最佳答案

北京某客户需要F1060配置vpn-instance并跨公网与对端防火墙对接IPSEC VPN。
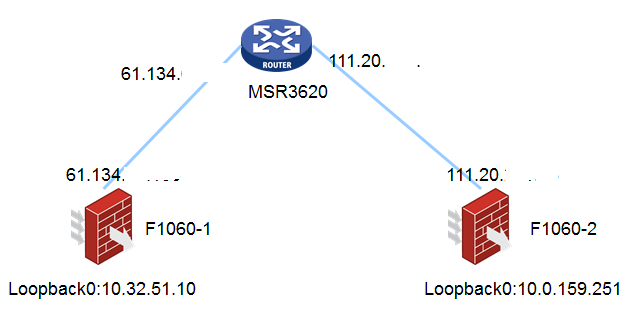
图一:组网拓扑
相关设备的接口ip地址和路由配置略。
F1060-1重要配置:
#
ip vpn-instance dx100
route-distinguisher 400:1
vpn-target 400:1 import-extcommunity
vpn-target 400:1 export-extcommunity
#
nat address-group 4
address 61.134.x.x 61.134.x.x
#
interface LoopBack0
ip binding vpn-instance dx100
ip address 10.32.51.10 255.255.255.255
#
interface GigabitEthernet1/0/19
port link-mode route
description dx100
combo enable copper
duplex full
speed 1000
ip binding vpn-instance dx100
ip address 61.134.x.x 255.255.255.224
nat outbound 3004 address-group 4 vpn-instance dx100
ipsec apply policy ntt
#
object-policy ip Trust-Untrust
rule 0 pass vrf dx
rule 1 pass vrf lt
rule 2 pass vrf vpn
rule 3 pass vrf dx100
rule 4 pass vrf management
#
object-policy ip Untrust-trust
rule 0 pass vrf dx
rule 1 pass vrf lt
rule 2 pass vrf vpn
rule 3 pass vrf dx100
rule 4 pass vrf management
#
security-zone name Trust
import interface LoopBack0
#
security-zone name DMZ
#
security-zone name Untrust
import interface GigabitEthernet1/0/19
#
zone-pair security source Trust destination Untrust
object-policy apply ip Trust-Untrust
#
zone-pair security source Untrust destination Trust
object-policy apply ip Untrust-trust
#
ip route-static vpn-instance dx100 0.0.0.0 0 61.134.x.x
#
acl advanced 3004
description dx100
rule 0 deny ip vpn-instance dx100 source 10.32.5.0 0.0.0.255
rule 1 deny ip vpn-instance dx100 source 10.32.6.0 0.0.0.255
rule 2 deny ip vpn-instance dx100 source 10.32.7.0 0.0.0.255
rule 3 deny ip vpn-instance dx100 source 10.32.1.41 0
rule 4 deny ip vpn-instance dx100 source 10.32.51.10 0 destination 10.0.109.251 0
rule 5 permit ip vpn-instance dx100 source 192.168.29.10 0
rule 6 permit ip vpn-instance dx100 source 192.168.29.11 0
rule 7 permit ip vpn-instance dx100 source 1.1.1.0 0.0.0.255
rule 9 permit ip vpn-instance dx100 source 10.100.0.0 0.0.255.255
rule 15 permit ip vpn-instance dx100 source 172.21.252.0 0.0.0.255
rule 20 permit ip vpn-instance dx100 source 172.21.253.0 0.0.0.255
rule 25 permit ip vpn-instance dx100 source 192.168.253.0 0.0.0.255
rule 30 permit ip vpn-instance dx100 source 172.21.1.24 0
rule 35 permit ip vpn-instance dx100 source 10.32.0.0 0.0.255.255
rule 40 permit ip vpn-instance dx100 source 172.21.1.250 0
rule 45 permit ip vpn-instance dx100 source 172.21.1.248 0
rule 50 permit ip vpn-instance dx100 source 192.168.0.0 0.0.0.255
#
acl advanced 3020
description to ipsec
rule 20 permit ip vpn-instance dx100 source 10.32.51.10 0 destination 10.0.109.251 0
#
ipsec transform-set ntt
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
#
ipsec policy ntt 1 isakmp
transform-set ntt
security acl 3020
local-address 61.134.x.x
remote-address 111.20.x.x
ike-profile ntt
#
ike profile ntt
keychain ntt
dpd interval 5 on-demand
