问题描述:
无线控制器web登录控制台无法实现,版本信息是
[WHH_XS_WX_C3510E]dis version
H3C Comware
Platform Software
Comware
Software, Version 5.20, ESS 3702
Copyright
(c) 2004-2013 Hangzhou H3C Tech. Co., Ltd. All rights reserved.
H3C WX3510E
uptime is 8 weeks, 3 days, 6 hours, 56 minutes
H3C WX3510E
with 1 RMI XLR 716 800MHz Processor
2048M bytes
DDR2
4M bytes
Flash Memory
259M bytes
CFCard Memory
Hardware
Version is Ver.B
CPLD Version
is 010
Basic
Bootrom Version is 2.01
Extend
Bootrom Version is 2.01
[Subslot
0]WX3510E Hardware Version is Ver.B
AAA认证也配置了local-user admin
password
cipher $c$3$5bHyuuXF3Sch8R01GK0y684VbjhsjtAlfqpnITU=
authorization-attribute
level 3
service-type
ssh telnet terminal
service-type
portal
service-type
web
请问问题出在哪里?
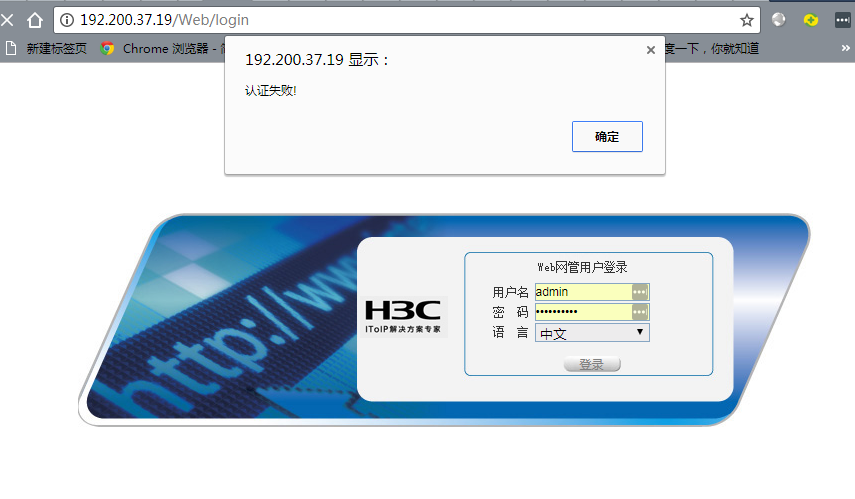
组网及组网描述:
1个AC6个AP组网
- 2017-08-17提问
- 举报
-
(0)
最佳答案

建议升级到最新版本。之前遇到过相同问题,一直提示为认证失败,实际上为该版本不支持使用WEB界面,说白点就是假界面;下载AC升级包时里面会附带相应AP版本,如果现场AP型号不多,可以考虑只将需要的AP型号版本上传上去就行了
- 2017-08-17回答
- 评论(2)
- 举报
-
(0)
非常感谢!抽空我试试!
是不是要先升级AP再升级AC?


升级应该也没啥用
user-interface vty 0 4下加条这个命令authentication-mode scheme试试
- 2017-08-17回答
- 评论(2)
- 举报
-
(0)
domain system authentication default radius-scheme system authorization default radius-scheme system accounting default radius-scheme system authentication portal radius-scheme system authorization portal radius-scheme system accounting portal radius-scheme system 把这里的default改成lan-access和portal吧,default是所有的,本地认证也会送到radius服务器,已经解决!!!!
没用,看来还是要升级版本
domain system authentication default radius-scheme system authorization default radius-scheme system accounting default radius-scheme system authentication portal radius-scheme system authorization portal radius-scheme system accounting portal radius-scheme system 把这里的default改成lan-access和portal吧,default是所有的,本地认证也会送到radius服务器,已经解决!!!!

