F100-C-G 的VLAN 70 掩码从 24 改为 23后,网络全部VLAN网络很慢
- 0关注
- 1收藏,2190浏览
问题描述:
问题: 我这边的一个 VLAN 需要接入 超过 254 个无线终端,10个 AP由同一个 AC管理。于是我昨天把原来的VLAN VLAN 60 删除了,把 70 的掩码 由24改为 23,修改后的配置如下,今天的所有VLAN网络异常卡顿,常用的百度、京东甚至打不开,求解,我的
#
version 5.20, Release 5142P02
#
sysname ds_F100
#
clock timezone UTC add 00:00:00
#
l2tp enable
#
undo voice vlan mac-address 00e0-bb00-0000
#
interzone policy default by-priority
#
ip pool 1 172.18.10.2 172.18.10.254
#
domain default enable system
#
dns resolve
dns proxy enable
#
telnet server enable
#
qos carl 5 destination-ip-address subnet 172.18.5.0 24 per-address
qos carl 6 destination-ip-address subnet 172.18.6.0 24 per-address
qos carl 7 destination-ip-address subnet 172.18.7.0 24 per-address
qos carl 8 destination-ip-address subnet 172.18.8.0 24 per-address
qos carl 12 destination-ip-address subnet 172.18.12.0 24 per-address
qos carl 13 destination-ip-address subnet 172.18.13.0 24 per-address
qos carl 20 destination-ip-address range 172.18.5.209 to 172.18.5.210 per-address
qos carl 21 destination-ip-address range 172.18.5.211 to 172.18.5.212 per-address
qos carl 22 destination-ip-address range 172.18.5.213 to 172.18.5.254 per-address
qos carl 51 destination-ip-address range 172.18.5.2 to 172.18.5.206 per-address
qos carl 52 destination-ip-address range 172.18.5.207 to 172.18.5.208 per-address
qos carl 103 destination-ip-address range 172.18.5.2 to 172.18.5.103 per-address
qos carl 104 destination-ip-address range 172.18.5.104 to 172.18.5.105
qos carl 106 destination-ip-address range 172.18.5.106 to 172.18.5.206 per-address
#
port-security enable
#
undo alg dns
undo alg rtsp
undo alg h323
undo alg sip
undo alg sqlnet
undo alg ils
undo alg nbt
undo alg msn
undo alg qq
undo alg tftp
undo alg sccp
undo alg gtp
#
session synchronization enable
#
password-recovery enable
#
acl number 2000 match-order auto
rule 2 permit source 172.18.4.0 0.0.0.255
rule 3 permit source 172.18.5.0 0.0.0.255
rule 4 permit source 172.18.6.0 0.0.0.255
rule 5 permit source 172.18.7.0 0.0.0.255
rule 6 permit source 172.18.8.0 0.0.0.255
rule 7 permit source 172.18.11.0 0.0.0.255
rule 8 permit source 172.18.12.0 0.0.0.255
rule 9 permit source 172.18.13.0 0.0.0.255
rule 10 permit source 172.18.14.0 0.0.0.255
rule 11 permit source 172.18.3.0 0.0.0.255
rule 15 permit source 172.18.18.0 0.0.0.255
#
vlan 1
pki domain datastory
ca identifier CA Server
certificate request from ca
certificate request entity datastory
#
pki domain datastoryca
ca identifier CA Server
certificate request from ra
certificate request entity datastory
root-certificate fingerprint sha1 4DC243
#
pki domain default
crl check disable
#
qos policy ceshi003
#
dhcp server ip-pool vlan120
network 172.18.12.0 mask 255.255.255.0
