问题描述:
客户要求双网一主一备{都搭了vpn隧道},哪个网断了自动切换另一个网,我这边想一台防火墙做双主这样带宽压力减少。
组网及组网描述:

- 2022-12-16提问
- 举报
-
(0)

1.16.6 配置IPsec智能选路
1. 组网需求
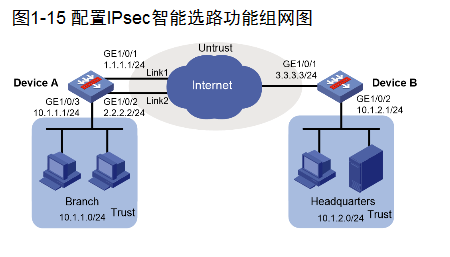
如图1-15所示,企业分支使用IPsec VPN接入企业总部,通过在分支Device A上配置IPsec智能选路功能,实现IPsec隧道在Link 1和Link 2两条链路上动态切换,具体需求如下:
· Device A首先使用Link1与总部建立IPSec隧道。
· 当基于Link1建立的IPSec隧道丢包严重或时延过高时,能自动切换到Link2建立新的IPSec隧道。
2. 组网图
3. 配置分支DeviceA
(1) 配置接口IP地址和网关地址,1.1.1.3和2.2.2.3为本例中的直连下一跳地址,实际使用中请以具体组网情况为准。
<DeviceA> system-view
[DeviceA] interface gigabitethernet 1/0/1
[DeviceA-GigabitEthernet1/0/1] ip address 1.1.1.1 24
[DeviceA-GigabitEthernet1/0/1] gateway 1.1.1.3
[DeviceA-GigabitEthernet1/0/1] quit
[DeviceA] interface gigabitethernet 1/0/2
[DeviceA-GigabitEthernet1/0/2] ip address 2.2.2.2 24
[DeviceA-GigabitEthernet1/0/2] gateway 2.2.2.3
[DeviceA-GigabitEthernet1/0/2] quit
(2) 配置接口加入安全域。
# 请根据组网图中规划的信息,将接口加入对应的安全域,具体配置步骤如下。
[DeviceA] security-zone name trust
[DeviceA-security-zone-Trust] import interface gigabitethernet 1/0/3
[DeviceA-security-zone-Trust] quit
[DeviceA] security-zone name untrust
[DeviceA-security-zone-Untrust] import interface gigabitethernet 1/0/1
[DeviceA-security-zone-Untrust] import interface gigabitethernet 1/0/2
[DeviceA-security-zone-Untrust] quit
(3) 配置安全策略
a. 配置安全策略放行Untrust与Local安全域之间的流量,用于设备之间可以建立IPsec隧道。
# 配置名称为ipseclocalout的安全策规则,使Device A可以向Device B发送IPsec隧道协商报文,具体配置步骤如下。
[DeviceA] security-policy ip
[DeviceA-security-policy-ip] rule name ipseclocalout
[DeviceA-security-policy-ip-1-ipseclocalout] source-zone local
[DeviceA-security-policy-ip-1-ipseclocalout] destination-zone untrust
[DeviceA-security-policy-ip-1-ipseclocalout] source-ip-host 1.1.1.1
[DeviceA-security-policy-ip-1-ipseclocalout] source-ip-host 2.2.2.1
[DeviceA-security-policy-ip-1-ipseclocalout] destination-ip-host 3.3.3.3
[DeviceA-security-policy-ip-1-ipseclocalout] action pass
[DeviceA-security-policy-ip-1-ipseclocalout] quit
# 配置名称为ipseclocalin的安全策略规则,使Device A可以接收和处理来自Device B的IPsec隧道协商报文,具体配置步骤如下。
[DeviceA-security-policy-ip] rule name ipseclocalin
[DeviceA-security-policy-ip-2-ipseclocalin] source-zone untrust
[DeviceA-security-policy-ip-2-ipseclocalin] destination-zone local
[DeviceA-security-policy-ip-2-ipseclocalin] source-ip-host 3.3.3.3
[DeviceA-security-policy-ip-2-ipseclocalin] destination-ip-host 1.1.1.1
[DeviceA-security-policy-ip-2-ipseclocalin] destination-ip-host 2.2.2.2
[DeviceA-security-policy-ip-2-ipseclocalin] action pass
[DeviceA-security-policy-ip-2-ipseclocalin] quit
b. 配置安全策略放行Host A与Host B之间的流量
# 配置名称为trust-untrust的安全策略规则,使Host A访问Host B的报文可通,具体配置步骤如下。
[DeviceA-security-policy-ip] rule name trust-untrust
[DeviceA-security-policy-ip-3-trust-untrust] source-zone trust
