H3C SR8812-F GRE over IPsec配置实例?
- 0关注
- 0收藏,1066浏览
问题描述:
在该产品相关资料里没有找到GRE over ipsec相关配置实例,能否给一个详细的配置实例?
组网及组网描述:
主站私网161.11.32.0/24,主站路由161.11.32.52,主站GRE接口10.130.21.86,主站GRE公网ip10.8.13.8;子站私网161.11.9.0/28,子站路由161.11.9.6,子站gre接口10.130.21.85,子站gre公网ip10.8.13.7。
- 2024-04-02提问
- 举报
-
(0)

您好,请知:
以下是配置案例,请参考:
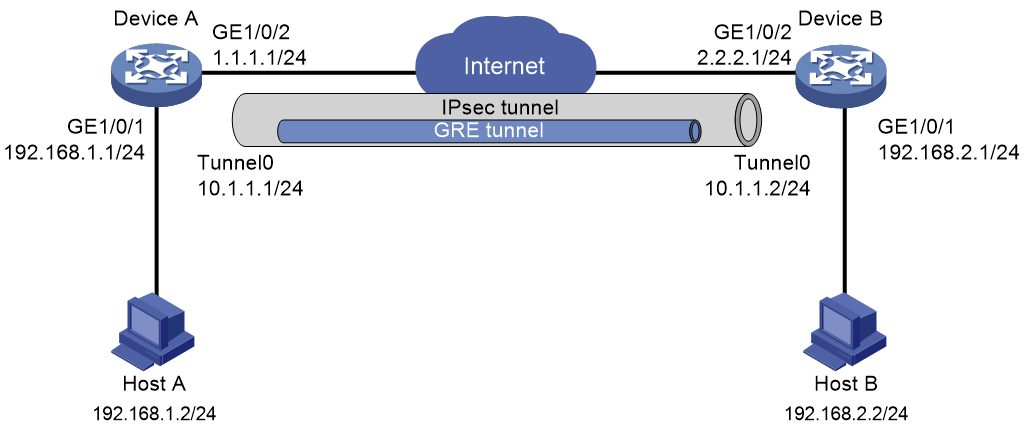
3.1 组网需求
如图3-1所示,Device A和Device B之间通过GRE隧道传输数据,要求对通过GRE隧道的数据进行IPsec加密处理。
3.2 配置思路
· 为了对经GRE封装的数据进行IPsec加密,将IPsec策略应用在物理接口上,访问控制列表源和目的地址为物理接口地址。
· 为了使IPsec保护整个GRE隧道,应用IPsec策略的接口和GRE隧道源、目的接口必须是同一接口。
3.3 配置注意事项
在开始配置之前,请确保Device A的GE1/0/2接口和Device B的GE1/0/2接口之间IPv4报文路由可达。
3.4 配置步骤
3.4.1 Device A的配置
(1) 配置各接口IP地址。
# 配置接口GigabitEthernet1/0/1的IP地址。
<DeviceA> system-view
[DeviceA] interface gigabitethernet 1/0/1
[DeviceA-GigabitEthernet1/0/1] ip address 192.168.1.1 255.255.255.0
[DeviceA-GigabitEthernet1/0/1] quit
# 配置接口GigabitEthernet1/0/2的IP地址。
[DeviceA] interface gigabitethernet 1/0/2
[DeviceA-GigabitEthernet1/0/2] ip address 1.1.1.1 255.255.255.0
[DeviceA-GigabitEthernet1/0/2] quit
(2) 配置GRE隧道。
# 创建Tunnel0接口,并指定隧道模式为GRE over IPv4隧道。
[DeviceA] interface tunnel 0 mode gre
# 配置Tunnel0接口的IP地址为10.1.1.1/24。
[DeviceA-Tunnel0] ip address 10.1.1.1 255.255.255.0
# 配置Tunnel0接口的源端地址为1.1.1.1/24(Device A的GigabitEthernet1/0/2的IP地址)。
[DeviceA-Tunnel0] source 1.1.1.1
# 配置Tunnel0接口的目的端地址为2.2.2.1/24(Device B的GigabitEthernet1/0/2的IP地址)。
[DeviceA-Tunnel0] destination 2.2.2.1
[DeviceA-Tunnel0] quit
(3) 配置ACL。
# 创建ACL3000,定义需要IPsec保护的数据流。
[DeviceA] acl number 3000
[DeviceA-acl-adv-3000] rule 0 permit gre source 1.1.1.1 0 destination 2.2.2.1 0
[DeviceA-acl-adv-3000] quit
(4) 配置静态路由。
# 配置从Device A经过Tunnel0接口到Host B所在子网的静态路由。
[DeviceA] ip route-static 192.168.2.1 255.255.255.0 tunnel 0
(5) 配置IPsec VPN。
# 配置IKE keychain。
[DeviceA] ike keychain keychain1
[DeviceA-ike-keychain-keychain1] pre-shared-key address 2.2.2.1 255.255.255.0 key simple 123456TESTplat&!
