问题描述:
防火墙1口绑定vrf连接外网,2口绑定同样vrf连接内网
怎样做nat server使静态地址一对一映射公网地址?
组网及组网描述:
- 2024-01-11提问
- 举报
-
(0)
最佳答案

您好,请知:
可以参考如下案例:
FW上做了静态NAT,并且内外网口都有VPN实例,要实现MSR4通过访问1.1.1.1来实现MSR4访问MSR1的10.0.0.1 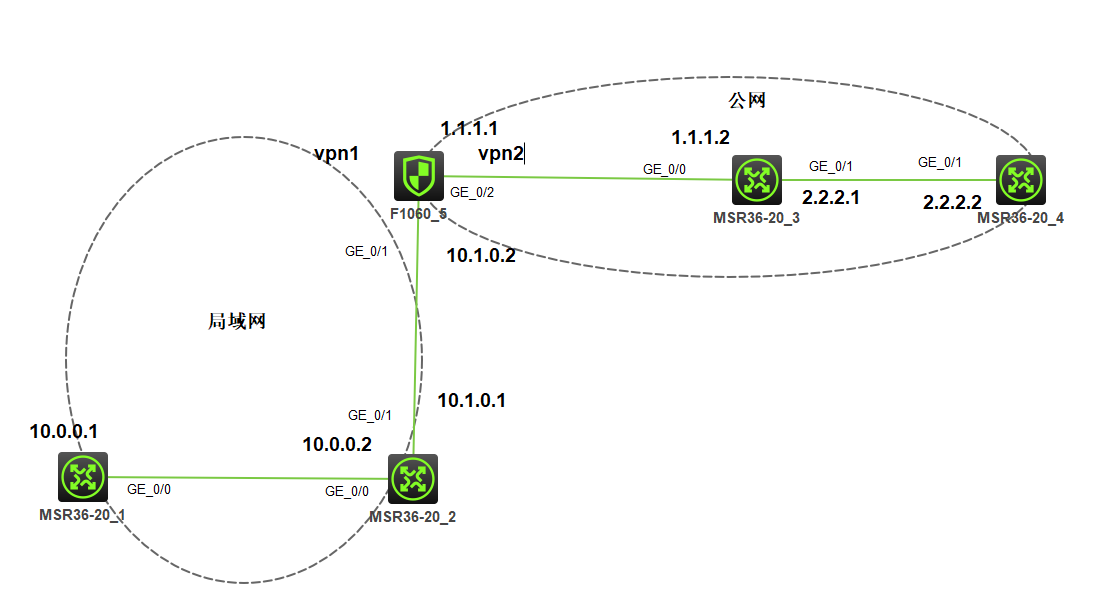
配置步骤
MSR1关键配置:
interface GigabitEthernet0/0
port link-mode route
combo enable copper
ip address 10.0.0.1 255.255.255.0
ip route-static 0.0.0.0 0 10.0.0.2
MSR2关键配置:
interface GigabitEthernet0/0
port link-mode route
combo enable copper
ip address 10.0.0.2 255.255.255.0
interface GigabitEthernet0/1
port link-mode route
combo enable copper
ip address 10.1.0.1 255.255.255.0
ip route-static 0.0.0.0 0 10.1.0.2
FW主要配置:
VPN配置:
ip binding vpn-instance vpn1
ip binding vpn-instance vpn2
接口配置以及静态NAT配置:
interface GigabitEthernet1/0/1
port link-mode route
combo enable copper
ip binding vpn-instance vpn1
ip address 10.1.0.2 255.255.255.0
interface GigabitEthernet1/0/2
port link-mode route
combo enable copper
ip binding vpn-instance vpn2
ip address 1.1.1.1 255.255.255.0
nat static enable
nat static outbound 10.0.0.1 vpn-instance vpn1 1.1.1.1 vpn-instance vpn2
安全域及安全策略配置:
security-zone name Trust
import interface GigabitEthernet1/0/1
security-zone name Untrust
import interface GigabitEthernet1/0/2
security-policy ip
rule 0 name 0
action pass
vrf vpn1
source-zone untrust
destination-zone trust
rule 1 name 1
action pass
vrf vpn2
source-zone untrust
destination-zone trust
路由配置:
ip route-static vpn-instance vpn1 2.2.2.0 24 vpn-instance vpn2 1.1.1.2
ip route-static vpn-instance vpn1 10.0.0.0 24 10.1.0.1
ip route-static vpn-instance vpn2 2.2.2.0 24 1.1.1.2
ip route-static vpn-instance vpn2 10.0.0.0 24 vpn-instance vpn1 10.1.0.1
MSR3关键配置:
interface GigabitEthernet0/0
port link-mode route
combo enable copper
ip address 1.1.1.2 255.255.255.0
interface GigabitEthernet0/1
port link-mode route
combo enable copper
ip address 2.2.2.1 255.255.255.0
MSR4关键配置:
interface GigabitEthernet0/1
port link-mode route
combo enable copper
ip address 2.2.2.2 255.255.255.0
ip route-static 1.1.1.0 24 2.2.2.1
配置关键点
配置关键点,主要是防火墙:
1.安全策略中UNtrust-----trust方向策略 在VRF1与VRF2中都要配置,并且VRF1中,源地址是公网地址,目的地址nat global地址;
在VRF2中,源地址是公网地址,目的地址是nat server 的inside地址
2、跨VPN实例的路由要配置
(1)VPN1中要有到10.0.0.1的路由,并且要有到VPN2目的地址为2.2.2.2的路由
ip route-static vpn-instance vpn1 2.2.2.0 24 vpn-instance vpn2 1.1.1.2
ip route-static vpn-instance vpn1 10.0.0.0 24 10.1.0.1
(2)VPN2中要有2.2.2.0的路由,并且要有到1VPN1目的地址为10.0.0.1的路由
ip route-static vpn-instance vpn2 2.2.2.0 24 1.1.1.2
ip route-static vpn-instance vpn2 10.0.0.0 24 vpn-instance vpn1 10.1.0.1
3、当现场业务不通,进行debug排查的时候,要想看到完整的4条流,下面ACL必须都配置,并且VRF实例不能错误
acl advanced 3000
rule 0 permit ip vpn-instance vpn1 source 10.0.0.1 0
rule 5 permit ip vpn-instance vpn1 source 1.1.1.1 0
rule 10 permit ip vpn-instance vpn2 destination 1.1.1.1 0
rule 20 permit ip vpn-instance vpn1 destination 10.0.0.1 0
- 2024-01-12回答
- 评论(0)
- 举报
-
(0)

按提供的拓扑举例:
在F1090 的GE0/1接口下配置nat server global 117.261.20.4 vpn-instance 1 inside 192.168.1.3 vpn-instance 1
相关路由正常,安全策略放通,需注意针对以上流量安全策略destination-ip 应配置为192.168.1.3。
- 2024-01-12回答
- 评论(0)
- 举报
-
(0)
暂无评论
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明





暂无评论