa duration (kilobytes/sec): 1843200/3600
sa remaining duration (kilobytes/sec): 1839310/768
max sent sequence-number: 10837
udp encapsulation used for nat traversal: N
-----------------------------
IPsec policy name: "center"
sequence number: 90
mode: isakmp
-----------------------------
connection id: 198
encapsulation mode: tunnel
perfect forward secrecy: None
tunnel:
local address: x.x.x.x
remote address: x.x.x.x
Flow :
sour addr: 192.168.20.0/255.255.255.0 port: 0 protocol: IP
dest addr: 192.168.90.0/255.255.255.0 port: 0 protocol: IP
[inbound ESP SAs]
spi: 1051300980 (0x3ea99474)
proposal: ESP-ENCRYPT-DES ESP-AUTH-MD5
sa duration (kilobytes/sec): 1843200/3600
sa remaining duration (kilobytes/sec): 1841206/768
max received sequence-number: 21289
anti-replay check enable: Y
anti-replay window size: 32
udp encapsulation used for nat traversal: N
[outbound ESP SAs]
spi: 2753749698 (0xa422e2c2)
proposal: ESP-ENCRYPT-DES ESP-AUTH-MD5
sa duration (kilobytes/sec): 1843200/3600
sa remaining duration (kilobytes/sec): 1842476/768
max sent sequence-number: 14214
udp encapsulation used for nat traversal: N
-----------------------------
IPsec policy name: "center"
sequence number: 90
mode: isakmp
-----------------------------
connection id: 199
encapsulation mode: tunnel
perfect forward secrecy: None
tunnel:
local address: x.x.x.x
remote address: x.x.x.x
Flow :
sour addr: 192.168.40.0/255.255.255.0 port: 0 protocol: IP