local-identity address 61.134.x.x
match remote identity address 111.20.x.x 255.255.255.248 vpn-instance dx100
proposal 2
#
ike proposal 2
#
ike keychain ntt vpn-instance dx100
pre-shared-key address 111.20.x.x 255.255.255.255 key cipher $c$3$7X4X7l8XgC90/R3l1zUac0pcTsjW4g==
F1060-2配置:
interface LoopBack0
ip address 10.0.109.251 255.255.255.255
#
interface GigabitEthernet1/0/9
port link-mode route
description to LT
combo enable copper
ip address 111.20.x.x 255.255.255.248
nat outbound 3000 address-group 1
ipsec apply policy ntt
#
object-policy ip Trust-Untrust
rule 0 pass
#
object-policy ip Untrust-Trust
rule 0 pass
#
security-zone name Trust
import interface LoopBack0
#
security-zone name Untrust
import interface GigabitEthernet1/0/9
#
zone-pair security source Trust destination Untrust
object-policy apply ip Trust-Untrust
#
zone-pair security source Untrust destination Trust
object-policy apply ip Untrust-Trust
#
ip route-static 0.0.0.0 0 111.20.x.x
#
acl advanced 3000
rule 2 deny ip source 10.0.109.251 0 destination 10.32.51.0 0.0.0.255
rule 4 deny ip source 10.0.109.251 0 destination 10.21.100.32 0
rule 6 deny ip source 10.0.109.251 0 destination 10.21.100.95 0
rule 8 deny ip source 10.0.109.251 0 destination 10.21.100.91 0
rule 20 permit ip
#
acl advanced 3010
rule 10 permit ip source 10.0.109.251 0 destination 10.32.51.10 0
rule 20 permit ip source 10.0.109.251 0 destination 10.21.100.32 0
rule 30 permit ip source 10.0.109.251 0 destination 10.21.100.91 0
rule 40 permit ip source 10.0.109.251 0 destination 10.21.100.95 0
#
ipsec transform-set ntt
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
#
ipsec transform-set zjm
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
#
ipsec policy 1 10 isakmp template ipsec
#
ipsec policy ntt 1 isakmp
transform-set ntt
security acl 3010
local-address 111.20.x.x
remote-address 61.134.x.x
ike-profile ntt
#
ike profile ntt
keychain ntt
dpd interval 5 on-demand
local-identity address 111.20.x.x
match remote identity address 61.134.x.x 255.255.255.224
proposal 2
#
ike keychain ntt
pre-shared-key address 61.134.x.x 255.255.255.255 key cipher $c$3$7REqNgpfKN60YGuJwReO4LykA00UMw==
#
验证结果:
<H3C>ping -a 10.32.51.10 -vpn-instance dx100 10.0.109.251
Ping 10.0.109.251 (10.0.109.251) from 10.32.51.10: 56 data bytes, press CTRL_C to break
56 bytes from 10.0.109.251: icmp_seq=0 ttl=255 time=9.000 ms
56 bytes from 10.0.109.251: icmp_seq=1 ttl=255 time=3.000 ms
56 bytes from 10.0.109.251: icmp_seq=2 ttl=255 time=2.000 ms
56 bytes from 10.0.109.251: icmp_seq=3 ttl=255 time=3.000 ms
56 bytes from 10.0.109.251: icmp_seq=4 ttl=255 time=2.000 ms
--- Ping statistics for 10.0.109.251 in VPN instance dx100 ---
5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss
round-trip min/avg/max/std-dev = 2.000/3.800/9.000/2.638 ms
<H3C> dis ipsec sa
-------------------------------