[DeviceA-security-policy-ip-3-trust-untrust] destination-zone untrust
[DeviceA-security-policy-ip-3-trust-untrust] source-ip-subnet 10.1.1.0 24
[DeviceA-security-policy-ip-3-trust-untrust] destination-ip-subnet 10.1.2.0 24
[DeviceA-security-policy-ip-3-trust-untrust] action pass
[DeviceA-security-policy-ip-3-trust-untrust] quit
# 配置名称为untrust-trust的安全策略规则,使Host B访问Host A的报文可通,具体配置步骤如下。
[DeviceA-security-policy-ip] rule name untrust-trust
[DeviceA-security-policy-ip-4-untrust-trust] source-zone untrust
[DeviceA-security-policy-ip-4-untrust-trust] destination-zone trust
[DeviceA-security-policy-ip-4-untrust-trust] source-ip-subnet 10.1.2.0 24
[DeviceA-security-policy-ip-4-untrust-trust] destination-ip-subnet 10.1.1.0 24
[DeviceA-security-policy-ip-4-untrust-trust] action pass
[DeviceA-security-policy-ip-4-untrust-trust] quit
[DeviceA-security-policy-ip] quit
(4) 配置IPsec智能选路策略,实现在不同的链路之间选择一条符合质量要求的链路与总部建立IPsec隧道。
[DeviceA] ipsec smart-link policy policy1
[DeviceA-ipsec-smart-link-policy-policy1] link 1 interface gigabitethernet 1/0/1 remote 3.3.3.3
[DeviceA-ipsec-smart-link-policy-policy1] link 2 interface gigabitethernet 1/0/2 remote 3.3.3.3
[DeviceA-ipsec-smart-link-policy-policy1] link-switch cycles 4
[DeviceA-ipsec-smart-link-policy-policy1] smart-link enable
[DeviceA-ipsec-smart-link-policy-policy1] quit
(5) 定义需要保护的数据流
[DeviceA] acl advanced 3000
[DeviceA-acl-ipv4-adv-3000] rule permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0 0.0.0.255
[DeviceA-acl-ipv4-adv-3000] quit
(6) 配置IPsec安全提议,协商封装报文使用的各种安全协议
# 创建IPsec安全提议,两端配置的安全提议参数需要完全相同,具体配置步骤如下。
[DeviceA] ipsec transform-set tran1
[DeviceA-ipsec-transform-set-tran1] encapsulation-mode tunnel
[DeviceA-ipsec-transform-set-tran1] protocol esp
[DeviceA-ipsec-transform-set-tran1] esp encryption-algorithm aes-cbc-128
[DeviceA-ipsec-transform-set-tran1] esp authentication-algorithm sha1
[DeviceA-ipsec-transform-set-tran1] quit
(7) 配置IKE keychain,约定通信双方使用的密钥信息
# 创建并配置IKE keychain,协商双方配置的预共享密钥必须完全相同,具体配置步骤如下。
[DeviceA] ike keychain keychain1
[DeviceA-ike-keychain-keychain1] pre-shared-key address 3.3.3.3 24 key simple 123456
[DeviceA-ike-keychain-keychain1] quit
(8) 配置IKE profile,约定建立IKE SA所需的安全参数
[DeviceA] ike profile profile1
[DeviceA-ike-profile-profile1] keychain keychain1
[DeviceA-ike-profile-profile1] match remote identity address 3.3.3.3 24
[DeviceA-ike-profile-profile1] quit
(9) 配置IPsec安全策略,建立IPsec隧道,保护需要防护的数据流
[DeviceA] ipsec policy policy1 10 isakmp
[DeviceA-ipsec-policy-isakmp-policy1-10] security acl 3000
[DeviceA-ipsec-policy-isakmp-policy1-10] transform-set tran1
[DeviceA-ipsec-policy-isakmp-policy1-10] ike-profile profile1