dest addr: 192.168.90.0/255.255.255.0 port: 0 protocol: IP
[inbound ESP SAs]
spi: 2005175563 (0x77848d0b)
proposal: ESP-ENCRYPT-DES ESP-AUTH-MD5
sa duration (kilobytes/sec): 1843200/3600
sa remaining duration (kilobytes/sec): 1842861/768
max received sequence-number: 5376
anti-replay check enable: Y
anti-replay window size: 32
udp encapsulation used for nat traversal: N
[outbound ESP SAs]
spi: 2753749696 (0xa422e2c0)
proposal: ESP-ENCRYPT-DES ESP-AUTH-MD5
sa duration (kilobytes/sec): 1843200/3600
sa remaining duration (kilobytes/sec): 1842865/768
max sent sequence-number: 5348
udp encapsulation used for nat traversal: N
[U200-M]
分支深圳的配置(会自动断):
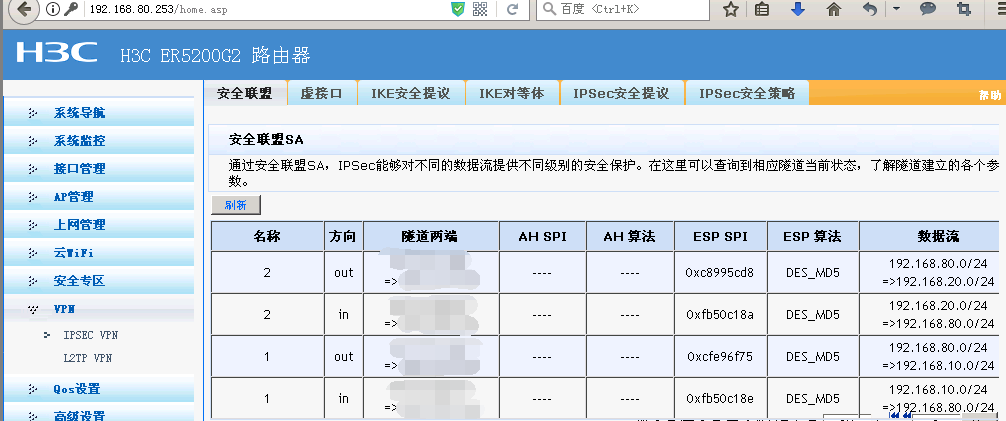
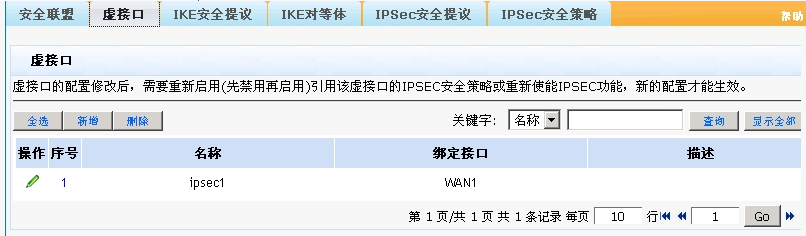
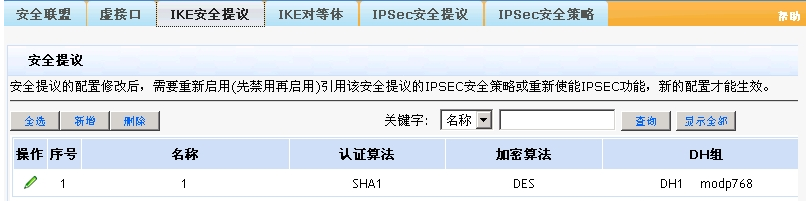
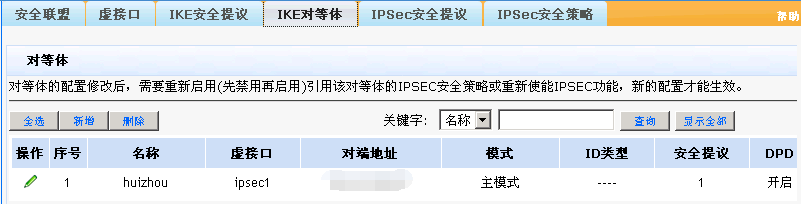
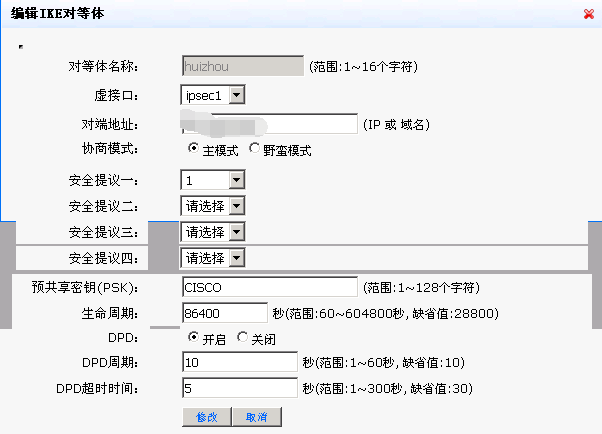
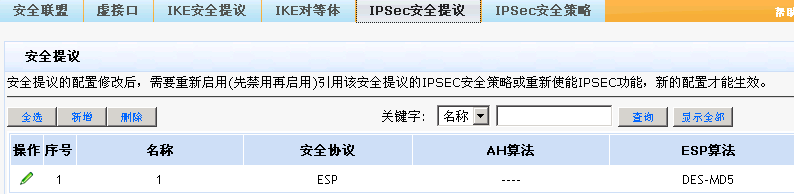
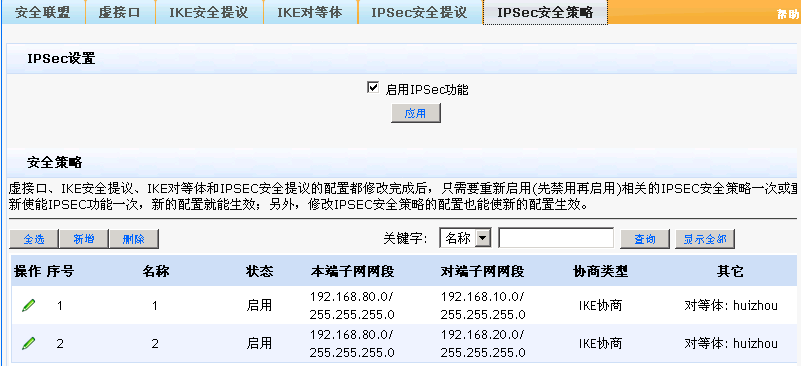
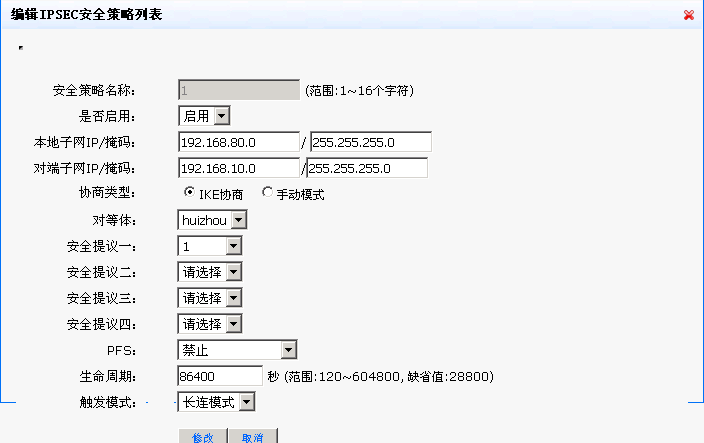
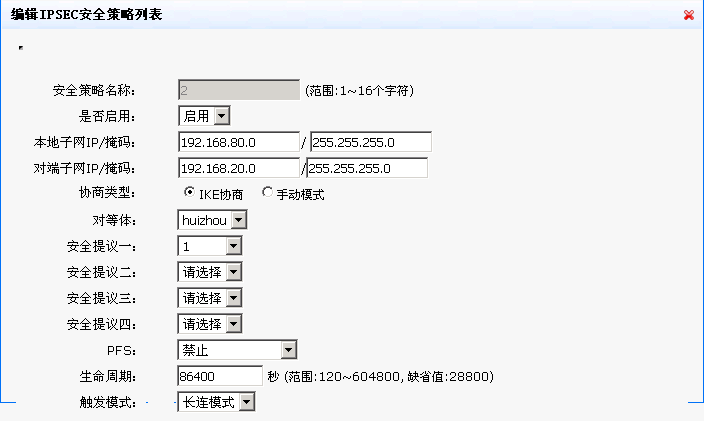
- 2018-06-22提问
- 举报
-
(0)
最佳答案


断的时候,log有日志吗?有没有类似dpd检测失败断开的日志?从配置上看不出来什么问题,这个大概多上时间会复现一次?自己就会好吗?
- 2018-06-22回答
- 评论(1)
- 举报
-
(0)
有日志的,一个是DPD超时,隧道断开,一个是发送PAYLOAD_MALFORMED通告信息,一个是收到IPSEC_RESPONDER_LIFETIME消息载荷;不固定的,大概7、8个小时左右,断的时候丢包8个,丢完包会自动重连成功


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明

有日志的,一个是DPD超时,隧道断开,一个是发送PAYLOAD_MALFORMED通告信息,一个是收到IPSEC_RESPONDER_LIFETIME消息载荷;不固定的,大概7、8个小时左右,断的时候丢包8个,丢完包会自动重连成功