[DeviceA-ike-keychain-keychain1] quit
# 配置IPsec安全提议。
[DeviceA] ipsec transform-set tran1
[DeviceA-ipsec-transform-set-tran1] esp encryption-algorithm des
[DeviceA-ipsec-transform-set-tran1] esp authentication-algorithm sha1
[DeviceA-ipsec-transform-set-tran1] quit
# 创建一条IKE协商方式的IPsec安全策略,名称为policy1,序列号为1。
[DeviceA] ipsec policy policy1 1 isakmp
[DeviceA-ipsec-policy-isakmp-policy1-1] security acl 3000
[DeviceA-ipsec-policy-isakmp-policy1-1] remote-address 2.2.2.1
[DeviceA-ipsec-policy-isakmp-policy1-1] transform-set tran1
[DeviceA-ipsec-policy-isakmp-policy1-1] quit
# 在接口GigabitEthernet1/0/2上应用安全策略。
[DeviceA] interface gigabitethernet 1/0/2
[DeviceA-GigabitEthernet1/0/2] ipsec apply policy policy1
[DeviceA-GigabitEthernet1/0/2] quit
3.4.2 Device B的配置
(1) 配置各接口IP地址。
# 配置接口GigabitEthernet1/0/1的IP地址。
<DeviceB> system-view
[DeviceB] interface gigabitethernet 1/0/1
[DeviceB-GigabitEthernet1/0/1] ip address 192.168.2.1 255.255.255.0
[DeviceB-GigabitEthernet1/0/1] quit
# 配置接口GigabitEthernet1/0/2的IP地址。
[DeviceB] interface gigabitethernet 1/0/2
[DeviceB-GigabitEthernet1/0/2] ip address 2.2.2.1 255.255.255.0
[DeviceB-GigabitEthernet1/0/2] quit
(2) 配置GRE隧道。
# 创建Tunnel0接口,并指定隧道模式为GRE over IPv4隧道。
[DeviceB] interface tunnel 0 mode gre
# 配置Tunnel0接口的IP地址为10.1.1.2/24。
[DeviceB-Tunnel0] ip address 10.1.1.2 255.255.255.0
# 配置Tunnel0接口的源端地址为2.2.2.1/24(Device B的GigabitEthernet1/0/2的IP地址)。
[DeviceB-Tunnel0] source 2.2.2.1
# 配置Tunnel0接口的目的端地址为1.1.1.1/24(Device A的GigabitEthernet1/0/2的IP地址)。
[DeviceB-Tunnel0] destination 1.1.1.1
[DeviceB-Tunnel0] quit
(3) 配置静态路由。
# 配置从DeviceB经过Tunnel0接口到Host A所在子网的静态路由。
[DeviceB] ip route-static 192.168.1.1 255.255.255.0 tunnel 0
(4) 创建ACL。
# 创建ACL3000,定义需要IPsec保护的数据流。
[DeviceB] acl number 3000
[DeviceB-acl-adv-3000] rule 0 permit gre source 2.2.2.1 0 destination 1.1.1.1 0
[DeviceB-acl-adv-3000] quit
(5) 配置IPsec VPN。
# 配置IKE keychain。
[DeviceB] ike keychain keychain1
[DeviceB-ike-keychain-keychain1] pre-shared-key address 1.1.1.1 255.255.255.0 key simple 123456TESTplat&!