gateway-list 172.18.12.1
dns-list 192.168.1.2
expired day 0 hour 4
#
dhcp server ip-pool vlan130
network 172.18.13.0 mask 255.255.255.0
gateway-list 172.18.13.1
dns-list 192.168.1.2
expired day 0 hour 3
#
dhcp server ip-pool vlan180
network 172.18.18.0 mask 255.255.255.0
gateway-list 172.18.18.1
dns-list 192.168.1.2
expired day 0 hour 1
#
dhcp server ip-pool vlan50
network 172.18.5.0 mask 255.255.255.0
gateway-list 172.18.5.1
dns-list 192.168.1.2
#
dhcp server ip-pool vlan70
network 172.18.6.0 mask 255.255.254.0
gateway-list 172.18.7.1
dns-list 192.168.1.2
expired day 0 hour 1 minute 30
#
dhcp server ip-pool vlan80
network 172.18.8.0 mask 255.255.255.0
gateway-list 172.18.8.1
dns-list 192.168.1.2
#
policy-based-route 2000 permit node 10
if-match acl 2000
apply ip-address next-hop 192.168.1.3
#
user-group system
group-attribute allow-guest
#
local-user admin
password ci
authorization-attribute level 3
service-type telnet
service-type web
local-user u8user
password cipher $
service-type ppp
local-user vpnuser
password cipher $
service-type ppp
#
stp max-hops 30
stp bpdu-protection
stp enable
#
ssl server-policy access-policy
pki-domain datastory
#
cwmp
undo cwmp enable
#
interface NULL0
#
interface Vlan-interface1
ip policy-based-route 2000
#
interface GigabitEthernet0/1
port link-mode route
nat outbound 2000
ip address 192.168.1.3 255.255.255.0
qos car inbound carl 13 cir 30000 cbs 64000 ebs 0 green pass red discard
qos car inbound carl 14 cir 10000 cbs 64000 ebs 0 green pass red discard
qos car inbound carl 52 cir 20000 cbs 64000 ebs 0 green pass red discard
qos car inbound carl 8 cir 60000 cbs 64000 ebs 0 green pass red discard
qos car inbound carl 103 cir 10000 cbs 625000 ebs 0 green pass red discard
qos car inbound carl 104 cir 40000 cbs 2500000 ebs 0 green pass red discard
qos car inbound carl 106 cir 10000 cbs 625000 ebs 0 green pass red discard
qos car inbound carl 21 cir 40000 cbs 2500000 ebs 0 green pass red discard
qos car inbound carl 6 cir 40000 cbs 3750000 ebs 0 green pass red discard
qos car inbound carl 12 cir 40000 cbs 625000 ebs 0 green pass red discard
#
interface GigabitEthernet0/2
port link-mode route
ip address XXXXXXXXXXX
#
interface GigabitEthernet0/3
port link-mode route
#
interface GigabitEthernet0/3.1
vlan-type dot1q vid 140
ip address 172.18.14.1 255.255.255.0
#
interface GigabitEthernet0/4
port link-mode route
#
interface GigabitEthernet0/4.3
vlan-type dot1q vid 50
ip address 172.18.5.1 255.255.255.0
#
interface GigabitEthernet0/4.5
vlan-type dot1q vid 70
ip address 172.18.7.1 255.255.254.0
#
interface GigabitEthernet0/4.6
vlan-type dot1q vid 80
ip address 172.18.8.1 255.255.255.0
#
interface GigabitEthernet0/4.8
vlan-type dot1q vid 120