[DeviceA-ipsec-policy-isakmp-policy1-10] smart-link policy policy1
[DeviceA-ipsec-policy-isakmp-policy1-10] quit
4. 配置总部Device B
(1) 配置接口IP地址和网关地址,3.3.3.4为本例中的直连下一跳地址,实际使用中请以具体组网情况为准。
<DeviceB> system-view
[DeviceB] interface gigabitethernet 1/0/1
[DeviceB-GigabitEthernet1/0/1] ip address 3.3.3.3 24
[DeviceB-GigabitEthernet1/0/1] gateway 3.3.3.4
[DeviceB-GigabitEthernet1/0/1] quit
(2) 配置接口加入安全域。
# 请根据组网图中规划的信息,将接口加入对应的安全域,具体配置步骤如下。
[DeviceB] security-zone name trust
[DeviceB-security-zone-Trust] import interface gigabitethernet 1/0/2
[DeviceB-security-zone-Trust] quit
[DeviceB] security-zone name untrust
[DeviceB-security-zone-Untrust] import interface gigabitethernet 1/0/1
[DeviceB-security-zone-Untrust] quit
(3) 配置安全策略
a. 配置安全策略放行Untrust与Local安全域之间的流量,用于设备之间可以建立IPsec隧道。
# 配置名称为ipseclocalout的安全策规则,使Device B可以向Device A发送IPsec隧道协商报文,具体配置步骤如下。
[DeviceB] security-policy ip
[DeviceB-security-policy-ip] rule name ipseclocalout
[DeviceB-security-policy-ip-1-ipseclocalout] source-zone local
[DeviceB-security-policy-ip-1-ipseclocalout] destination-zone untrust
[DeviceB-security-policy-ip-1-ipseclocalout] source-ip-host 3.3.3.3
[DeviceB-security-policy-ip-1-ipseclocalout] destination-ip-host 1.1.1.1
[DeviceB-security-policy-ip-1-ipseclocalout] destination-ip-host 2.2.2.2
[DeviceB-security-policy-ip-1-ipseclocalout] action pass
[DeviceB-security-policy-ip-1-ipseclocalout] quit
# 配置名称为ipseclocalin的安全策略规则,使Device B可以接收和处理来自Device A的IPsec隧道协商报文,具体配置步骤如下。
[DeviceB-security-policy-ip] rule name ipseclocalin
[DeviceB-security-policy-ip-2-ipseclocalin] source-zone untrust
[DeviceB-security-policy-ip-2-ipseclocalin] destination-zone local
[DeviceB-security-policy-ip-2-ipseclocalin] source-ip-host 1.1.1.1
[DeviceB-security-policy-ip-2-ipseclocalin] source-ip-host 2.2.2.2
[DeviceB-security-policy-ip-2-ipseclocalin] destination-ip-host 3.3.3.3
[DeviceB-security-policy-ip-2-ipseclocalin] action pass
[DeviceB-security-policy-ip-2-ipseclocalin] quit
b. 配置安全策略放行Host A与Host B之间的流量
# 配置名称为trust-untrust的安全策略规则,使Host B访问Host A的报文可通,具体配置步骤如下。
[DeviceB-security-policy-ip] rule name trust-untrust
[DeviceB-security-policy-ip-3-trust-untrust] source-zone trust
[DeviceB-security-policy-ip-3-trust-untrust] destination-zone untrust
[DeviceB-security-policy-ip-3-trust-untrust] source-ip-subnet 10.1.2.0 24
[DeviceB-security-policy-ip-3-trust-untrust] destination-ip-subnet 10.1.1.0 24
[DeviceB-security-policy-ip-3-trust-untrust] action pass
[DeviceB-security-policy-ip-3-trust-untrust] quit
# 配置名称为untrust-trust的安全策略规则,使Host A访问Host B的报文可通,具体配置步骤如下。
[DeviceB-security-policy-ip] rule name untrust-trust