[DeviceB-ike-keychain-keychain1] quit
# 配置IPsec安全提议。
[DeviceB] ipsec transform-set tran1
[DeviceB-ipsec-transform-set-tran1] esp encryption-algorithm des
[DeviceB-ipsec-transform-set-tran1] esp authentication-algorithm sha1
[DeviceB-ipsec-transform-set-tran1] quit
# 创建一条IKE协商方式的IPsec安全策略,名称为policy1,序列号为1。
[DeviceB] ipsec policy policy1 1 isakmp
[DeviceB-ipsec-policy-isakmp-policy1-1] security acl 3000
[DeviceB-ipsec-policy-isakmp-policy1-1] remote-address 1.1.1.1
[DeviceB-ipsec-policy-isakmp-policy1-1] transform-set tran1
[DeviceB-ipsec-policy-isakmp-policy1-1] quit
# 在接口GigabitEthernet1/0/2上应用安全策略。
[DeviceB] interface gigabitethernet 1/0/2
[DeviceB-GigabitEthernet1/0/2] ipsec apply policy policy1
[DeviceB-GigabitEthernet1/0/2] quit
3.5 验证配置
# 以Host A向Host B发起通信为例,从192.168.1.2 ping 192.168.2.2,会触发IPsec协商,建立IPsec隧道,在成功建立IPsec隧道后,可以ping通。
C:\Users> ping 192.168.2.2
Pinging 192.168.2.2 with 32 bytes of data:
Request timed out.
Reply from 192.168.2.2: bytes=32 time=2ms TTL=254
Reply from 192.168.2.2: bytes=32 time=2ms TTL=254
Reply from 192.168.2.2: bytes=32 time=1ms TTL=254
Ping statistics for 192.168.2.2:
Packets: Sent = 4, Received = 3, Lost = 1 (25% loss),
Approximate round trip times in milli-seconds:
Minimum = 1ms, Maximum = 2ms, Average = 1ms
# 在Device A上使用display ike sa命令,可以看到第一阶段的SA正常建立。
<DeviceA> display ike sa
Connection-ID Remote Flag DOI
------------------------------------------------------------------
2 2.2.2.1 RD IPSEC
Flags:
RD--READY RL--REPLACED FD-FADING
# 在Device A上使用display ipsec sa命令可以看到IPsec SA的建立情况。
<DeviceA> display ipsec sa
-------------------------------
Interface: GigabitEthernet1/0/2
-------------------------------
-----------------------------
IPsec policy: policy1
Sequence number: 1
Mode: isakmp
-----------------------------
Tunnel id: 0
Encapsulation mode: tunnel
Perfect forward secrecy:
Path MTU: 1443
Tunnel:
local address: 1.1.1.1
remote address: 2.2.2.1
Flow:
sour addr: 1.1.1.1/255.255.255.255 port: 0 protocol: gre
dest addr: 2.2.2.1/255.255.255.255 port: 0 protocol: gre
[Inbound ESP SAs]
SPI: 2130348402 (0x7efa8972)
Transform set: ESP-ENCRYPT-DES-CBC ESP-AUTH-SHA1
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843199/3573
Max received sequence-number: 3
Anti-replay check enable: Y
Anti-replay window size: 64
UDP encapsulation used for NAT traversal: N
Status: Active
[Outbound ESP SAs]
SPI: 2811839266 (0xa7994322)
Transform set: ESP-ENCRYPT-DES-CBC ESP-AUTH-SHA1
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843199/3573
Max sent sequence-number: 3
UDP encapsulation used for NAT traversal: N
Status: Active
# 在Device A上通过命令display interface tunnel 0可以查看经过GRE隧道传输的流量情况。
<DeviceA> display interface tunnel 0
Tunnel0
Current state: UP
Line protocol state: UP
Description: Tunnel0 Interface
Bandwidth: 64kbps
Maximum Transmit Unit: 1476
Internet Address is 10.1.1.1/24 Primary
Tunnel source 1.1.1.1, destination 2.2.2.1
Tunnel keepalive disabled
Tunnel TTL 255