ip address 172.18.12.1 255.255.255.0
#
interface GigabitEthernet0/4.9
vlan-type dot1q vid 130
ip address 172.18.13.1 255.255.255.0
#
interface GigabitEthernet0/4.15
vlan-type dot1q vid 180
ip address 172.18.18.1 255.255.255.0
#
vd Root id 1
#
zone name Management id 0
priority 100
import interface GigabitEthernet0/0
zone name Local id 1
priority 100
zone name Trust id 2
priority 85
import interface GigabitEthernet0/3
import interface GigabitEthernet0/3.1
import interface GigabitEthernet0/4
import interface GigabitEthernet0/4.3
import interface GigabitEthernet0/4.5
import interface GigabitEthernet0/4.6
import interface GigabitEthernet0/4.8
import interface GigabitEthernet0/4.9
import interface GigabitEthernet0/4.15
import interface Virtual-Template0
zone name DMZ id 3
priority 50
zone name Untrust id 4
priority 5
import interface GigabitEthernet0/1
import interface GigabitEthernet0/2
switchto vd Root
object service wannacry01
description 阻止比特币病毒
service tcp destination-port 445
object service wannacry02
service tcp destination-port 135
object service wannacry03
service tcp destination-port 137
object service wannacry04
service tcp destination-port 139
zone name Management id 0
ip virtual-reassembly
zone name Local id 1
ip virtual-reassembly
zone name Trust id 2
ip virtual-reassembly
zone name DMZ id 3
ip virtual-reassembly
zone name Untrust id 4
ip virtual-reassembly
interzone source Trust destination Trust
rule 0 permit logging
source-ip any_address
destination-ip any_address
service any_service
rule enable
interzone source Untrust destination Trust
rule 2 deny
source-ip any_address
destination-ip any_address
service wannacry01
service wannacry02
service wannacry03
service wannacry04
rule enable
rule 0 permit logging
source-ip any_address
destination-ip any_address
service any_service
rule enable
#
ssl-vpn server-policy access-policy
ssl-vpn enable
#
ip route-static 0.0.0.0 0.0.0.0 192.168.1.2
#
dhcp enable
#
load xml-configuration
#
load tr069-configuration
#
user-interface con 0
user-interface vty 0 4
authentication-mode scheme
#
return
组网及组网描述:
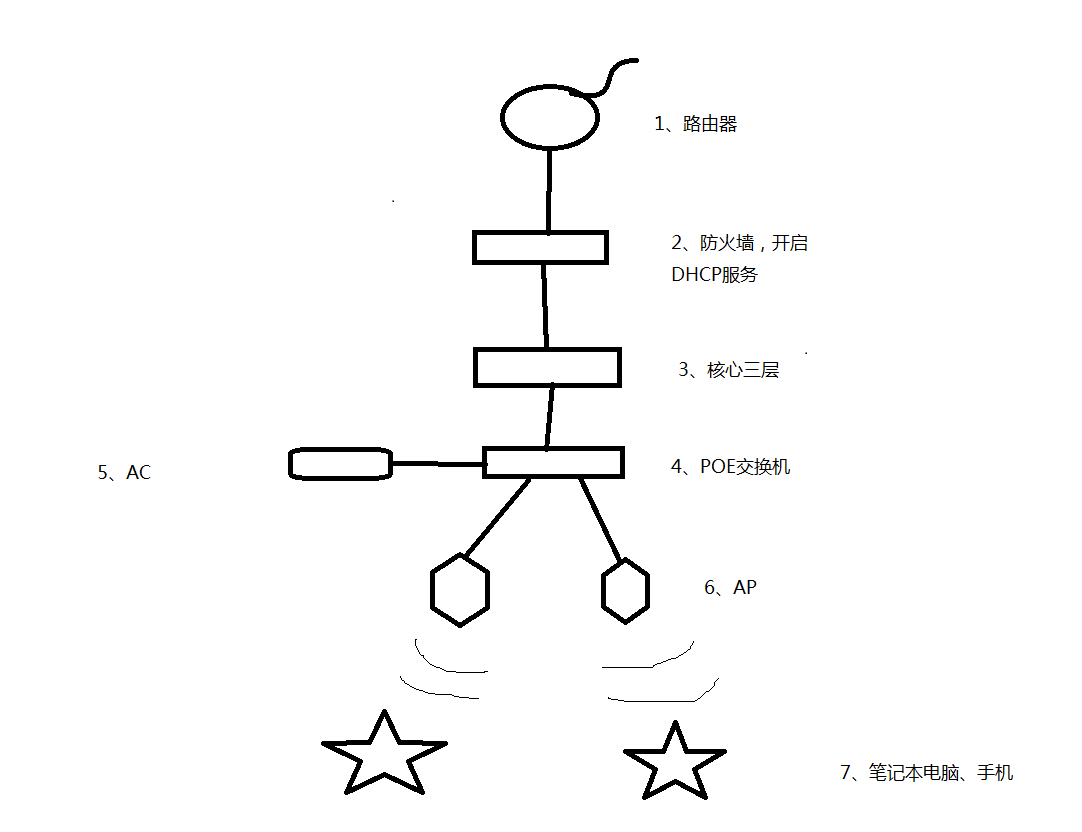
- 2018-09-18提问
- 举报
-
(0)
最佳答案

把qos去掉试试?cpu高吗?不排除是性能不够了。ping丢包吗?丢包估计性能问题问400吧,如果只有网页卡可以修改下tcp mss试试
- 2018-09-18回答
- 评论(1)
- 举报
-
(0)
CPU 1% ,内存 29% ,温度 47 度,没有满负载的吧,之前都好好的,就是昨天我把 VLAN60删除了,把VLAN70的掩码由 24改为 23后,原来V少部分的 VLAN 60 的打印机、台式机都连接到 VLAN 70上。今天中午开始,就很卡了,全公司的台式机、笔记本都上网很慢,网页经常打不开。首先想请教一下,我这样设置的VLAN 70 ,得到的500个IP ,有没有问题


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明




CPU 1% ,内存 29% ,温度 47 度,没有满负载的吧,之前都好好的,就是昨天我把 VLAN60删除了,把VLAN70的掩码由 24改为 23后,原来V少部分的 VLAN 60 的打印机、台式机都连接到 VLAN 70上。今天中午开始,就很卡了,全公司的台式机、笔记本都上网很慢,网页经常打不开。首先想请教一下,我这样设置的VLAN 70 ,得到的500个IP ,有没有问题