[DeviceB-security-policy-ip-4-untrust-trust] source-zone untrust
[DeviceB-security-policy-ip-4-untrust-trust] destination-zone trust
[DeviceB-security-policy-ip-4-untrust-trust] source-ip-subnet 10.1.1.0 24
[DeviceB-security-policy-ip-4-untrust-trust] destination-ip-subnet 10.1.2.0 24
[DeviceB-security-policy-ip-4-untrust-trust] action pass
[DeviceB-security-policy-ip-4-untrust-trust] quit
[DeviceB-security-policy-ip] quit
(4) 定义需要保护的数据流
[DeviceB] acl advanced 3000
[DeviceB-acl-ipv4-adv-3000] rule permit ip source 10.1.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255
[DeviceB-acl-ipv4-adv-3000] rule permit ip source 3.3.3.0 0.0.0.255 destination 1.1.1.0 0.0.0.255
[DeviceB-acl-ipv4-adv-3000] rule permit ip source 3.3.3.0 0.0.0.255 destination 2.2.2.0 0.0.0.255
[DeviceB-acl-ipv4-adv-3000] quit
(5) 配置IPsec安全提议,协商封装报文使用的各种安全协议
# 创建IPsec安全提议,两端配置的安全提议参数需要完全相同,具体配置步骤如下。
[DeviceB] ipsec transform-set tran1
[DeviceB-ipsec-transform-set-tran1] encapsulation-mode tunnel
[DeviceB-ipsec-transform-set-tran1] protocol esp
[DeviceB-ipsec-transform-set-tran1] esp encryption-algorithm aes-cbc-128
[DeviceB-ipsec-transform-set-tran1] esp authentication-algorithm sha1
[DeviceB-ipsec-transform-set-tran1] quit
(6) 配置IKE keychain,约定通信双方使用的密钥信息
# 创建并配置IKE keychain,协商双方配置的预共享密钥必须完全相同,具体配置步骤如下。
[DeviceB] ike keychain keychain1
[DeviceB-ike-keychain-keychain1] pre-shared-key address 0.0.0.0 0 key simple 123456
[DeviceB-ike-keychain-keychain1] quit
(7) 配置IKE profile,约定建立IKE SA所需的安全参数
[DeviceB] ike profile profile1
[DeviceB-ike-profile-profile1] keychain keychain1
[DeviceB-ike-profile-profile1] match remote identity address 0.0.0.0 0
[DeviceB-ike-profile-profile1] quit
(8) 配置IPsec安全策略模板,用于创建IPsec安全策略
[DeviceB] ipsec policy-template template1 10
[DeviceB-ipsec-policy-template-template1-10] security acl 3000
[DeviceB-ipsec-policy-template-template1-10] transform-set tran1
[DeviceB-ipsec-policy-template-template1-10] local-address 3.3.3.3
[DeviceB-ipsec-policy-template-template1-10] ike-profile profile1
[DeviceB-ipsec-policy-template-template1-10] quit
(9) 引用安全策略模板template1创建一条IKE协商方式的安全策略policy1,建立IPsec隧道,保护需要防护的数据流
[DeviceB] ipsec policy policy1 10 isakmp template template1
(10) 在接口GigabitEthernet1/0/1上应用安全策略policy1,对接口上的流量进行保护
[DeviceB] interface gigabitethernet 1/0/1
[DeviceB-GigabitEthernet1/0/1] ipsec apply policy policy1
[DeviceB-GigabitEthernet1/0/1] quit
5. 验证配置
以上配置完成后,总部Device A和分支Device B之间的IPsec智能选路功能配置完成。
# 可以通过以下显示命令查看Device A上创建的IPsec智能选路策略。
[DeviceA] display ipsec smart-link policy
--------------------------------------------------------------------------
Policy name : policy1
State :Enabled
Probe count :10
Probe interval :1 sec