Tunnel protocol/transport GRE/IP
GRE key disabled
Checksumming of GRE packets disabled
Output queue - Urgent queuing: Size/Length/Discards 0/100/0
Output queue - Protocol queuing: Size/Length/Discards 0/500/0
Output queue - FIFO queuing: Size/Length/Discards 0/75/0
Last clearing of counters: Never
Last 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Last 300 seconds output rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Input: 43 packets, 3480 bytes, 0 drops
Output: 45 packets, 3740 bytes, 2 drops
# 从Host B向Host A发起通信验证方法相同,此不赘述。
- 2024-04-03回答
- 评论(0)
- 举报
-
(0)
暂无评论

多分支接入的情况下,如果设备支持点到多点GRE隧道,则总部只需要配置一个GRE Tunnle,但是设备不支持此特性的话,只能在总部为每个分支建立一个GRE Tunnle。
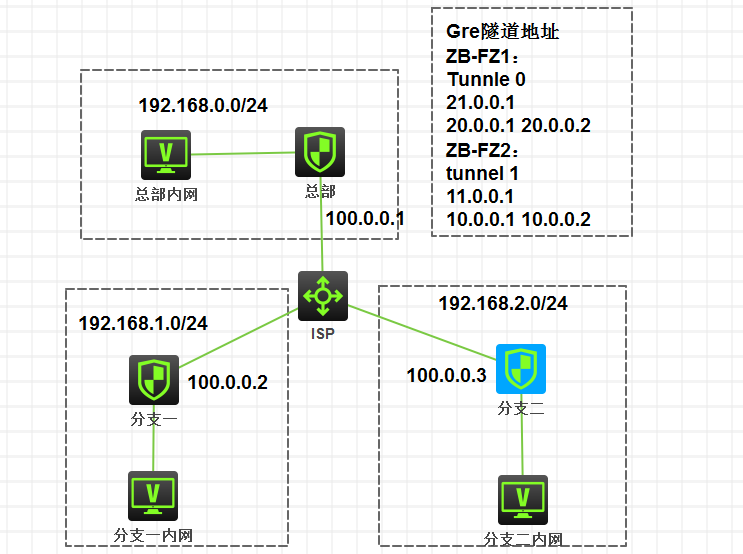
总部:
公网地址:100.0.0.1
私网地址:192.168.0.0/24
GRE tunnel 0:去往分支1
地址:21.0.0.1
封装源地址:20.0.0.1 目的地址:20.0.0.2
GRE tunnel 1:去往分支2
地址:11.0.0.1
封装源地址:10.0.0.1 目的地址:10.0.0.2
分支一:
公网地址:100.0.0.2
私网地址:192.168.1.0/24
GRE tunnel 0:去往总部
地址:21.0.0.2
封装源地址:20.0.0.2 目的地址:20.0.0.1
分支二:
公网地址:100.0.0.2
私网地址:192.168.1.0/24
GRE tunnel 0:去往总部
地址:11.0.0.2
封装源地址:10.0.0.2 目的地址:10.0.0.1
配置步骤
配置基本的IP地址以及域间策略
总部:
interface GigabitEthernet1/0/1
ip address 192.168.0.1 255.255.255.0
#
interface GigabitEthernet1/0/2 #公网口
ip address 100.0.0.1 255.255.255.0
interface LoopBack0 #GRE封装时的源地址
description GRE
ip address 20.0.0.1 255.255.255.255
#
interface LoopBack1 # #GRE封装时的源地址
description GRE
ip address 10.0.0.1 255.255.255.255
interface Tunnel0 mode gre
description ToFenZhi_1
ip address 21.0.0.1 255.255.255.0
source 20.0.0.1
destination 20.0.0.2
#
interface Tunnel1 mode gre
description ToFenZhi_2
ip address 11.0.0.1 255.255.255.0
source 10.0.0.1
destination 10.0.0.2
#域间策略
security-zone name Trust
import interface GigabitEthernet1/0/1
#
security-zone name Untrust
import interface GigabitEthernet1/0/2
import interface Tunnel0
import interface Tunnel1
zone-pair security source Any destination Any
packet-filter 3010
acl advanced 3010
description yujiancelue
rule 0 permit ip
分支一:
interface GigabitEthernet1/0/1
ip address 192.168.1.1 255.255.255.0
#
interface GigabitEthernet1/0/2
ip address 100.0.0.2 255.255.255.0
interface LoopBack0
description GRE
ip address 20.0.0.2 255.255.255.255
interface Tunnel0 mode gre #这里封装的地址源目和总部反过来
ip address 21.0.0.2 255.255.254.0
source 20.0.0.2
destination 20.0.0.1
security-zone name Trust
import interface GigabitEthernet1/0/1
#
security-zone name Untrust
import interface GigabitEthernet1/0/2
import interface Tunnel0
acl advanced 3010
description yujiancelue
rule 0 permit ip
zone-pair security source Local destination Any
packet-filter 3010
分支二:
interface GigabitEthernet1/0/1
ip address 192.168.2.1 255.255.255.0
#
interface GigabitEthernet1/0/2
ip address 100.0.0.3 255.255.255.0
interface LoopBack0
description GRE
ip address 10.0.0.2 255.255.255.255
interface Tunnel0 mode gre
ip address 11.0.0.2 255.255.255.0
source 10.0.0.2
destination 10.0.0.1
security-zone name Trust
import interface GigabitEthernet1/0/1#