Interface: GigabitEthernet1/0/19
-------------------------------
-----------------------------
IPsec policy: ntt
Sequence number: 1
Mode: ISAKMP
-----------------------------
Tunnel id: 0
Encapsulation mode: tunnel
Perfect Forward Secrecy:
Inside VPN: dx100
Extended Sequence Numbers enable: N
Traffic Flow Confidentiality enable: N
Path MTU: 1444
Tunnel:
local address: 61.134.x.x
remote address: 111.20.x.x
Flow:
sour addr: 10.32.51.10/255.255.255.255 port: 0 protocol: ip
dest addr: 10.0.109.251/255.255.255.255 port: 0 protocol: ip
[Inbound ESP SAs]
SPI: 246074279 (0x0eaacba7)
Connection ID: 4294967296
Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843199/3527
Max received sequence-number: 9
Anti-replay check enable: Y
Anti-replay window size: 64
UDP encapsulation used for NAT traversal: N
Status: Active
[Outbound ESP SAs]
SPI: 2249709047 (0x8617d5f7)
Connection ID: 4294967297
Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843199/3527
Max sent sequence-number: 9
UDP encapsulation used for NAT traversal: N
Status: Active
<H3C> dis ike sa
Connection-ID Remote Flag DOI
-----------------------------------------------------------
1 111.20.x.x RD IPsec
Flags:
RD--READY RL--REPLACED FD-FADING RK-REKEY
1、ike profile中 match remote address 要绑定vpn-instance
2、ike keychain也要绑定vpn
- 2020-06-16回答
- 评论(0)
- 举报
-
(0)

您好,请知:
1、可参考如下PPPOE的配置命令:
[H3C]sysname PPPOE
[PPPOE]acl basic 2000
[PPPOE-acl-ipv4-basic-2000]rule 0 permit source any
[PPPOE-acl-ipv4-basic-2000]quit
[PPPOE]int gi 0/1
[PPPOE-GigabitEthernet0/1]des
[PPPOE-GigabitEthernet0/1]ip address 202.1.100.2 30
[PPPOE-GigabitEthernet0/1]nat outbound 2000
[PPPOE-GigabitEthernet0/1]quit
[PPPOE]ip route-static 0.0.0.0 0.0.0.0 202.1.100.1
[PPPOE]
PPPOE拨号关键配置点:
[PPPOE]local-user weijianing class network //创建用户名、密码,赋予PPP登陆的权限
New local user added.
[PPPOE-luser-network-weijianing]password simple weijianing
[PPPOE-luser-network-weijianing]service-type ppp
[PPPOE-luser-network-weijianing]quit
[PPPOE]domain name system //配置域,验证方式为本地PPP认证
[PPPOE-isp-system]authentication ppp local
[PPPOE-isp-system]quit
[PPPOE]ip pool weijianing 192.168.10.2 192.168.10.100 //创建地址池,用于PPPOE客户端拨号的IP地址分配
[PPPOE]int Virtual-Template 1 //创建虚拟模板,调用域和地址池
[PPPOE-Virtual-Template1]ip address 192.168.10.1 255.255.255.0
[PPPOE-Virtual-Template1]ppp authentication-mode pap domain system
[PPPOE-Virtual-Template1]remote address pool weijianing
[PPPOE-Virtual-Template1]quit
[PPPOE]int gi 0/0
[PPPOE-GigabitEthernet0/0]pppoe-server bind virtual-template 1 //将PPPOE与虚拟模板绑定到物理接口
[PPPOE-GigabitEthernet0/0]quit
2、以下是具体的案例连接,里面包含详细的配置过程及测试效果:
https://zhiliao.h3c.com/theme/details/101879
3、以下是Ipsec的典型组网配置案例,请参考:
如下是ipsec + IKE预共享密钥:
https://zhiliao.h3c.com/theme/details/102865
如下是Ipsec+IKE野蛮模式:
- 2020-06-16回答
- 评论(0)
- 举报
-
(0)
暂无评论
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明




暂无评论