全局开启ip http enable。能打开页面认证不通过的确认下密码有没有错?可以先建个简单的密码测试。
另外版本也太老了,建议升级最新的R3709P61.
- 2017-08-17回答
- 评论(1)
- 举报
-
(0)
全局已经启用了ip http enable还是不行,telnet就可以,用的同一个密码,升级AC的话AP的版本是不是也要相应升级?
全局已经启用了ip http enable还是不行,telnet就可以,用的同一个密码,升级AC的话AP的版本是不是也要相应升级?

无线控制器有没有做其他的认证,然后把其他认证域改成默认域了?可以尝试用admin@system登录试试。
- 2017-08-17回答
- 评论(1)
- 举报
-
(0)
区分SSID做了802.1X认证和PORTAL认证,按你的方法操作了还是不行。。。。。。。。
区分SSID做了802.1X认证和PORTAL认证,按你的方法操作了还是不行。。。。。。。。


具体配置如下,请各位大神帮忙看看,谢谢!
[WHH_XS_WX_C3510E] dis cur
#
version 5.20, ESS 3702
#
sysname WHH_XS_WX_C3510E
#
clock timezone Beijing add 08:00:00
#
domain default enable system
#
telnet server enable
#
port-security enable
#
dot1x authentication-method eap
#
portal server whh ip 192.200.37.19 url http://192.200.37.19/portal/logon.htm server-type imc
portal free-rule 1 source interface GigabitEthernet1/0/1 destination any
portal free-rule 2 source ip any destination ip 61.153.6.58 mask 255.255.255.255
portal free-rule 3 source ip 61.153.6.58 mask 255.255.255.255 destination ip any
portal free-rule 4 source ip any destination ip 192.200.10.8 mask 255.255.255.255
portal free-rule 5 source ip 192.200.10.8 mask 255.255.255.255 destination ip any
portal local-server http
#
password-recovery enable
#
vlan 1
#
vlan 88
#
radius scheme system
primary authentication 192.200.10.8
primary accounting 192.200.10.8
key authentication cipher $c$3$nYcyd8k2vXIFc9NyzUqmuskiQcyRJffZc+8J9aI=
key accounting cipher $c$3$DSy1PFAC6IBLV4jLxWW3m79/yoNbGtJAjsQ1uSg=
user-name-format without-domain
nas-ip 192.200.37.19
radius scheme imc
#
domain 802.1x
access-limit disable
state active
idle-cut disable
self-service-url disable
domain system
authentication default radius-scheme system
authorization default radius-scheme system
accounting default radius-scheme system
authentication portal radius-scheme system
authorization portal radius-scheme system
accounting portal radius-scheme system
access-limit disable
state active
idle-cut disable
self-service-url disable
#
user-group system
group-attribute allow-guest
#
local-user admin
password cipher $c$3$5bHyuuXF3Sch8R01GK0y684VbjhsjtAlfqpnITU=
authorization-attribute level 3
service-type ssh telnet terminal
service-type portal
service-type web
local-user h3c
password cipher $c$3$dnKSSZqpSpDwUkCtcyWRpWqvxqC6zQ==
service-type portal
local-user xh
password cipher $c$3$teSvJJLjhTmR+GDd/1TmRH0mVKZZk3KMnt46rUA=
service-type telnet terminal
service-type web
#
wlan rrm
dot11a mandatory-rate 6 12 24
dot11a supported-rate 9 18 36 48 54
dot11b mandatory-rate 1 2
dot11b supported-rate 5.5 11
dot11g mandatory-rate 1 2 5.5 11
dot11g supported-rate 6 9 12 18 24 36 48 54
#
wlan service-template 1 crypto
ssid itcitc_QS
bind WLAN-ESS 0
cipher-suite tkip
security-ie rsn
service-template enable
#
wlan service-template 2 clear
ssid itcitc_qiaosi
bind WLAN-ESS 1
service-template enable
#
wlan service-template 3 crypto
ssid itcitc_802.1X
bind WLAN-ESS 3
cipher-suite ccmp
security-ie rsn
service-template enable
#
wlan ap-group default_group
ap itc_1
ap itc_2
ap itc_3
ap itc_4
ap itc_5
ap itc_6
ap itc_7
#
interface NULL0
#
interface Vlan-interface1