security-zone name Untrust
import interface GigabitEthernet1/0/2
import interface Tunnel0
#
acl advanced 3010
description yujiancelue
rule 0 permit ip
#
zone-pair security source Any destination Any
packet-filter 3010
IPsec的配置
总部
#总部使用模板方式建立ipsec,只需要写一个策略,不需要安全acl。
ike keychain 1
pre-shared-key address 0.0.0.0 0.0.0.0 key simple 123 #0.0.0.0代表接受任何地址建立ipsec
ike profile 1
keychain 1
local-identity address 100.0.0.1
match remote identity address 0.0.0.0 0.0.0.0
#
ipsec transform-set 1
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
#
ipsec policy-template 1 1
transform-set 1
local-address 100.0.0.1
ike-profile 1
#
ipsec policy 1 1 isakmp template 1
#接口下调用ipsec
interface GigabitEthernet1/0/2
ip address 100.0.0.1 255.255.255.0
ipsec apply policy 1
最重要的一步:
ip route-static 192.168.1.0 24 Tunnel0 #192.168.1.0是分支一的私网地址,将其下一跳指向Tunnle 0,即去往分支一的GRE隧道。
ip route-static 192.168.2.0 24 Tunnel1 #192.168.1.0是分支二的私网地址,将其下一跳指向Tunnle 0,即去往分支一的GRE隧道。
分支一:
ike profile 1
keychain 1
match remote identity address 100.0.0.1 255.255.255.255
#
ike keychain 1
pre-shared-key address 100.0.0.1 255.255.255.255 key simple 123
ipsec transform-set 1
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
#
ipsec policy 1 1 isakmp
transform-set 1
security acl 3020
remote-address 100.0.0.1
ike-profile 1
acl advanced 3020
description IPsec
rule 0 permit ip source 20.0.0.2 0 destination 20.0.0.1 0 #这里安全ACl匹配的流和GRE的源目地址一致,即由GRE封装之后的报文。
最重要的一步:
ip route-static 192.168.0.0 24 Tunnel0 #不管是去往总部192.168.0.0还是去往其他分支192.168.2.0,下一跳全部指向Tunnle 0,全部指向总部,再由总部转发。
ip route-static 192.168.2.0 24 Tunnel0
分支二:
类似分支一
ipsec transform-set 1
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
#
ipsec policy 1 1 isakmp
transform-set 1
security acl 3020
remote-address 100.0.0.1
ike-profile 1
#
ike profile 1
keychain 1
match remote identity address 100.0.0.1 255.255.255.255
#
ike keychain 1
pre-shared-key address 100.0.0.1 255.255.255.255 key simple 123
acl advanced 3020
description IPsec
rule 0 permit ip source 20.0.0.2 0 destination 20.0.0.1 0
ip route-static 192.168.0.0 24 Tunnel0
ip route-static 192.168.2.0 24 Tunnel0
#
验证效果:
#总部使用模板方式时,只能被动建立IPSEC隧道,不能主动呼叫。
分支一:
[H3C]ping -a 192.168.1.1 192.168.0.1
Ping 192.168.0.1 (192.168.0.1) from 192.168.1.1: 56 data bytes, press CTRL_C to break
56 bytes from 192.168.0.1: icmp_seq=0 ttl=255 time=2.000 ms
56 bytes from 192.168.0.1: icmp_seq=1 ttl=255 time=8.000 ms
56 bytes from 192.168.0.1: icmp_seq=2 ttl=255 time=2.000 ms
56 bytes from 192.168.0.1: icmp_seq=3 ttl=255 time=1.000 ms
56 bytes from 192.168.0.1: icmp_seq=4 ttl=255 time=1.000 ms
--- Ping statistics for 192.168.0.1 ---
5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss
round-trip min/avg/max/std-dev = 1.000/2.800/8.000/2.638 ms
[H3C]%May 9 18:41:03:921 2018 H3C PING/6/PING_STATISTICS: -COntext=1; Ping statistics for 192.168.0.1: 5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss, round-trip min/avg/max/std-dev = 1.000/2.800/8.000/2.638 ms.