Probe source IP address :1.1.1.1
Probe destination IP address :3.3.3.3
Max link switch cycles :4
IPsec policy name :policy1
Interface :GigabitEthernet1/0/1
IPsec policy sequence number :10
Link ID Local address Remote address Loss(%) Delay(ms) State
1 1.1.1.1 3.3.3.3 0.0 1.0 Active
2 2.2.2.2 3.3.3.3 25.0 1.0 Inactive
--------------------------------------------------------------------------
# 通过以下显示命令查看IPsec安全策略引用IPsec智能选路策略。
[DeviceA] display ipsec policy
-------------------------------------------
IPsec Policy: policy1
Interface: GigabitEthernet1/0/1
-------------------------------------------
-----------------------------
Sequence number: 10
Mode: ISAKMP
-----------------------------
Traffic Flow Confidentiality: Disabled
Security data flow: 3000
Selector mode: standard
Local address: 1.1.1.1
Remote address: 3.3.3.3
Transform set: tran1
IKE profile: profile1
IKEv2 profile:
smart-link policy: policy1
SA trigger mode: Auto
SA duration(time based): 3600 seconds
SA duration(traffic based): 1843200 kilobytes
SA idle time: 100 seconds
# 通过以下显示命令查看动态生成的ACL规则。
[DeviceA] display acl 3000
Advanced IPv4 ACL 3000, 3 rules,
ACL"s step is 5
rule 0 permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0 0.0.0.255
rule 5 permit ip source 1.1.1.0 0.0.0.255 destination 3.3.3.3 0 (Dynamic) (10 times matched)
# 通过以下显示查看协商生成的IPsec SA。
[DeviceA]display ipsec sa
-------------------------------
Interface: GigabitEthernet1/0/1
-------------------------------
-----------------------------
IPsec policy: policy1
Sequence number: 10
Mode: ISAKMP
-----------------------------
Tunnel id: 0
Encapsulation mode: tunnel
Perfect Forward Secrecy:
Inside VPN:
Extended Sequence Numbers enable: N
Traffic Flow Confidentiality enable: N
Path MTU: 1428
Tunnel:
local address: 1.1.1.1
remote address: 3.3.3.3
Flow:
sour addr: 1.1.1.0/255.255.255.0 port: 0 protocol: ip
dest addr: 3.3.3.3/255.255.255.255 port: 0 protocol: ip
[Inbound ESP SAs]
SPI: 2443816215 (0x91a9ad17)
Connection ID: 38654705665
Transform set: ESP-ENCRYPT-AES-CBC-128 ESP-AUTH-SHA1
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843194/3368
Max received sequence-number: 64
Anti-replay check enable: Y
Anti-replay window size: 64
UDP encapsulation used for NAT traversal: N
Status: Active
[Outbound ESP SAs]
SPI: 4220315517 (0xfb8ce77d)
Connection ID: 38654705664
Transform set: ESP-ENCRYPT-AES-CBC-128 ESP-AUTH-SHA1
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843194/3368
Max sent sequence-number: 64
UDP encapsulation used for NAT traversal: N
Status: Active
- 2022-12-16回答
- 评论(0)
- 举报
-
(0)
暂无评论
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明



暂无评论