ip address 192.200.37.19 255.255.254.0
portal server whh method direct
#
interface Vlan-interface88
description AP_MGT
ip address 172.18.1.10 255.255.255.0
#
interface GigabitEthernet1/0/1
port link-type trunk
port trunk permit vlan 1 88
#
interface GigabitEthernet1/0/2
#
interface GigabitEthernet1/0/3
#
interface GigabitEthernet1/0/4
#
interface Ten-GigabitEthernet1/0/5
#
interface WLAN-ESS0
port-security port-mode psk
port-security tx-key-type 11key
port-security preshared-key pass-phrase cipher $c$3$dorxF2jV5SLr6na3PDj3+FdXM81kxM0OmwCxF2c=
#
interface WLAN-ESS1
port link-type hybrid
port hybrid vlan 1 untagged
#
interface WLAN-ESS3
port-security port-mode userlogin-secure-ext
port-security tx-key-type 11key
#
wlan ap itc_1 model WA2620i-AGN id 1
serial-id 219801A0CMC13B001375
radio 1
radio 2
service-template 1
service-template 2
radio enable
#
wlan ap itc_2 model WA2620i-AGN id 2
serial-id 219801A0CMC13B001367
radio 1
radio 2
service-template 1
service-template 2
radio enable
#
wlan ap itc_3 model WA2620i-AGN id 3
serial-id 219801A0CMC13B001368
radio 1
radio 2
service-template 1
service-template 2
service-template 3
radio enable
#
wlan ap itc_4 model WA2620i-AGN id 4
serial-id 219801A0CMC13B001397
radio 1
radio 2
service-template 1
service-template 2
service-template 3
radio enable
#
wlan ap itc_5 model WA2620i-AGN id 5
serial-id 219801A0CMC13B001392
radio 1
radio 2
service-template 1
service-template 2
radio enable
#
wlan ap itc_6 model WA2620i-AGN id 6
serial-id 219801A0CMC13B001005
radio 1
radio 2
service-template 1
service-template 2
radio enable
#
wlan ap itc_7 model WA2620i-AGN id 7
serial-id 219801A0CMC13B001383
radio 1
radio 2
service-template 1
service-template 2
radio enable
#
wlan ips
malformed-detect-policy default
signature deauth_flood signature-id 1
signature broadcast_deauth_flood signature-id 2
signature disassoc_flood signature-id 3
signature broadcast_disassoc_flood signature-id 4
signature eapol_logoff_flood signature-id 5
signature eap_success_flood signature-id 6
signature eap_failure_flood signature-id 7
signature pspoll_flood signature-id 8
signature cts_flood signature-id 9
signature rts_flood signature-id 10
signature-policy default
countermeasure-policy default
attack-detect-policy default
virtual-security-domain default
attack-detect-policy default
malformed-detect-policy default
signature-policy default
countermeasure-policy default
#
ip route-static 0.0.0.0 0.0.0.0 192.200.37.2
#
undo info-center logfile enable
#
user-interface con 0
user-interface vty 0 4
user privilege level 3
set authentication password cipher $c$3$n2klKvgoY78uUw3+0j0ZcYxX/P8WYsaomkcJvoU=
#
return
[WHH_XS_WX_C3510E]
- 2017-08-17回答
- 评论(2)
- 举报
-
(0)
大神感谢你的指导!!!!!!已经解决
domain system authentication default radius-scheme system authorization default radius-scheme system accounting default radius-scheme system authentication portal radius-scheme system authorization portal radius-scheme system accounting portal radius-scheme system 把这里的default改成lan-access和portal吧,default是所有的,本地认证也会送到radius服务器
大神感谢你的指导!!!!!!已经解决
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明


是不是要先升级AP再升级AC?