[H3C]ping -a 192.168.1.1 192.168.2.1
Ping 192.168.2.1 (192.168.2.1) from 192.168.1.1: 56 data bytes, press CTRL_C to break
56 bytes from 192.168.2.1: icmp_seq=0 ttl=254 time=5.000 ms
56 bytes from 192.168.2.1: icmp_seq=1 ttl=254 time=2.000 ms
56 bytes from 192.168.2.1: icmp_seq=2 ttl=254 time=4.000 ms
56 bytes from 192.168.2.1: icmp_seq=3 ttl=254 time=2.000 ms
56 bytes from 192.168.2.1: icmp_seq=4 ttl=254 time=3.000 ms
--- Ping statistics for 192.168.2.1 ---
5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss
round-trip min/avg/max/std-dev = 2.000/3.200/5.000/1.166 ms
[H3C]%May 9 18:41:07:906 2018 H3C PING/6/PING_STATISTICS: -COntext=1; Ping statistics for 192.168.2.1: 5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss, round-trip min/avg/max/std-dev = 2.000/3.200/5.000/1.166 ms.
分支二:
[H3C]ping -a 192.168.2.1 192.168.0.1
Ping 192.168.0.1 (192.168.0.1) from 192.168.2.1: 56 data bytes, press CTRL_C to break
56 bytes from 192.168.0.1: icmp_seq=0 ttl=255 time=1.000 ms
56 bytes from 192.168.0.1: icmp_seq=1 ttl=255 time=1.000 ms
56 bytes from 192.168.0.1: icmp_seq=2 ttl=255 time=1.000 ms
56 bytes from 192.168.0.1: icmp_seq=3 ttl=255 time=2.000 ms
56 bytes from 192.168.0.1: icmp_seq=4 ttl=255 time=1.000 ms
--- Ping statistics for 192.168.0.1 ---
5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss
round-trip min/avg/max/std-dev = 1.000/1.200/2.000/0.400 ms
[H3C]\%May 9 18:42:47:047 2018 H3C PING/6/PING_STATISTICS: -COntext=1; Ping statistics for 192.168.0.1: 5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss, round-trip min/avg/max/std-dev = 1.000/1.200/2.000/0.400 ms.
[H3C]ping -a 192.168.2.1 192.168.1.1
Ping 192.168.1.1 (192.168.1.1) from 192.168.2.1: 56 data bytes, press CTRL_C to break
56 bytes from 192.168.1.1: icmp_seq=0 ttl=254 time=11.000 ms
56 bytes from 192.168.1.1: icmp_seq=1 ttl=254 time=2.000 ms
56 bytes from 192.168.1.1: icmp_seq=2 ttl=254 time=2.000 ms
56 bytes from 192.168.1.1: icmp_seq=3 ttl=254 time=5.000 ms
56 bytes from 192.168.1.1: icmp_seq=4 ttl=254 time=4.000 ms
--- Ping statistics for 192.168.1.1 ---
5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss
round-trip min/avg/max/std-dev = 2.000/4.800/11.000/3.311 ms
[H3C]%May 9 18:42:50:726 2018 H3C PING/6/PING_STATISTICS: -COntext=1; Ping statistics for 192.168.1.1: 5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss, round-trip min/avg/max/std-dev = 2.000/4.800/11.000/3.311 ms.
配置关键点
一:注意loopback口的建立,和GRE封装时的源目地址保持一致,而不是GRE Tunnle的ip地址。
二:安全策略,Tunnle口需要加入安全域并且放通策略
三:这种方式下的IPSEC,后续网段变动时,只需要配置不同的静态路由指向GRE Tunnle口,IPsec的配置无需改变,适合私网地址较大的拓扑。
四:IPsec的各种加密参数注意保持一致。以及IPsec的安全ACL匹配的是GRE封装之后的源目地址。
五:对于各种访问控制,建议IPsec这块不用动,等IPsec成功后,在防火墙的域间策略上统一控制。
- 2024-04-10回答
- 评论(0)
- 举报
-
(0)
暂无评论
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明




暂无评论